Password-stealing spyware targets Android users in the UK
Tech Republic Security
APRIL 27, 2021
The spyware tries to steal passwords and other sensitive data and accesses your contact list, warns the U.K.'s s National Cyber Security Centre.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
APRIL 27, 2021
The spyware tries to steal passwords and other sensitive data and accesses your contact list, warns the U.K.'s s National Cyber Security Centre.

Tech Republic Security
APRIL 12, 2024
Apple recommends that iPhone users install software updates, use strong passwords and 2FA, and don’t open links or attachments from suspicious emails to keep their device safe from spyware.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Adam Levin
JANUARY 25, 2019
Trojan horse-based malware attacks and spyware rose sharply in 2018 as ransomware-based attacks declined, according to a new report published by Malwarebytes. The post Trojans and Spyware Are Making a Comeback appeared first on Adam Levin.

Krebs on Security
SEPTEMBER 4, 2018
Before it was taken offline sometime in the past 12 hours, the database contained millions of records, including the username, password and private encryption key of each mSpy customer who logged in to the mSpy site or purchased an mSpy license over the past six months. In September 2014, U.S. In September 2014, U.S.

Schneier on Security
JUNE 23, 2021
Its spyware is also said to be equipped with a keylogger, which means every keystroke made on an infected device — including passwords, search queries and messages sent via encrypted messaging apps — can be tracked and monitored.

Malwarebytes
JULY 12, 2024
In a new round, Apple is now warning users in 98 countries of potential mercenary spyware attacks. The message sent to the affected users says: “Apple detected that you are being targeted by a mercenary spyware attack that is trying to remotely compromise the iPhone associated with your Apple ID.”

CyberSecurity Insiders
JULY 19, 2021
And keep their apps on phone secured with 2FA backed passwords. The post Apple iPhones to get protection against Pegasus Mobile Spyware appeared first on Cybersecurity Insiders. Till then the iPhone owners are requested to avoid using unknown Wi-Fi networks for accessing internet on their devices.

Malwarebytes
APRIL 28, 2021
This time it seems to be very active, especially in the UK where Android users are being targeted by text messages containing a link to a particularly nasty piece of spyware called Flubot. The tracking app is in fact spyware that steals passwords and other sensitive data. Warning from the National Cyber Security Centre.

CyberSecurity Insiders
JULY 22, 2021
Chine Foreign Ministry has issued a public statement condemning the distribution and usage of Pegasus Spyware surveillance software by various countries. The post China officially condemns Pegasus spyware surveillance and accuses US appeared first on Cybersecurity Insiders.

Schneier on Security
JULY 6, 2020
But it's nasty: In addition to ransomware, ThiefQuest has a whole other set of spyware capabilities that allow it to exfiltrate files from an infected computer, search the system for passwords and cryptocurrency wallet data, and run a robust keylogger to grab passwords, credit card numbers, or other financial information as a user types it in.

Malwarebytes
SEPTEMBER 27, 2023
Recent events have demonstrated very clearly just how persistent and wide-spread the Pegasus spyware is. The exploit chain based on these vulnerabilities was capable of compromising devices without any interaction from the victim and were reportedly used by the NSO Group to deliver its infamous Pegasus spyware.

SecureList
JUNE 21, 2023
Over the years, there have been multiple cases when iOS devices were infected with targeted spyware such as Pegasus, Predator, Reign and others. Due to this granularity, discovering one exploit in the chain often does not result in retrieving the rest of the chain and obtaining the final spyware payload. db database.
Security Affairs
APRIL 16, 2024
Researchers warn of a renewed cyber espionage campaign targeting users in South Asia with the Apple iOS spyware LightSpy Blackberry researchers discovered a renewed cyber espionage campaign targeting South Asia with an Apple iOS spyware called LightSpy. 217:52202, which also hosts an administrator panel accessible on port 3458.
Malwarebytes
JUNE 29, 2022
Google’s Threat Analysis Group (TAG) has revealed a sophisticated spyware activity involving ISPs (internet service providers) aiding in downloading powerful commercial spyware onto users’ mobile devices. The spyware, dubbed Hermit, is reported to have government clients much like Pegasus.
Security Affairs
AUGUST 12, 2020
Agent Tesla is a spyware that is used to spy on the victims by collecting keystrokes, system clipboard, screenshots, and credentials from the infected system. To do this, the spyware creates different threads and timer functions in the main function. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.
Malwarebytes
SEPTEMBER 29, 2022
This particular campaign, initially discovered by an Internet researcher going by the handle @idclickthat , gets unsuspecting users to download an information-stealer— spyware , if you prefer—from fake sites hosting malformed Zoom installers (malware bundled with a legitimate Zoom installer) onto their work systems.

