Predator Spyware Spreads: 11 Countries Now at Risk
Penetration Testing
MARCH 3, 2024
The operators behind the invasive Predator mobile spyware remain undeterred by public exposure and scrutiny.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Penetration Testing
MARCH 3, 2024
The operators behind the invasive Predator mobile spyware remain undeterred by public exposure and scrutiny.

Penetration Testing
APRIL 11, 2024
Apple has sent warnings to a growing number of users, alerting them about highly sophisticated mercenary spyware attacks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
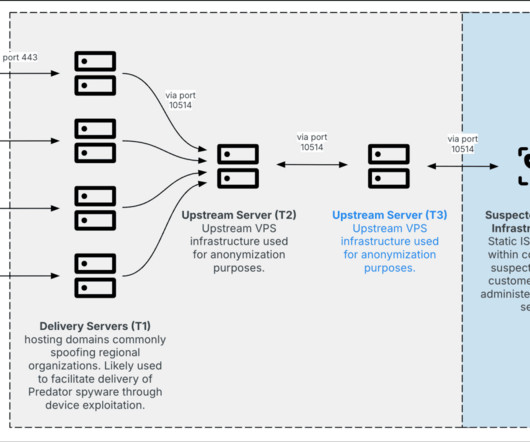
Penetration Testing
SEPTEMBER 8, 2024
Recently, cybersecurity researchers from Insikt Group have identified a resurgence of Predator spyware infrastructure, previously believed to be largely inactive due to public exposure and U.S. Despite these... The post Predator Spyware Roars Back: New Infrastructure, Evasive Tactics appeared first on Cybersecurity News.

Penetration Testing
NOVEMBER 29, 2023
The latest player in this game is sophisticated spyware, employing a series of ingenious obfuscation techniques to bypass static analysis, as revealed in a... The post How Spyware Evades Detection through Advanced Obfuscation appeared first on Penetration Testing.

Penetration Testing
JANUARY 17, 2024
Anomalies were detected by Kaspersky through vigilant monitoring of internal network traffic, leading to the uncovering of what is now known as ‘Operation Triangulation’ Kaspersky Lab remains steadfast in its pursuit to unravel the... The post iShutdown: The New Vanguard in Detecting iOS Spyware Threats appeared first on Penetration (..)

Penetration Testing
NOVEMBER 29, 2023
In an era increasingly defined by digital surveillance, a recent incident in Serbia has thrown a stark light on the use of invasive spyware to suppress civil society. Access Now, SHARE Foundation, the Citizen... The post Serbian Spyware Scandal: Civil Society Under Siege appeared first on Penetration Testing.

Penetration Testing
NOVEMBER 10, 2023
Researchers at ESET have discovered a new type of mobile spyware called Kamran, targeting Urdu-speaking residents of the Gilgit-Baltistan region.

Penetration Testing
NOVEMBER 24, 2023
There was a 46% increase in... The post Android Malware Surge: Adware Trojans, Spyware Trojans, and Banking Malware on the Rise appeared first on Penetration Testing.

Penetration Testing
APRIL 14, 2024
The resurgence of the LightSpy mobile spyware campaign poses a renewed and alarming threat to individuals and organizations in Southern Asia, particularly those potentially connected to India.

Penetration Testing
APRIL 9, 2025
A recent advisory from the National Cyber Security Centre (NCSC UK) and its international partners has shed light on the activities of malicious cyber actors using sophisticated spyware to target specific groups of people.

Penetration Testing
MAY 7, 2024
Dubbed “Cuckoo,” this nasty piece of code combines the worst aspects of spyware and info-stealers, designed to pilfer sensitive data and... The post “Cuckoo” Malware Lands on Macs, Steals Data, and Spies on Users appeared first on Penetration Testing.

Penetration Testing
DECEMBER 21, 2023
Born from the remnants of Cytrox, this spyware vendor has ascended to the echelons of intelligence agency-grade espionage tools. Cisco Talos’s... The post Unmasking Predator: Cisco Talos Exposes Spyware’s Hidden Depths appeared first on Penetration Testing.
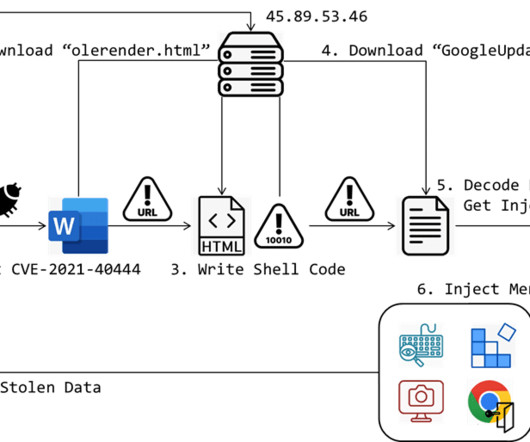
Penetration Testing
JUNE 28, 2024
Cybersecurity researchers at FortiGuard Labs have uncovered a sophisticated cyberattack that leverages a known vulnerability in Microsoft Office to deliver a potent spyware payload known as MerkSpy.

