Setting Up Your Network Security? Avoid These 4 Mistakes
Tech Republic Security
OCTOBER 4, 2024
Learn how to execute the fundamentals, harden your defenses, and protect your business's network security with no high-tech software.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
OCTOBER 4, 2024
Learn how to execute the fundamentals, harden your defenses, and protect your business's network security with no high-tech software.
The Last Watchdog
FEBRUARY 25, 2025
This category of awards ranks the worlds top 50 software education products based on authentic reviews from more than 100 million G2 users. Warn “We are thrilled to be recognized for a second consecutive year by G2’s Best Software Awards, said Dara Warn, CEO of INE. Cary, NC, Feb.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JUNE 6, 2022
And because network security teams lack direct control, coordinating people, policies and infrastructure scattered across the organization has become impossible to get done in a timely manner. Software-defined everything is the mantra and mushrooming complexity is the result.

The Last Watchdog
OCTOBER 31, 2022
But there’s something you can do to get better at striking it: build that balance into your network testing and policy management. Why do so many businesses struggle to balance network security and user experience? Security has always been a moving target, with new threat vectors emerging all the time. Navigating threats.

The Last Watchdog
OCTOBER 23, 2024
INE Security recommends implementing strong password policies that require the use of complex passwords and regular updates. Tip 3: Securing and Monitoring the Network Small businesses often overlook network security, leaving them vulnerable to attacks.

The Last Watchdog
JUNE 16, 2022
Jackson Shaw is chief strategy officer at Clear Skye , an Identity Governance and Administration (IGA) software company focused on enterprise identity access and risk management. With knowledge comes power, and with this research, we have the power to implement better approaches for identity management and beyond. About the essayist.

The Last Watchdog
MAY 18, 2021
To make matters more difficult, implementing new security software and processes to address these issues is another big hurdle, often causing disruption—and not the good kind. By doing this, businesses can ensure they’re keeping security top of mind, while arming employees with the tools they need to get work done.

The Last Watchdog
JUNE 27, 2022
This notorious incident highlights the security risks associated with open-source software, and the challenges of protecting web applications against zero day attacks. To improve web application security, there are basic steps an organization should take: •Security test earlier in the development cycle.

eSecurity Planet
APRIL 26, 2024
Network security architecture is a strategy that provides formal processes to design robust and secure networks. Effective implementation improves data throughput, system reliability, and overall security for any organization. or segregated as cloud or network attached storage (NAS).

Tech Republic Security
MAY 26, 2022
Looking to secure your network? Microsoft Defender and Trellix are two of the most popular endpoint detection and response software options. The post Microsoft Defender vs Trellix: EDR software comparison appeared first on TechRepublic. Compare the features of these EDR tools.

eSecurity Planet
NOVEMBER 12, 2024
Norton has multiple training videos and help articles for using the software, and it offers phone, email, and chat options for customer support. If you’re looking to protect your entire home network, learn more about overall network security. On the usability side, it supports Mac, Windows, Android, and iOS devices.

eSecurity Planet
DECEMBER 10, 2023
The consistent implementation of firewall best practices establish a strong defense against cyber attacks to secure sensitive data, protect the integrity and continuity of business activities, and ensure network security measures function optimally. Why It Matters By restricting access, this strategy mitigates potential damage.

Schneier on Security
MAY 16, 2024
A separate allow list will contain IP address subnets that clients need to run authorized software. .” By default, the firewall will deny resolutions to all domains except those enumerated in allow lists. Key to making this work at scale inside an organization with rapidly changing needs.

Security Affairs
OCTOBER 21, 2024
It provides a range of development resources, including SDKs (Software Development Kits), documentation, sample code, and learning materials for networking, security, and cloud infrastructure. for customers to use as needed.

Security Boulevard
APRIL 28, 2025
True Scale Application Security enables organizations to scale their business without compromising on security, speed, accuracy, and compliance. The post AI avalanche: Taming software risk with True Scale Application Security appeared first on Blog.

Adam Levin
JULY 6, 2022
A firewall is a network security device or program designed to prevent unauthorized and malicious internet traffic from entering a private network or device. Firewalls can be software- or hardware-based. A software firewall is a program installed on a computer that monitors incoming traffic entering through ports.

