‘Predator’ — Nasty Android Spyware Revealed
Security Boulevard
MAY 30, 2023
Intellexa mercenary spyware chains five unpatched bugs—plus ‘Alien’ technology The post ‘Predator’ — Nasty Android Spyware Revealed appeared first on Security Boulevard.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Security Boulevard
MAY 30, 2023
Intellexa mercenary spyware chains five unpatched bugs—plus ‘Alien’ technology The post ‘Predator’ — Nasty Android Spyware Revealed appeared first on Security Boulevard.
Security Affairs
FEBRUARY 24, 2021
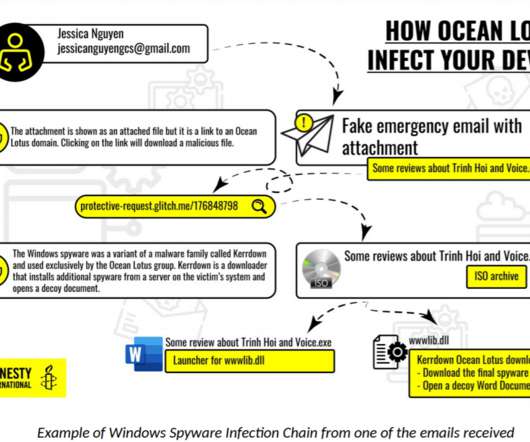
The threat actors used by spyware to take over the target systems, spy on the victims, and exfiltrate data. The APT32 also targeted peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors. Pierluigi Paganini.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
MARCH 28, 2024
The number of zero-day vulnerabilities that are exploited jumped in 2023, with enterprises becoming a larger target and spyware vendors and China-backed cyberespionage groups playing an increasingly bigger role, according to Google cybersecurity experts.

Security Boulevard
SEPTEMBER 25, 2023
The post More iOS Zero Days, More Mercenary Spyware — This Time: Cytrox Predator appeared first on Security Boulevard. Apple Scrambled to Fix 3 More CVEs: Egyptian opposition presidential candidate Ahmed Eltantawy targeted “by the government.

Security Boulevard
JUNE 28, 2023
The post Ironic: LetMeSpy Spyware Hackers Were Hacked (by Hackers) appeared first on Security Boulevard. Content warning: Abuse, stalking, controlling behavior, Schadenfreude, irony, doxxing.

Security Boulevard
JULY 22, 2021
The post Pegasus And Spyware | Avast appeared first on Security Boulevard. The tool of choice for these activities was the Israeli NSO Group’s Pegasus, a tool that can be deployed on Android and Apple smartphones with a great deal of stealth.

Security Boulevard
MAY 3, 2022
The notorious spyware, sold by NSO Group “only to governments,” caused large amounts of data to be exfiltrated. Hacked by NSO Pegasus Spyware (or was it?) appeared first on Security Boulevard. The prime minister and the defense minister of Spain were infected with Pegasus. The post Spanish Govt.

Security Boulevard
AUGUST 1, 2022
Last summer, we wrote about a major international investigation of the NSO Group and its Pegasus spyware. The post NSO Pegasus Spyware Developments | Avast appeared first on Security Boulevard. We described how it works and what you can do to protect your phone.

Security Boulevard
AUGUST 22, 2022
NSO, notorious producer of the Pegasus nation-state spyware, is struggling. The post NSO Group Fires CEO — and 100 Staff — in Spyware ‘Streamlining’ appeared first on Security Boulevard. So it’s dumped its CEO, Shalev Hulio, and around 100 employees.

Security Boulevard
JULY 19, 2023
Adds ‘Mercenary Spyware’ Firms to Ban List appeared first on Security Boulevard. European cousins Intellexa and Cytrox essentially banned by Commerce Dept. Predator/ALIEN not welcome in U.S. The post Biden Admin.

eSecurity Planet
MARCH 14, 2023
Network security creates shielded, monitored, and secure communications between users and assets. Securing the expanding, sprawling, and sometimes conflicting collection of technologies that make up network security provides constant challenges for security professionals.

Security Boulevard
MARCH 13, 2025
A North Korea-backed threat group, APT37, disguised KoSpy as utility apps in Google Play to infect Android devices, using the spyware for such activities as gathering sensitive information, tracking locations, capturing screenshots, recording keystrokes, and accessing files.

Security Boulevard
APRIL 11, 2024
Apple reportedly is alerting iPhone users in 92 countries that they may have been the targets of attacks using “mercenary spyware,” a term that the company is now using in such alerts in place of “state-sponsored” malware. Apple’s messages to affected users said they were being “targeted by a mercenary spyware attacks that is trying.

Dark Reading
JUNE 21, 2022
ToddyCat's Samurai and Ninja tools are designed to give attackers persistent and deep access on compromised networks, security vendor says.

