“Urgent reminder” tax scam wants to phish your Microsoft credentials
Malwarebytes
APRIL 1, 2025
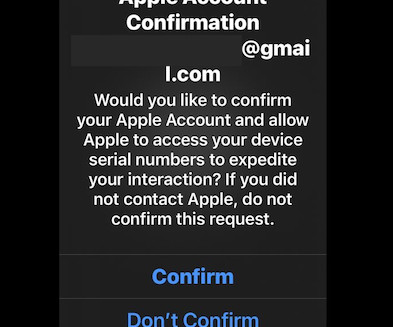
Entering your password will send your credentials to a Russian receiver, who will decide what the most profitable way to use them is. But that’s just one example of a tax scam. The IRS’s annual Dirty Dozen list of tax scams shows common schemes that threaten your tax and financial information.













































Let's personalize your content