Setting Up Your Network Security? Avoid These 4 Mistakes
Tech Republic Security
OCTOBER 4, 2024
Learn how to execute the fundamentals, harden your defenses, and protect your business's network security with no high-tech software.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
OCTOBER 4, 2024
Learn how to execute the fundamentals, harden your defenses, and protect your business's network security with no high-tech software.

The Last Watchdog
OCTOBER 23, 2024
Tip 2: Implementing Strong Password Policies Weak passwords can be easily compromised, giving attackers access to sensitive systems and data. LastPass reports that 80% of all hacking-related breaches leveraged either stolen and/or weak passwords.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
MAY 25, 2021
Trend Micro fixed some flaws in Trend Micro Home Network Security devices that could be exploited to elevate privileges or achieve arbitrary authentication. Trend Micro fixed three vulnerabilities in Home Network Security devices that could be exploited to elevate privileges or achieve arbitrary authentication.

Tech Republic Security
AUGUST 4, 2022
Windows finally includes a tool to manage local admin passwords, but admins will still need to do some work to make it useful. The post Protect domain-joined computer passwords with Windows’ Local Administrator Password Solution appeared first on TechRepublic.
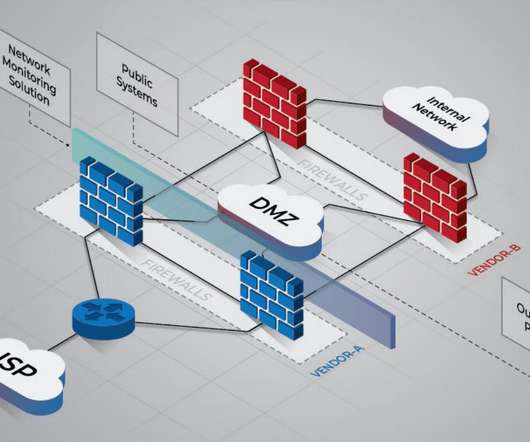
eSecurity Planet
MARCH 4, 2022
National Security Agency (NSA) released comprehensive network security guidance on March 3, on the same day that the Cybersecurity and Infrastructure Security Agency (CISA) released its longest-ever list of exploited vulnerabilities. Change default passwords and remove unnecessary accounts. The post U.S.
The Hacker News
SEPTEMBER 9, 2021
Network security solutions provider Fortinet confirmed that a malicious actor had unauthorizedly disclosed VPN login names and passwords associated with 87,000 FortiGate SSL-VPN devices. These credentials were obtained from systems that remained unpatched against CVE-2018-13379 at the time of the actor's scan.

eSecurity Planet
APRIL 26, 2024
Network security architecture is a strategy that provides formal processes to design robust and secure networks. Effective implementation improves data throughput, system reliability, and overall security for any organization.

Security Boulevard
JANUARY 16, 2023
NortonLifeLock is warning customers their passwords are loose. The post Another Password Manager Breach: NortonLifeLock Apes LastPass appeared first on Security Boulevard. First LastPass, now this?

CyberSecurity Insiders
OCTOBER 13, 2021
Problems arise for businesses when they base their access management programs entirely around passwords, however. Such programs overlook the burden that passwords can cause to users as well as to IT and security teams. Passwords: An unsustainable business cost. Users have too many passwords to remember on their own.

eSecurity Planet
MARCH 8, 2022
The average internet user has somewhere around 100 accounts, according to NordPass research, meaning they have to track 100 different passwords or risk using the same one over and over. Users can share password files securely with encrypted transmissions. Vault health reports Directory sync Secure password sharing.

Security Boulevard
APRIL 30, 2024
The UK’s Product Security and Telecommunications Infrastructure Act aims to improve the security of net-connected consumer gear. The post Brits Ban Default Passwords — and More IoT Stupidity appeared first on Security Boulevard. Nice Cup of IoTea?

eSecurity Planet
AUGUST 27, 2021
Employing a zero trust model instead, Jain said, ensures that endpoints only get network access post-authentication – and recognizes that most traffic will likely be to the Internet or a private data center, limiting lateral movement within the network via default deny policies (with exceptions for printers, conferencing, etc.).

Security Boulevard
MARCH 8, 2021
There’s a t-shirt that reads, “My password is the last 20 digits of Pi.” but every single password generator would flag that password as “weak.” There are no letters or symbols, and that would create a password without all the necessary criteria. It’s funny – who would ever guess that? – This is only one.

eSecurity Planet
MARCH 17, 2023
Whether you’re operating a global enterprise network or a small family business, your network’s security needs to be optimized with tools, teams, and processes to protect customer data and valuable business assets. Many of these tools protect resources connected to networks, thus shutting down threats as early as possible.

