Breaking a Password Manager
Schneier on Security
JUNE 4, 2024
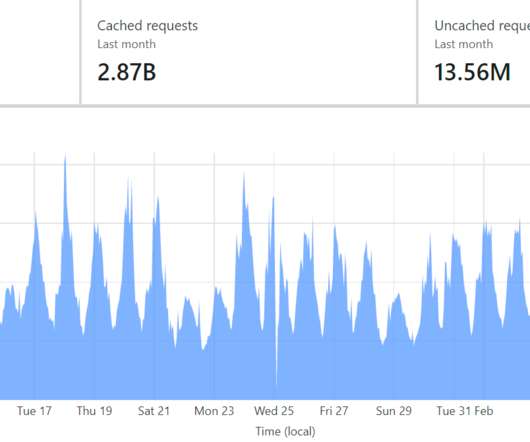
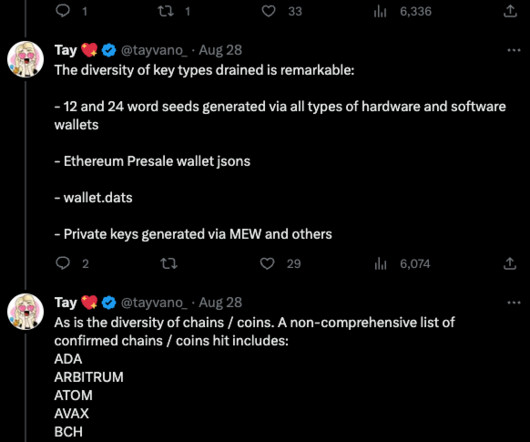
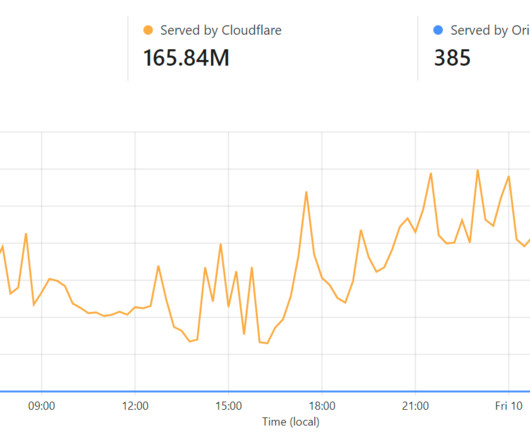
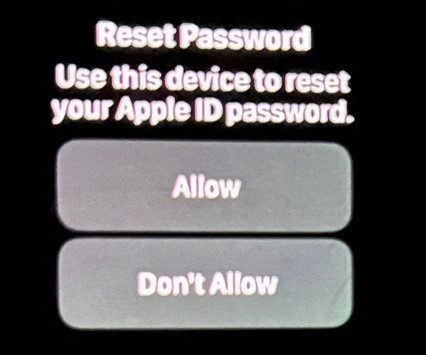
Interesting story of breaking the security of the RoboForm password manager in order to recover a cryptocurrency wallet password. If you knew the date and time and other parameters, you could compute any password that would have been generated on a certain date and time in the past.





















Let's personalize your content