Over-the-Air Vulnerabilities in Advantech EKI Access Points Put Industrial Networks at Risk
Penetration Testing
NOVEMBER 30, 2024
Industrial environments are increasingly relying on wireless technologies to power critical operations.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Penetration Testing
NOVEMBER 30, 2024
Industrial environments are increasingly relying on wireless technologies to power critical operations.
Cisco Security
SEPTEMBER 22, 2021
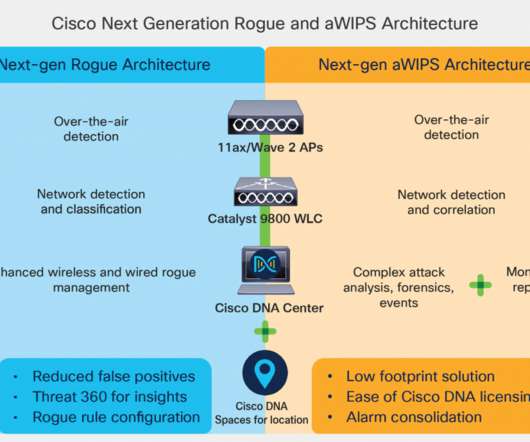
As each day passes, wireless security becomes even more critical to the day-to-day operations of organizations. With the introduction of Wi-Fi 6, many organizations are shifting from a primarily wired infrastructure to one that focuses on worker mobility through wireless connectivity. The Challenges of Wireless Security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
AUGUST 4, 2021
By releasing an information sheet that provides guidance on securing wireless devices while in public (pdf) —for National Security System, Department of Defense, and Defense Industrial Base teleworkers—the NSA has provided useful information on malicious techniques used by cyber actors, and ways to protect against them.

The Hacker News
FEBRUARY 9, 2023
A set of 38 security vulnerabilities has been uncovered in wireless industrial internet of things (IIoT) devices from four different vendors that could pose a significant attack surface for threat actors looking to exploit operational technology (OT) environments.

CyberSecurity Insiders
APRIL 16, 2021
Internet of Medical Things (IoMT) products refer to a combination of medical applications and devices connected to healthcare information technology systems through an online computer network or a wireless network. Therefore, one must understand the risk level of a medical device and its intended… Posted by: Carnell Council.

eSecurity Planet
MARCH 1, 2023
Wireless security is the protection of wireless networks, devices and data from unwanted access and breaches. It involves a variety of strategies and practices designed to preserve the confidentiality, integrity and availability of wireless networks and their resources. What is Wireless Security?

SecureWorld News
FEBRUARY 10, 2023
One technology that has raised particular concerns is personal Bluetooth Low Energy (BLE) trackers. On the other hand, they can be exploited by stalkers, thieves, and other criminals to carry out their illegal activities with little to no risk of getting caught. Learn more about BlueSleuth-Lite on its Kickstarter page here.

Krebs on Security
AUGUST 3, 2020
The Blacklist Alliance provides technologies and services to marketing firms concerned about lawsuits under the Telephone Consumer Protection Act (TCPA), a 1991 law that restricts the making of telemarketing calls through the use of automatic telephone dialing systems and artificial or prerecorded voice messages.
eSecurity Planet
NOVEMBER 1, 2021
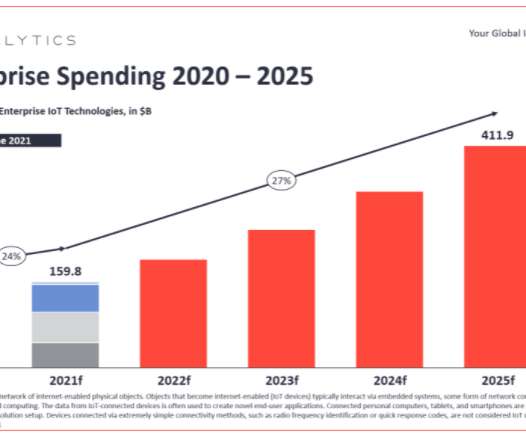
The European Union is poised to place more demands on manufacturers to design greater security into their wireless and Internet of Things (IoT) devices. The goal of the amendment – called a “delegated act” – is to ensure that all wireless devices are safe before they are sold in the EU. IoT Security Neglected.

SecureWorld News
NOVEMBER 27, 2024
Travelers often rely on technology to enhance vacations, like by sharing photos online or finding lodging on an app. The more laptops, tablets and smartphones you take with you, the more risk you open yourself up to. Some devices will automatically seek and connect to available wireless networks.

Krebs on Security
FEBRUARY 21, 2019
Here’s a look at the back side of that unwelcome parasite: A multi-functional wireless device found attached to a contactless payment terminal at a gas station. Using SMS-based skimmers, the fraudsters never need to take that risk and can receive the stolen card data in real-time from anywhere there is mobile phone service.

eSecurity Planet
SEPTEMBER 1, 2021
Consumers and organizations are enthused about the operational benefits of more robust mobile connectivity, but the shift to 5G networks doesn’t come without risks. Service providers and 5G-enabled device manufacturers both have critical roles to play in the success and sustainability of this wireless network rollout.

