Wanted: Disgruntled Employees to Deploy Ransomware
Krebs on Security
AUGUST 19, 2021
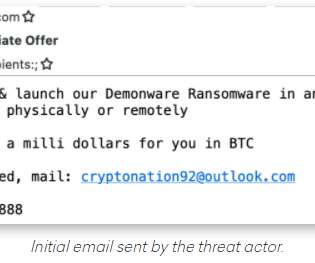
Criminal hackers will try almost anything to get inside a profitable enterprise and secure a million-dollar payday from a ransomware infection. ” This attacker’s approach may seem fairly amateur, but it would be a mistake to dismiss the threat from West African cybercriminals dabbling in ransomware. billion in 2020.










































Let's personalize your content