Security Boulevard
JULY 9, 2024
Credential crunch: Ten billion plain-text passwords in a file—sky falling or situation normal? The post Biggest Ever Password Leak — but is ObamaCare’s RockYou2024 Really NEW? appeared first on Security Boulevard.

Tech Republic Security
FEBRUARY 8, 2022
Remote password changes on company-issued workstations can sometimes yield chaotic results. The post 10 best practices for Windows workstation password changes over a VPN appeared first on TechRepublic. Follow these best practices to help ensure you keep working.

Security Boulevard
AUGUST 8, 2022
Since 2017, if you’ve invited anyone to a Slack workspace, your password has leaked. The post Slack App Leaked Hashed User Passwords for 5 YEARS appeared first on Security Boulevard. How could this have happened?

Security Boulevard
OCTOBER 15, 2021
A report published this week by Cisco’s Duo Security unit found the use of both multifactor authentication (MFA) and biometric authentication is on the rise as alternatives to passwords. The post Cisco Report Shows Shift Away from Traditional Passwords appeared first on Security Boulevard.

Schneier on Security
DECEMBER 15, 2020
Logs from the Exchange server showed that the attacker provided username and password authentication like normal but were not challenged for a second factor through Duo. After successful password authentication, the server evaluated the duo-sid cookie and determined it to be valid.

SC Magazine
MARCH 2, 2021
House Oversight and Homeland Security committees last week, SolarWinds’s former and current CEOs blamed an intern for creating a weak FTP server password and leaking it on GitHub – an act which may or may not have contributed to a supply chain hack that impacted users of the tech firm’s Orion IT performance monitoring platform.

Security Boulevard
FEBRUARY 22, 2023
US DoD Server Had no Password — 3TB of Sensitive Data Leaked appeared first on Security Boulevard. Sensitive military data found on unprotected Microsoft Azure server. Defense Department email store left insecure for at least 11 days. The post Surprise!

eSecurity Planet
MARCH 14, 2023
Network security creates shielded, monitored, and secure communications between users and assets. Securing the expanding, sprawling, and sometimes conflicting collection of technologies that make up network security provides constant challenges for security professionals.

Security Boulevard
JULY 25, 2022
Windows to Block Password Guessing — by Default appeared first on Security Boulevard. Brute-force guessing of Windows credentials is a common entry point for hackers. After 27 years, Microsoft is finally fixing the dumb default that allows it. The post Finally!

IT Security Guru
JANUARY 9, 2025
Cybercriminals weaponise AI to speed up and scale traditional attack tactics, such as phishing and password cracking, while also creating entirely new forms of cyber threats. With the continued evolution of these risks, IT leaders must adapt by implementing a multi-layered approach to security, staying one step ahead of attackers.

Security Boulevard
MARCH 22, 2023
Poor password practices continue to put businesses at risk, with nearly 90% of passwords used in successful attacks consisting of 12 characters or less, indicating additional security measures are required to protect access to sensitive data. The report.

Duo's Security Blog
SEPTEMBER 6, 2023
But conventional protection solutions, like password security, fall short when it comes to efficacy. That’s why many tech companies are turning to passkeys as a more secure and convenient replacement. This will allow them to sign in to their Apple ID sign-in pages with Face ID or Touch ID instead of their password.
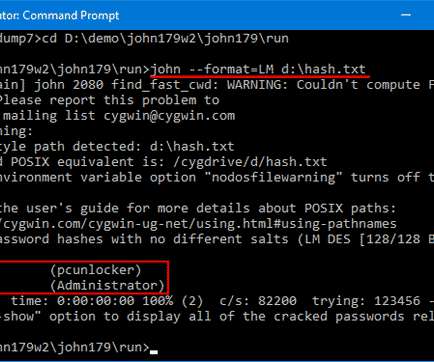
eSecurity Planet
JANUARY 31, 2023
John the Ripper is a popular password cracking tool that can be used to perform brute-force attacks using different encryption technologies and helpful wordlists. It’s often what pen-testers and ethical hackers use to find the true passwords behind hashes. For our example, we won’t need a powerful machine. Or at least a good GPU.

Security Boulevard
AUGUST 15, 2023
Enterprises are developing strategies now to protect identities from being stolen and abused even as a true passwordless future is slowly coming into view, according to Joseph Carson, chief security scientist and advisory CISO at privileged access manager (PAM) vendor Delinea.

