China-linked APT Silk Typhoon targets IT Supply Chain
Security Affairs
MARCH 5, 2025
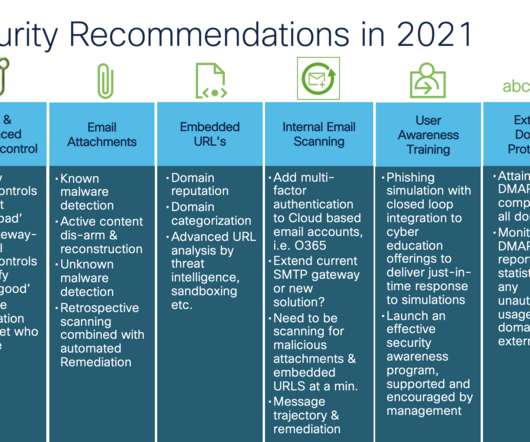
Silk Typhoon targets multiple sectors worldwide, including information technology (IT) services and infrastructure, remote monitoring and management (RMM) companies, managed service providers (MSPs) and affiliates, healthcare, legal services, higher education, defense, government, non-governmental organizations (NGOs), and energy.

















































Let's personalize your content