Penetration Testing
FEBRUARY 20, 2025
The Pegasus spyware, developed by Israeli commercial surveillance firm NSO Group, remains one of the most formidable threats The post Apple’s Spyware Detection: Only 50% Effective? appeared first on Cybersecurity News.

Penetration Testing
DECEMBER 5, 2024
In an investigation, iVerify has revealed the pervasive presence of the notorious Pegasus spyware in mobile devices, uncovering seven infections in a sample of 2,500 user-scanned devices.

Penetration Testing
JULY 26, 2024
A small Minnesota-based company, Spytech, specializing in spyware production, fell victim to a cyber attack. As a result of the data... The post Spytech Hacked: Thousands of Devices Exposed in Spyware Maker Breach appeared first on Cybersecurity News.

Penetration Testing
MARCH 15, 2025
A new Android surveillance tool, dubbed KoSpy, has been discovered by Lookout Threat Lab researchers, with evidence suggesting The post North Korean ScarCruft APT Targets Users with Novel KoSpy Android Spyware appeared first on Cybersecurity News.

Penetration Testing
APRIL 25, 2024
The detailed technical analysis provided... The post Hackers Employ Advanced Fileless Attack to Implant AgentTesla Malware appeared first on Penetration Testing.
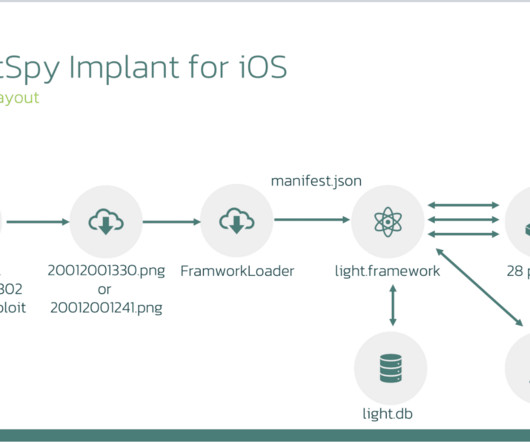
Penetration Testing
OCTOBER 29, 2024
ThreatFabric released a report detailing advancements in the LightSpy implant, an iOS spyware first identified in 2020, which has evolved into a more complex and damaging tool.

Penetration Testing
DECEMBER 12, 2024
Researchers at the Lookout Threat Lab have uncovered two sophisticated Android spyware families, BoneSpy and PlainGnome, attributed to the Russian-aligned Advanced Persistent Threat (APT) group Gamaredon.

Penetration Testing
DECEMBER 7, 2024
A joint investigation by the First Department and cybersecurity researchers has exposed the covert implantation of spyware resembling the Monokle family on a confiscated device returned to a Russian programmer....

Penetration Testing
JULY 26, 2024
German Member of the European Parliament, Daniel Freund, revealed that he was targeted by sophisticated spyware two weeks before the European Parliament elections. Freund is well-known... The post Spyware Targets MEP Daniel Freund Before EU Elections appeared first on Cybersecurity News.

Malwarebytes
FEBRUARY 21, 2024
Targeted automatic penetration testing scenario framework. While some of the information is dated, the leaked data provide an inside look in the operations that go on in a leading spyware vendor and APT-for-hire.

Penetration Testing
AUGUST 6, 2024
This spyware, named LianSpy, may have been active since mid-2021. Its detection difficulty is attributed to the attackers’ efforts to... The post New Android Spyware LianSpy Evade Detection for Years appeared first on Cybersecurity News.

Penetration Testing
JULY 1, 2024
The group is deploying a malicious Google Chrome extension called “TRANSLATEXT” to... The post North Korean Hackers Target South Korean Academics with New Chrome Extension Spyware appeared first on Cybersecurity News.

Penetration Testing
DECEMBER 22, 2024
A California court has ruled that Israeli firm NSO Group is liable for hacking into WhatsApp and deploying its notorious Pegasus spyware. The ruling, delivered by Judge Phyllis Hamilton in... The post Pegasus Spyware: Court Finds NSO Group Liable for 1,400 Infections appeared first on Cybersecurity News.

Penetration Testing
DECEMBER 20, 2023
The period from June to November has been marked by... The post From Magecart Mayhem to Ransomware Revamp: Inside ESET’s H2 2023 Cyber Threatscape appeared first on Penetration Testing.
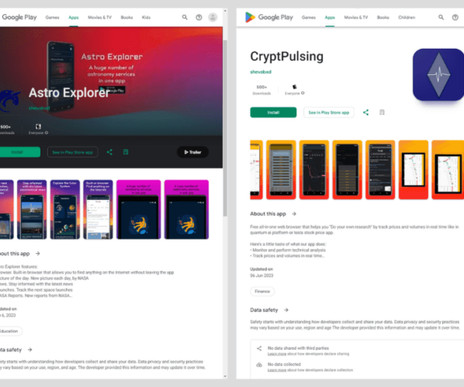
Penetration Testing
JULY 29, 2024
Kaspersky researchers revealed the return of the Mandrake Android spyware, which has been discovered lurking on the Google Play Store for two years, amassing over 32,000 downloads across five different apps.

eSecurity Planet
MAY 2, 2024
Sophos: Noted that 43% of all 2023 malware signature updates are for stealers, spyware, and keyloggers often used to steal credentials from devices. 60% of all mobile and browser zero-days are exploited by spyware vendors. 20% increase accesses of specific organizations advertised. and software libraries to attack the supply chain.