Schneier on Security
SEPTEMBER 26, 2019
There is definitely a national security risk in buying computer infrastructure from a country you don't trust. That's why there is so much worry about Chinese-made equipment for the new 5G wireless networks. The risk of discovery is too great, and the payoff would be too low. This is a complicated topic.

CyberSecurity Insiders
JANUARY 28, 2022
The technological revolution of agriculture is here. Particularly in the context of climate change and a growing global population , the role of emerging technology in the farming industry will be critical to the success and thriving of future generations. This is where smart farming technology can help. With as much as $22.3

Joseph Steinberg
JUNE 10, 2022
Many of Gillis’s comments echoed those that I have heard in recent months from CISOs and others within the cybersecurity industry who witness developments from various vantage points quite different from those of a vendor of cybersecurity technologies. Sampling No Longer Works.

Security Affairs
SEPTEMBER 5, 2020
The US Federal Communications Commission (FCC) estimates the cost of a full replacement of all Huawei and ZTE hardware on American wireless networks at $1.837bn. The United States , Australia , New Zealand , Romania , and Japan announced the exclusion of Huawei technology for their 5G internet networks. Pierluigi Paganini.

Security Affairs
DECEMBER 1, 2020
The British government will ban the installation of new Huawei equipment in the 5G networks of Wireless carriers after September 2021. The British government will not allow the installation of new Huawei equipment in the 5G networks of Wireless carriers after September 2021. ” th e UK Government announced. allegations.

Security Affairs
OCTOBER 21, 2020
Sweden is banning Chinese tech giant Huawei and ZTE from building new 5G wireless networks due to national security concerns. The United States , Australia , New Zealand , Romania , and Japan announced the exclusion of Huawei technology for their 5G internet networks.

Security Affairs
NOVEMBER 18, 2024
broadband providers, including Verizon, AT&T, and Lumen Technologies, potentially accessing systems for lawful wiretapping and other data. The security breach poses a major national security risk. In 2019, T-Mobile disclosed data breach affecting prepaid wireless customers.

SecureWorld News
FEBRUARY 18, 2024
Bluetooth has been around since 1994 as a wireless connectivity specification, but the first mobile phones did not appear with basic Bluetooth services until 2001. To begin, consider the simplest and most well-known risk. This is a well-known risk.
Security Affairs
DECEMBER 2, 2022
Once a niche technology, drones are about to explode in terms of market growth and enterprise adoption. Naturally, threat actors follow the trend and exploit the technology for surveillance, payload delivery, kinetic operations, and even diversion. Market overview. Attacks against enterprise-owned drones. Danger Drone platform.

Security Affairs
NOVEMBER 12, 2020
The Swedish Post and Telecom Authority announced that four wireless carriers bidding for frequencies in an upcoming spectrum auction for the new 5G networks (Hi3G Access, Net4Mobility, Telia Sverige and Teracom) cannot use network equipment from the Chinese firms.

Malwarebytes
MAY 13, 2021
Many people assume that WiFi is short for “wireless fidelity” because the term “hi-fi” stands for “high fidelity.” ” Some members of the WiFi Alliance, the wireless industry organization that promotes wireless technologies and owns the trademark, may even have encouraged this misconception.

Schneier on Security
JANUARY 14, 2020
The security risks inherent in Chinese-made 5G networking equipment are easy to understand. Eavesdropping is also a risk, although efforts to listen in would almost certainly be detectable. The technology will quickly become critical national infrastructure, and security problems will become life-threatening.

SecureWorld News
AUGUST 19, 2024
This technology promises greater efficiency and cost savings, but it also brings new security and privacy challenges that need careful consideration. Security risks Despite their benefits, smart meters introduce several security risks. Many smart meters do not encrypt their data, making it vulnerable to interception.

Security Affairs
AUGUST 13, 2019
“Plus, there’s only a small pool of OEMs working seriously with cellular technologies, and their hardware (& software dependencies) can be found running in all sorts of places.” The post Flaws in 4G Routers of various vendors put millions of users at risk appeared first on Security Affairs. ” Richter explained.

Security Affairs
OCTOBER 10, 2020
Proximus declared it made its choice “on the basis of technological, operational, financial and environmental criteria,”but the decision, according to sources cited by the Reuters, is the result of political pressure. The two operators, which share their mobile network, had faced political pressure to replace the Huawei equipment.

Krebs on Security
AUGUST 30, 2022
Phishers are enjoying remarkable success using text messages to steal remote access credentials and one-time passcodes from employees at some of the world’s largest technology companies and customer support firms. Unfortunately, a great many companies still rely on SMS for employee multi-factor authentication.