Security Boulevard
JUNE 23, 2023
Vulns unpatched for FOUR years: ‘Triangulation’ spyware said to use backdoor Apple gave to NSA. The post Apple Fixes 0-Days — Russia Says US Used for Spying appeared first on Security Boulevard.

Security Boulevard
AUGUST 5, 2021
That culprit could be spyware. Spyware is software that tracks your internet surfing and [.]. The post Spyware: What It Is, How It Works, and How to Prevent It appeared first on TechSpective. The post Spyware: What It Is, How It Works, and How to Prevent It appeared first on Security Boulevard.

eSecurity Planet
NOVEMBER 12, 2024
If you’re looking to protect your entire home network, learn more about overall network security. 5 McAfee Total Protection is a set of five consumer security plans that include antivirus, web protection, and safety scores. McAfee also doesn’t offer spyware detection. 5 Pricing: 4.7/5 5 Core features: 3.3/5

SiteLock
AUGUST 27, 2021
Make sure that all of your network-connected devices have the latest version. You should also install any security software updates and network security patches as soon as they’re available to patch any security vulnerabilities that can be exploited through outdated versions of IoT software. The Bottom Line.

eSecurity Planet
MARCH 28, 2025
Fortinet and Palo Alto Networks are two of the best network security providers, offering excellent next-generation firewalls (NGFWs) with strong, independently verified security. 5 Customer support: 4/5 Fortinets FortiGate is a series of network security appliances that protect networks from threats.

eSecurity Planet
FEBRUARY 16, 2021
Rogue security software. Architect a premium network security model like SASE that encompasses SD-WAN , CASB , secure web gateways , ZTNA , FWaaS , and microsegmentation. However, a growing number of botnet attacks are used against IoT devices and their connected networks. Jump ahead: Adware. Bots and botnets.

CyberSecurity Insiders
MARCH 21, 2021
When it comes to protecting your small business from cyber attacks, the first and foremost thing is to upgrade your network security and IT infrastructure to the latest standards. Modern technology comes with improved network security offering higher protection. . Ensure Network Security .

eSecurity Planet
FEBRUARY 17, 2025
It tries to provide features like anti-ransomware, anti-spyware, and parental controls, but that still keeps it behind. However, some of these features could be present in Microsoft 365 security subscription packages, which we will review later in this guide. McAfee also doesnt offer spyware detection, but Defender does.

Security Affairs
DECEMBER 5, 2021
Hundreds of vulnerabilities in common Wi-Fi routers affect millions of users German BSI agency warns of ransomware attacks over Christmas holidays Cuba ransomware gang hacked 49 US critical infrastructure organizations CISA warns of vulnerabilities in Hitachi Energy products NSO Group spyware used to compromise iPhones of 9 US State Dept officials (..)

Security Affairs
SEPTEMBER 12, 2019
“The main Simjacker attack involves an SMS containing a specific type of spyware-like code being sent to a mobile phone, which then instructs the SIM Card within the phone to ‘take over’ the mobile phone to retrieve and perform sensitive commands.” ” continues the post.

SecureList
DECEMBER 9, 2024
Fortinet products are integral to many organizations’ network security. When critical vulnerabilities in such widely deployed products are exploited, it opens a pathway for attackers to breach the security of multiple organizations through a single vendor’s software or appliances. Why does it matter?
eSecurity Planet
FEBRUARY 9, 2022
MDR services , for example, often include network security services, and vice versa. Trend Micro Managed XDR is an integrated managed service across email, endpoints, servers, cloud workloads, and networks. Lookout Mobile Endpoint Security addresses iOS, Android, and Chrome OS devices. Network Security.

eSecurity Planet
MARCH 22, 2023
Networks connect devices to each other so that users can access assets such as applications, data, or even other networks such as the internet. Network security protects and monitors the links and the communications within the network using a combination of hardware, software, and enforced policies.

Security Affairs
SEPTEMBER 9, 2019
In 2016, researchers from non-profit organization CitizenLab published a report that describes a campaign of targeted spyware attacks carried by the Stealth Falcon. “Compared with traditional communication via API functions, the BITS mechanism is exposed through a COM interface and thus harder for a security product to detect.

Security Boulevard
MAY 28, 2021
The flaw was discovered by cybersecurity firm Jamf when, according to its blog , it observed XCSSET spyware “using this bypass specifically for the purpose of taking screenshots of the user’s desktop without requiring additional permissions.”

eSecurity Planet
FEBRUARY 26, 2021
ESET acts as a single point of network security management and is available as both a cloud-based or on-premises solution. This tool can block suspicious emails that may contain spyware, ransomware and phishing websites. Notable features. ESET’s Antispam feature is also a valuable asset for bolstering data integrity.

