New Report “State of Cloud Threat Detection and Response”
Anton on Security
MARCH 6, 2023
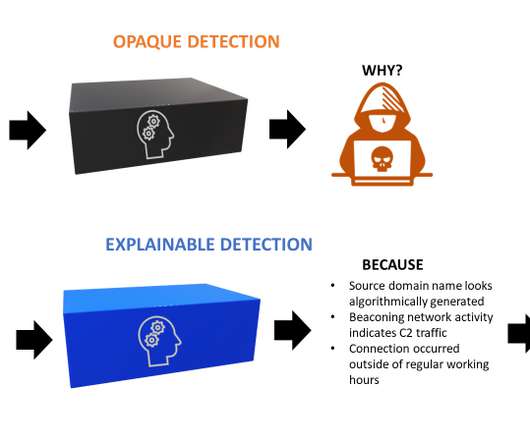
Cloud D&R Report (2023) One of the mysteries of detection and response (D&R) is about how companies really approach D&R in the public cloud. Cloud: Risk or Benefit? Many respondents (more technologists than leaders, mind you) still think that “cloud is hard” and/or also believe in some form of “cloud is a risk” sentiment.
















Let's personalize your content