Complete Guide to Cybersecurity for Small Businesses
eSecurity Planet
OCTOBER 15, 2024
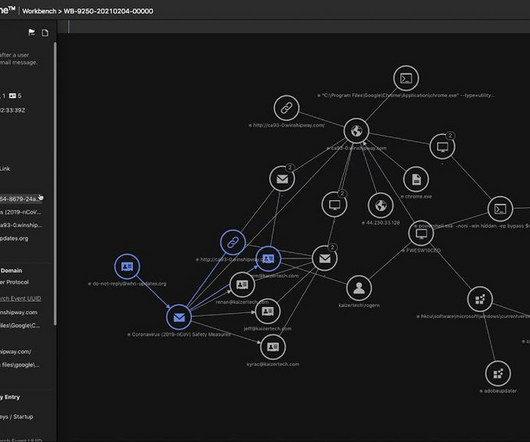
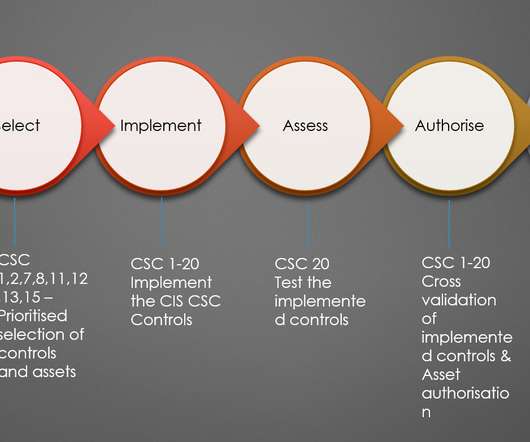
Are you prepared to defend against the rising tide of cyber threats? If you’re a small business owner, it’s crucial to understand the significance of cybersecurity and the steps needed to safeguard your data, customers, and company reputation.












































Let's personalize your content