Security Affairs
JULY 25, 2019
Researchers at Lookout discovered a new mobile spyware dubbed Monokle that was developed by a Russian defense contractor. Experts at Lookout discovered a new Android mobile spyware in the wild, dubbed Monokle, that was developed by a Russian defense contractor named Special Technology Centre Ltd. ( Pierluigi Paganini.

Security Affairs
NOVEMBER 19, 2024
DEEPPOST is a post-exploitation data exfiltration tool used to send files to a remote system and LIGHTSPY is a modular spyware. WebBrowser Collect history, cookies, and passwords from Firefox, Chrome, Opera, and Edge web browsers. SystemInfo Gather basic enumeration information from the compromised device.

Krebs on Security
SEPTEMBER 12, 2023
7, researchers at Citizen Lab warned they were seeing active exploitation of a “zero-click,” zero-day flaw to install spyware on iOS devices without any interaction from the victim. Citizen Lab says the bug it discovered was being exploited to install spyware made by the Israeli cyber surveillance company NSO Group.

Tech Republic Security
DECEMBER 12, 2016
The password simply isn't secure anymore. Spyware, brute force attacks, dictionary attacks, and phishing can make circumventing passwords easy. Here are five tools to add an extra layer of security.

Malwarebytes
MAY 28, 2024
As you may have read many times before on our blog, some spyware companies have a surprisingly low standard of security. Daigle found that pcTattleTale’s Application Programming Interface (API) allows any attacker to access the most recent screen capture recorded from any device on which the spyware is installed.

Malwarebytes
APRIL 11, 2024
Mercenary spyware is used by governments to target people like journalists, political activists, and similar targets, and involves the use of sophisticated tools like Pegasus. Pegasus is one of the world’s most advanced and invasive spyware tools, known to utilize zero-day vulnerabilities against mobile devices. Use a password manager.

Security Affairs
SEPTEMBER 4, 2018
The company that sells the parental control spyware app Family Orbit has been hacked, pictures of hundreds of monitored children were left online. The company that sells the parental control spyware app Family Orbit has been hacked, the pictures of hundreds of monitored children were left online only protected by a password.

Security Affairs
NOVEMBER 3, 2024
Chinese threat actors use Quad7 botnet in password-spray attacks FBI arrested former Disney World employee for hacking computer menus and mislabeling allergy info Sophos details five years of China-linked threat actors’ activity targeting network devices worldwide PTZOptics cameras zero-days actively exploited in the wild New LightSpy spyware (..)

Security Affairs
APRIL 16, 2019
Scranos is a powerful cross-platform rootkit-enabled spyware discovered while investigating malware posing as legitimate software like video players, drivers and even anti-virus products. “The dropper, which doubles as a password stealer, installs a driver that provides persistence to all other components to be installed in the future.

SecureWorld News
OCTOBER 31, 2024
Like vampires, malware strains can operate quietly, leeching data or encrypting files without warning, making ransomware and spyware infections incredibly haunting. How to keep the ghosts away : Conduct routine audits of connected devices, disconnect unused devices, and enforce strong password policies across all endpoints.
Security Boulevard
MARCH 24, 2025
Researchers name several countries as potential Paragon spyware customers TechCrunch The Citizen Lab, a group of academics and security researchers, recently published a report indicating the governments of Australia, Canada, Cyprus, Denmark, Israel, and Singapore are "likely" customers of Israeli spyware maker Paragon Solutions.

Malwarebytes
SEPTEMBER 4, 2024
After using passwords obtained from one of the countless breaches as a lure to trick victims into paying, the “Hello pervert” sextortion scammers have recently introduced two new pressure tactics: Name-dropping the infamous Pegasus spyware and adding pictures of your home environment. The scammer says they know “your password.”
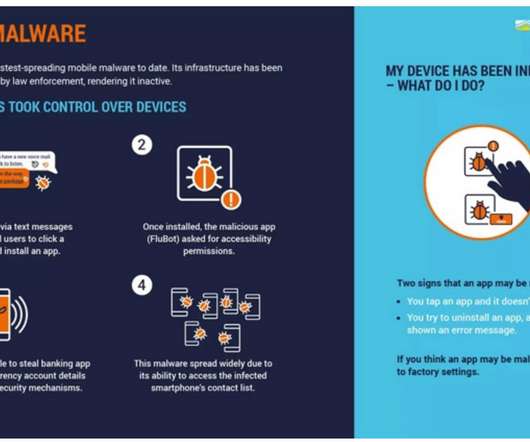
Security Affairs
JUNE 2, 2022
Known as FluBot, this Android malware has been spreading aggressively through SMS, stealing passwords, online banking details and other sensitive information from infected smartphones across the world.” The post An international police operation dismantled FluBot spyware appeared first on Security Affairs. Pierluigi Paganini.