Security Boulevard
DECEMBER 8, 2023
Newly discovered cracked applications being distributed by unauthorized websites are delivering Trojan-Proxy malware to macOS users who are looking for free or cheap versions of the software tools they want. The post Trojan Malware Hidden in Cracked macOS Software, Kaspersky Says appeared first on Security Boulevard.

SecureWorld News
NOVEMBER 12, 2024
This advisory highlights specific vulnerabilities and offers guidance to mitigate risks for software developers and end-user organizations. The aim is to help organizations secure systems and strengthen defenses against today's persistent and complex cyber threats.

Krebs on Security
JUNE 8, 2023
It’s not often that a zero-day vulnerability causes a network security vendor to urge customers to physically remove and decommission an entire line of affected hardware — as opposed to just applying software updates. The Barracuda Email Security Gateway (ESG) 900 appliance. Campbell, Calif.

Security Boulevard
DECEMBER 12, 2023
The post Snyk Launches ASPM Platform to Secure Software Supply Chains appeared first on Security Boulevard. Snyk's ASPM platform promises to bridge the divide between cybersecurity teams and application developers.

Security Affairs
DECEMBER 30, 2024
It provides a range of development resources, including SDKs (Software Development Kits), documentation, sample code, and learning materials for networking, security, and cloud infrastructure. for customers to use as needed.

Security Boulevard
JULY 16, 2024
The post Patagonia Sued for Using AI-Based Software to Analyze Customer Calls appeared first on Security Boulevard.

Security Boulevard
FEBRUARY 7, 2024
The post Google Pushes Software Security Via Rust, AI-Based Fuzzing appeared first on Security Boulevard. The donation supports the.

eSecurity Planet
OCTOBER 6, 2023
That makes email security software a worthwhile investment for organizations of all sizes. We analyzed the market for email security tools and software to arrive at this list of 7 top email security solutions, including their standout features, limitations and ideal use cases, followed by issues prospective buyers should consider.

Penetration Testing
NOVEMBER 18, 2024
Palo Alto Networks has issued critical advisories regarding two actively exploited vulnerabilities in their PAN-OS software, posing significant risks to organizations relying on the platform for network security.
Security Boulevard
SEPTEMBER 24, 2024
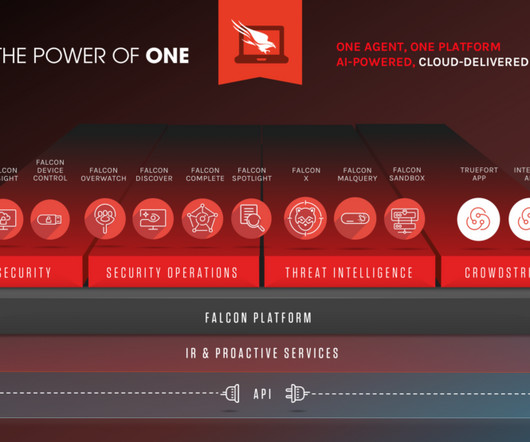
’s software outage that wreaked havoc with key sectors of the global digital. Lawmakers Over Faulty Software Update appeared first on Security Boulevard. During a hearing Tuesday, federal lawmakers reacted with measured outrage at CrowdStrike Inc.’s The post CrowdStrike Gets Grilled By U.S.

Security Boulevard
JANUARY 10, 2025
Giant education software provider PowerSchool reported that hackers using compromised credentials access a database and stole student and teacher data in an attack that the company said was not ransomware, though a ransom apparently was paid. Affected K-12 school districts are scrambling to alert parents and staffs.

Schneier on Security
MARCH 19, 2020
Handing people VPN software to install and use with zero training is a recipe for security mistakes, but not using a VPN is even worse. Worrying about network security seems almost quaint in the face of the massive health risks from COVID-19, but attacks on infrastructure can have effects far greater than the infrastructure itself.

The Last Watchdog
AUGUST 19, 2022
A user gets continually vetted, per device and per software application — and behaviors get continually analyzed to sniff out suspicious patterns. This new approach is required — now that software-defined resources scattered across hybrid and public clouds have come to rule the day.