SecureWorld News
NOVEMBER 12, 2024
These vulnerabilities span a range of technologies, from network security appliances to widely used software applications. An unauthenticated user can access sensitive data such as admin passwords, mail server credentials, and license keys. This exploit occurs even without user interaction.

Krebs on Security
JUNE 29, 2023
Nikita Kislitsin , formerly the head of network security for one of Russia’s top cybersecurity firms, was arrested last week in Kazakhstan in response to 10-year-old hacking charges from the U.S. Department of Justice. Nikulin is currently serving a seven-year sentence in the U.S. prison system.

Security Boulevard
FEBRUARY 5, 2024
Businesses are striving to create better customer experiences, but reliance on password-based authentication is holding them back. The post Are Passwords Killing Your Customer Experience? appeared first on Security Boulevard.

SecureWorld News
FEBRUARY 10, 2025
The good news is that security teams can learn to anticipate these events and know exactly what to do to stop or prevent them. Why network security matters Before zooming in on specific attack methods, it's important to understand what network security is and why it's a top priority. How can they do that?

Security Boulevard
MARCH 24, 2025
A Cato Networks threat researcher with little coding experience was able to convince AI LLMs from DeepSeek, OpenAI, and Microsoft to bypass security guardrails and develop malware that could steal browser passwords from Google Chrome.

Security Affairs
DECEMBER 4, 2024
The government agencies released a guide that advises telecom and critical infrastructure defenders on best practices to strengthen network security against PRC-linked and other cyber threats. Strong segmentation with firewalls and DMZs, securing VPN gateways, and ensuring encrypted traffic with TLS v1.3

SecureWorld News
MARCH 27, 2025
Encryption Whenever you are sharing sensitive personal or business information (from passwords to client details), encryption should be mandatory. Encryption keeps your data confidential and secure, making it difficult for hackers to access information you're sharing across digital channels. It's time to change it.

Security Boulevard
DECEMBER 21, 2021
You enter your password, then you get a prompt to enter a code or pin that’s sent to your phone number. The post Why Using SMS Authentication for 2FA Is Not Secure appeared first on Enterprise Network Security Blog from IS Decisions. After you type in the code, you’re in. Simple, right? We all have … Continued.

The Last Watchdog
JANUARY 27, 2025
Structured learning paths cover essential skills in network security implementation and monitoring system setup, giving users real-world experience with the tools and techniques required for CMMC compliance. Organizations can use this checklist to track progress and identify areas requiring attention before assessment.

Security Boulevard
APRIL 22, 2024
Securing these accounts with strong passwords is critical. However, a recent spike in brute force attack emphasizes the need for even stronger security measures. A recent report warns of a significant increase in […] The post Is Your Password Strong Enough? The post Is Your Password Strong Enough?

Security Boulevard
FEBRUARY 5, 2024
Remote access software maker AnyDesk has revoked all security-related certificates and is urging users to change their passwords in the wake of a cyberattack that compromised some of its systems. The post AnyDesk Revokes Certificates, Urges Password Changes After Attack appeared first on Security Boulevard.

eSecurity Planet
AUGUST 21, 2024
Navigating the complexities of password management can be challenging, especially if you’re new to it. LastPass, a leading password manager, offers a robust solution for securely storing and managing your organization’s digital assets. Enter your email address and create a strong master password.

Security Affairs
JUNE 21, 2021
The group published the link to 13 password-protected archives, allegedly containing sensitive data stolen from the chipmaker. Attention Password for the Archives: XXXXXXXXXXX#1JLDiw8″ reads the post published by the group on its leak site. !!Inside This information should not be accessible from the compromised network.

Security Boulevard
AUGUST 30, 2024
Permalink The post USENIX Security ’23 – Checking Passwords On Leaky Computers: A Side Channel Analysis Of Chrome’s Password Leak Detect Protocol appeared first on Security Boulevard. Originating from the conference’s events situated at the Anaheim Marriott ; and via the organizations YouTube channel.

SecureWorld News
MAY 28, 2024
Threat actors are targeting Check Point Remote Access VPN devices in an ongoing campaign to breach enterprise networks, the company has warned in a new advisory. We have recently witnessed compromised VPN solutions, including various cyber security vendors.

Security Affairs
FEBRUARY 4, 2021
The provider of network security products Stormshield discloses data breach, threat actors stole information on some of its clients. Stormshield is a major provider of network security products to the French government, some approved to be used on sensitive networks. ” continues Stormshield.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content