Malwarebytes
JUNE 29, 2023
In the database file which was later dumped online, the blog said there was: 26,000+ email addresses of the tool's "operators" along with hashes of their passwords. How to prevent spyware and stalkerware-type apps Set a screen lock on your phone and don't let anyone else access it Keep your phone up-to-date.

eSecurity Planet
NOVEMBER 12, 2024
Password manager: Norton generates strong passwords and syncs logins across all your protected devices. Norton has a password manager in all of its Antivirus plans, and all the 360 plans also have a VPN. Norton doesn’t have spyware protection; I recommend looking at business antivirus products if that’s a priority for you.

Troy Hunt
MARCH 23, 2019
Elsevier looks like they logged a bunch of passwords in plain text (who would do that.

WIRED Threat Level
JULY 1, 2020
The malware known as ThiefQuest or EvilQuest also has spyware capabilities that allow it to grab passwords and credit card numbers.

Webroot
FEBRUARY 21, 2025
It combines multiple security capabilities into one easy-to-use package that includes: Antivirus protection Detects and neutralizes viruses, malware , spyware , and ransomware. Password Manager Ensures your passwords are strong and secure, while also making them easy to access and manage.

Security Affairs
AUGUST 7, 2022
Greek intelligence service used surveillance malware to spy on a journalist, Reuters reports Slack resets passwords for about 0.5% of its users due to the exposure of salted password hashes Twitter confirms zero-day used to access data of 5.4

Schneier on Security
MARCH 14, 2023
From Brian Krebs : A Croatian national has been arrested for allegedly operating NetWire, a Remote Access Trojan (RAT) marketed on cybercrime forums since 2012 as a stealthy way to spy on infected systems and siphon passwords. The arrest coincided with a seizure of the NetWire sales website by the U.S. Federal Bureau of Investigation (FBI).

SiteLock
AUGUST 27, 2021
Cybercriminals were able to exploit the default password on thousands of these innocuous devices to carry out this nefarious attack. When not secured properly on their own Wi-Fi channel, IoT devices can be more than an inconvenience, they can be seen as a critical security risk due to the poor security protocols like fixed default passwords.

Troy Hunt
SEPTEMBER 7, 2018
Be that as it may, I did manage to pump out a long-awaited blog post on the total cost of running Pwned Passwords in HIBP and its. This week there's also a few random things ranging from online authenticity (the human kind), changes in Chrome 69 (there's some major visual security indicators gone), yet another spyware breach (just don't.),

IT Security Guru
APRIL 26, 2021
Spyware – Without realising it, gamers could be targeted through spyware schemes, especially if they are dealing with an untrustworthy online gaming operation. Spyware monitors a user’s every movement and actions on the internet without their knowledge. Additionally, following basic password security hygiene is beneficial.
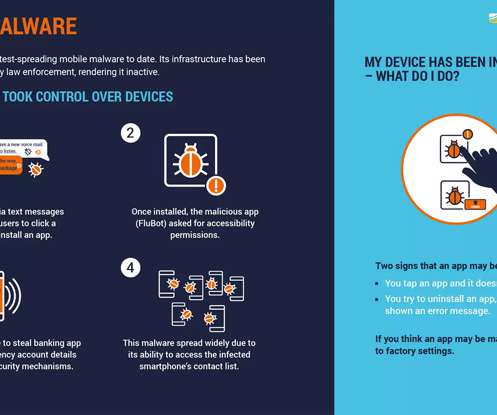
The Hacker News
JUNE 1, 2022
This Android malware has been spreading aggressively through SMS, stealing passwords, online banking details and other sensitive information from infected smartphones across the world," Europol said in a statement. The "complex

Security Affairs
JULY 30, 2018
A new sophisticated version of the AZORult Spyware was spotted in the wild, it was involved in a large email campaign on July 18. Malware researchers at Proofpoint spotted a new version of the AZORult Spyware in the wild, it was involved in a large email campaign on July 18, just 24 hours it appeared in cybercrime forums on the Dark Web.

Security Affairs
JANUARY 19, 2025
CISA adds Aviatrix Controllers vulnerability to its Known Exploited Vulnerabilities catalog ESET detailed a flaw that could allow a bypass of the Secure Boot in UEFI systems Russia-linked APT Star Blizzard targets WhatsApp accounts Prominent US law firm Wolf Haldenstein disclosed a data breach Clop Ransomware exploits Cleo File Transfer flaw: dozens (..)

The Last Watchdog
JANUARY 28, 2019
Use a password manager. It’s clear that we will continue to be reliant on usernames and passwords to access online services for some time to come. This means using strong passwords — and changing them frequently — will remain a vital best security practice. Apps from other sources can carry malware or spyware.

Security Affairs
NOVEMBER 15, 2023
Source: Cybernews The exposed phone numbers can be exploited for spam, malware and spyware attacks, SIM swapping, and the discovery of user accounts on platforms like WhatsApp, Signal, and others. Notes on users, submitted by admins and customer support agents. The leaked IP addresses introduce the risk of a takeover of a local network.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content