Security Affairs
NOVEMBER 25, 2019
Anyway, the economic impact of the replacement could be greater than initial thought, the AP Agency reports the case of a trade group for small rural wireless carriers that would spend up to $1 billion for its dozen companies to replace the Huawei and ZTE equipment. Currently, Huawei has tens of customers in the U.S.

CyberSecurity Insiders
NOVEMBER 1, 2021
Below is a five-step strategy to analyze the efficacy of your existing corporate safety protocols and reduce the risks of cyberattacks. Protect your wireless system with full backups. Make sure your wireless network is protected, concealed, and safe. . Putting data access in silos is a great way to mitigate the risks of leaks.

IT Security Guru
DECEMBER 1, 2020
And of course, the risks from hotspots are compounded when access devices are personal and unmanaged by Mobile Device Management (MDM) systems that can enforce security policies. Anyone deploying a Wi-Fi network should be aware of these top eight Wi-Fi risks. Finally, narrowing the Wi-Fi range will also reduce your risks.

Joseph Steinberg
JANUARY 28, 2021
Unfortunately, however, people have begun marketing for sale devices that allow criminals to exploit a technological vulnerability in these systems, and crooks have been seen using “mystery devices” to open cars equipped with hands-free car entry systems.

Penetration Testing
NOVEMBER 28, 2023
In the realm of wireless communications, Bluetooth stands as a ubiquitous technology, integral to billions of devices worldwide.

IT Security Guru
NOVEMBER 11, 2021
It’s mostly problems from the IT world, says Andy Norton, European Cyber Risk Officer at Armis. Operational technology (OT) used to be the specialist networks nobody in IT bothered with, or perhaps thought they didn’t need to. The Guru decided to ask Armis’ European cyber risk officer, Andy Norton for his thoughts.

Krebs on Security
FEBRUARY 23, 2021
But thieves are adept at exploiting weaknesses in how certain financial institutions have implemented the technology to sidestep key chip card security features and effectively create usable, counterfeit cards. Normally, overlay skimmers relay this data wirelessly using a built-in Bluetooth circuit board.

CyberSecurity Insiders
MARCH 31, 2022
And telecom company Verizon Wireless was forced to issue a public statement that some threat actors might have taken control of its servers to send spam to its users and diverting them to Russian state media network Channel One.

CyberSecurity Insiders
APRIL 27, 2021
To those uninitiated, Airdrop is a wireless technology offered by Apple Inc that enables users to share or transfer files via Bluetooth or Wi-Fi. However, the good news is that users who set their device settings to be accessed by ‘Everyone’ are only at risk and not all.

Security Affairs
APRIL 26, 2023
German government warns that technology to regulate power consumption in Huawei network appliances could be used for sabotage purposes. government officials as well as European security authorities, which have warned of the risks associated with Chinese telecoms equipment.” The FCC’s move definitively banned U.S.

The Last Watchdog
NOVEMBER 9, 2020
The good news is that we already possess the technology, as well as the best practices frameworks, to mitigate fast-rising IoT exposures. IoT risks have been a low-priority, subset concern. It’s Nelson’s job to help companies address IoT risks – but he also has a very personal stake. This surge can, and must, be blunted.

CyberSecurity Insiders
DECEMBER 14, 2022
The cyber alert was issued to companies involved in the business of offering applications and services related to the high-speed wireless internet broadband services. National Security Agency (NSA) has issued a report that has outlined cybersecurity threats related to 5G Network Slicing.

Security Affairs
NOVEMBER 14, 2019
The Canadian Security Intelligence Service (CSIS) and the Communications Security Establishment (CSE) are divided over the ban of Huawei 5G technology. The Canadian Security Intelligence Service (CSIS) and the Communications Security Establishment (CSE) agencies are divided over the ban of Huawei 5G technology.

Malwarebytes
JULY 24, 2024
TracFone Wireless Inc. is an American prepay wireless service provider wholly owned by Verizon. TracFone Wireless Inc. is an American prepay wireless service provider wholly owned by Verizon. TracFone services are used by the brands Straight Talk, Total by Verizon Wireless, and Walmart Family Mobile.

Security Affairs
AUGUST 25, 2018
We have been informed by the Govt that Huawei & ZTE have been banned from providing 5G technology to Australia. Has safely & securely delivered wireless technology in Aust for close to 15 yrs. Huawei Australia defined the decision disappointing. This is a extremely disappointing result for consumers.

SecureWorld News
JUNE 18, 2021
However, individual states may still set their own guidelines for election technology. Listening to this pushback on VVSG, the state of Ohio made the decision to ban all wireless capabilities in its election equipment, saying that everything should be 'air-gapped,' meaning the technology cannot connect to any outside networks.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content