Malwarebytes
JUNE 7, 2021
Malicious hackers might use tools like computer viruses, spyware, ransomware, Trojan horses, and more to further their goals. An unethical hacker can use many techniques and tools to breach your computer or device’s network security. Many people wonder what motivates hackers who have had intentions.

eSecurity Planet
JUNE 7, 2022
Cybersecurity is the method that is used to protect the network, system, or applications from the cyber-attacks. Application security, information security, network security, disaster recovery, operational security, etc. It is used to avoid unauthorized data access, cyber-attacks, and identity theft.

eSecurity Planet
FEBRUARY 4, 2022
Where WiFi 5 routers could get overwhelmed when too many devices attempted to connect which could compromise network security, WiFi 6 routers should alleviate that problem, providing a better internet security suite by preventing attackers from just spamming a router with connect requests. Web Application Firewall (WAF).

Security Boulevard
OCTOBER 15, 2021
We do not allow ads promoting spyware for partner surveillance,” a Google spokesperson told TechCrunch. “We The app developers took advantage of the gray areas of the policy, which allows ads for surveillance apps targeted at parents to keep track of their children or workplaces to keep track of their employees’ devices. “We

eSecurity Planet
FEBRUARY 6, 2024
Securing an Individual Device Outside the Corporate Network Host-based firewalls give an extra layer of security in situations where individual devices may be vulnerable to attacks, especially when used outside of the corporate network. With two-way protection, it shields PCs from hackers and avoids spyware exposure.

eSecurity Planet
FEBRUARY 26, 2021
ESET acts as a single point of network security management and is available as both a cloud-based or on-premises solution. This tool can block suspicious emails that may contain spyware, ransomware and phishing websites. Notable features. ESET’s Antispam feature is also a valuable asset for bolstering data integrity.

eSecurity Planet
SEPTEMBER 11, 2023
The 10 components listed below not only cover the main components of containerized network architecture but also the container security tools that are most important for this type of network setup. Examples of container networking and virtualization tools include VMWare NSX and HAProxy.

eSecurity Planet
AUGUST 12, 2023
” Digital Espionage: “Spyware installed in data centers across the world could be leveraged for extreme cyberespionage,” they wrote. This malware could be leveraged for unprecedented ransomware , DDoS or Wiper attacks that would completely dwarf SuxNet, Mirai BotNet , or WannaCry.”

IT Security Guru
FEBRUARY 13, 2023
Malware Cybercriminals can use malware like spyware to break into your phone or computer and potentially steal your banking details. The best antivirus programs will offer a built-in firewall, essentially a network security device that provides a barrier between a trusted network and an untrusted network. 10.

eSecurity Planet
MAY 2, 2024
Sophos: Noted that 43% of all 2023 malware signature updates are for stealers, spyware, and keyloggers often used to steal credentials from devices. Company instructions to keep hands off internal network traffic leads to internet service provider (ISP) suppression of only 1% of the 100,000 monthly outgoing DDoS attacks.
eSecurity Planet
MARCH 27, 2023
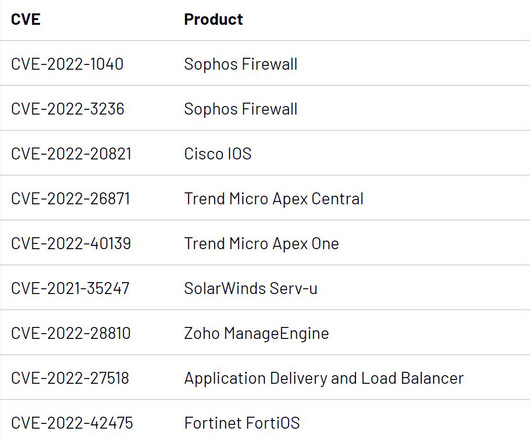
Exploited enterprise IT zero-day vulnerabilities: Mandiant Commercial Use of Zero-Days Mandiant also observed three cases in which commercial spyware companies leveraged zero-day flaws.

eSecurity Planet
OCTOBER 21, 2022
Want to Make Sure Remote Workers Can Access Your Network Securely? Check Out Secure Access for Remote Workers: RDP, VPN & VDI. Employee monitoring software can look very similar to spyware, a type of malware used by hackers to track user activity and steal their data. Does Employee Monitoring Increase Productivity?

eSecurity Planet
SEPTEMBER 11, 2023
Android, Apple, Apache, Cisco, and Microsoft are among the names reporting significant security vulnerabilities and fixes in the last week, and some of those are already under assault by hackers. The problem: The zero-day vulnerabilities were actively exploited in attacks against iPhone and Mac users.

eSecurity Planet
JANUARY 15, 2021
The McAfee Network Security Platform (NSP) is a next-generation intrusion detection and prevention solution that protects systems and data wherever they reside, across data centers, the cloud and hybrid enterprise environments. The solution offers network traffic inspection throughput up to 120 Gbps. Starts at $5,595.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content