Network Security Architecture: Best Practices & Tools
eSecurity Planet
APRIL 26, 2024
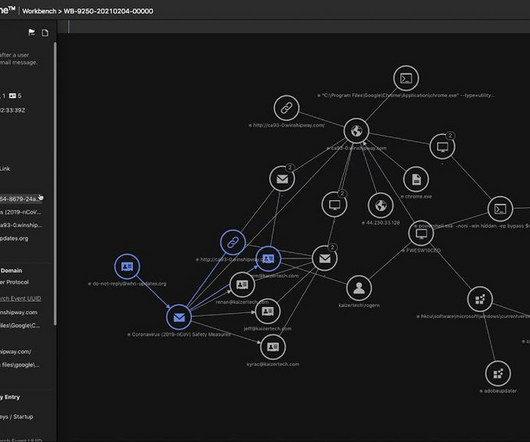
Network security architecture is a strategy that provides formal processes to design robust and secure networks. Effective implementation improves data throughput, system reliability, and overall security for any organization. or segregated as cloud or network attached storage (NAS).















































Let's personalize your content