Penetration Testing
DECEMBER 16, 2024
A new report by Amnesty International reveals that NSO Group’s Pegasus spyware was used to target iPhones belonging to Serbian journalists and activists. The attacks were conducted using a zero-click... The post Zero-Click HomeKit Exploit Used to Spy on Serbian Journalists appeared first on Cybersecurity News.

SecureList
NOVEMBER 30, 2021
In November, Apple announced that it was taking legal action against NSO Group for developing software that targets its users with “malicious malware and spyware” Detecting infection traces from Pegasus and other advanced mobile malware is very tricky, and complicated by the security features of modern OSs such as iOS and Android.

SecureWorld News
AUGUST 8, 2022
Cybercriminals often use malware to gain access to a computer or mobile device to deploy viruses, worms, Trojans, ransomware, spyware, and rootkits. Remcos Remcos is marketed as a legitimate software tool for remote management and penetration testing. Qakbot can also be used to form botnets.

BH Consulting
SEPTEMBER 24, 2024
MORE Mythical beasts and where to find them: mapping the global spyware landscape MORE Six truths of quantifying cyber risk, as told by Google CISO Phil Venables. MORE Rahim Jina explores what DORA will mean for penetration testing. Links we liked Secrets of a ransomware negotiator, as told in The Economist.

Security Boulevard
MAY 3, 2021
That link would attempt to install spyware called Flubot, malware designed to steal online banking data from Andriod devices. . Which is more Important: Vulnerability Scans Or Penetration Tests? Millions of UK citizens received a scam text message (aka smashing) which impersonated DHL in April. Stay safe and secure.

eSecurity Planet
MARCH 22, 2023
Penetration testing and vulnerability scanning should be used to test proper implementation and configuration. Endpoint Security: Antivirus , anti-spyware , endpoint detection and response (EDR), and other controls should be deployed to secure the endpoint against compromise. and mobile (phones, tablets, etc.)

Security Affairs
NOVEMBER 8, 2019
” A new wave of attacks could exploit the vulnerability to spread more dangerous and destructive malware, like ransomware or spyware. ” Microsoft confirmed that attackers are leveraging an exploit module released for the Metasploit penetration testing platform.

eSecurity Planet
MARCH 14, 2023
Often auditing will be performed through the review of networking logs, but penetration testing and vulnerability scanning can also be used to check for proper implementation and configuration. Penetration testing and IT architecture design can also be useful skills, but some organizations will outsource these specialties.
SecureList
NOVEMBER 22, 2022
Looking for alternative sources to download an episode of a show or a newly released film, users encounter various types of malware, including Trojans, spyware and backdoors, as well as adware. More new “Red Team” penetration testing frameworks deployed by cybercriminals.
Security Affairs
JANUARY 10, 2021
The exploit called “SignSight” involved the modification of software installers hosted on the Certificate Authorities website (“ca.gov.vn”) to insert a spyware tool called PhantomNet or Smanager to unsuspecting end users. For more information on this breach, see: Software Supply-Chain Attack Hits Vietnam Government Certification Authority.
SecureList
AUGUST 15, 2022
The attack starts by driving targets to a legitimate website and tricking them into downloading a compressed RAR file that is booby-trapped with the network penetration testing tools Cobalt Strike and SilentBreak. WinDealer’s man-on-the-side spyware.

Herjavec Group
AUGUST 26, 2021
2008 — Heartland Payment Systems — 134 million credit cards are exposed through SQL injection to install spyware on Heartland’s data systems. The security team reported their Red Team toolkit, containing applications used by ethical hackers in penetration tests, was stolen. east coast.

Penetration Testing
DECEMBER 11, 2024
Researchers at the Lookout Threat Lab have identified a sophisticated surveillance tool, dubbed EagleMsgSpy, reportedly used by law enforcement agencies in mainland China. The tool, operational since at least 2017,... The post EagleMsgSpy: Unmasking a Sophisticated Chinese Surveillance Tool appeared first on Cybersecurity News.

Penetration Testing
DECEMBER 19, 2024
McAfee Labs uncovered a malicious app on the Amazon Appstore that disguised itself as a simple health tool while secretly stealing sensitive user data. The app, named BMI CalculationVsn, pretended... The post Malicious App Found on Amazon Appstore Masquerades as Health Tool appeared first on Cybersecurity News.

Penetration Testing
APRIL 20, 2025
A security researcher published a proof-of-concept exploit code for an Android zero-day exploit chain developed by Cellebrite to The post Cellebrite Android Zero-Day Exploit PoC Released: CVE-2024-53104 appeared first on Daily CyberSecurity.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content