Tech Republic Security
OCTOBER 17, 2023
The number of devices exposing the web UI on the internet, a timeline and technical details about this malicious activity, and tips for mitigating this zero-day threat are featured.

The Last Watchdog
JULY 19, 2023
We discussed how the boundaries between in-company and out-of-company IT infrastructure have become increasingly blurred making network security more challenging than ever. Yokohama observed that once clearly defined network boundaries have all but disappeared, making network security a very difficult challenge.

The Last Watchdog
MAY 31, 2022
Vulnerability management, or VM, has long been an essential, if decidedly mundane, component of network security. Advanced VM tools and practices are rapidly emerging to help companies mitigate a sprawling array of security flaws spinning out of digital transformation. Related: Log4J’s long-run risks.

IT Security Guru
JANUARY 9, 2025
With the continued evolution of these risks, IT leaders must adapt by implementing a multi-layered approach to security, staying one step ahead of attackers. Key elements in protecting against AI-driven threats include timely software updates, network security improvements and strong password policies.

eSecurity Planet
OCTOBER 18, 2024
Security Engineer Security engineers build secure systems. They install technologies like firewalls and intrusion detection, keep software up to date, enforce security standards, and choose protocols and best practices. Security is embedded within the software development lifecycle, changing the skillset required.

The Last Watchdog
JUNE 28, 2022
This is so, despite the fact that the fundamental design of a VPN runs diametrically opposed to zero trust security principles. I had the chance to visit with David Holmes, network security analyst at Forrester, to learn more about how this dichotomy is playing out as companies accelerate their transition to cloud-centric networking.

The Hacker News
APRIL 13, 2024
Threat actors have been exploiting the newly disclosed zero-day flaw in Palo Alto Networks PAN-OS software dating back to March 26, 2024, nearly three weeks before it came to light yesterday.
Security Boulevard
FEBRUARY 14, 2025
A Chinese threat actor who targeted an Asian software company used the same toolset for the ransomware attack that was found in multiple cyberespionage incidents, leaving Symantec analysts to believe the hacker was a Chinese spy who used the malicious tools to earn some money on the side.

SecureList
APRIL 21, 2025
Fake CAPTCHA distribution vectors Fake CAPTCHA distribution scheme There are two types of resources used to promote fake CAPTCHA pages: Pirated media, adult content, and cracked software sites. The attackers create Telegram channels with names containing keywords related to cryptocurrencies or pirated content, such as software, movies, etc.

SecureList
DECEMBER 9, 2024
A software update in April caused problems in a number of distributions, such as Red Hat, Debian and Rocky. Linux is the operating system used by many key infrastructure and security facilities. The issue serves as a reminder of the potential risks inherent in widely used software. Why does it matter? Why does it matter?

Krebs on Security
OCTOBER 8, 2020
There’s an old adage in information security: “Every company gets penetration tested, whether or not they pay someone for the pleasure.” ” Many organizations that do hire professionals to test their network security posture unfortunately tend to focus on fixing vulnerabilities hackers could use to break in.

The Last Watchdog
MARCH 4, 2024
These worrying statistics underscore the need to be more proactive in preventing security breaches. Keep software updated. Outdated software and operating systems are known risk factors in cybersecurity. Nonprofits can bolster their network security by insisting on strong login credentials.

Tech Republic Security
OCTOBER 24, 2023
The vulnerabilities, one of which was rated critical and one of which was rated highly severe, affect Cisco IOS XE software.

The Last Watchdog
OCTOBER 25, 2021
Traditional network security solutions, such as firewalls, are not effective at detecting and stopping lateral attack movement – and that’s where the real damage is done. About the essayist: Ofer Israeli is Founder and CEO of Illusive , a supplier of advanced network security systems.

Security Boulevard
MARCH 9, 2025
Microsoft Engineer's Transition to Cybersecurity Ankit Masrani, a 36-year-old software engineer, successfully transitioned into a cybersecurity role at Microsoft. With a background in IT and a Master's degree in computer science, Masrani secured an internship and later a full-time position at AWS, focusing on data and network security.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content