South African telecom provider Cell C disclosed a data breach following a cyberattack
Security Affairs
APRIL 13, 2025
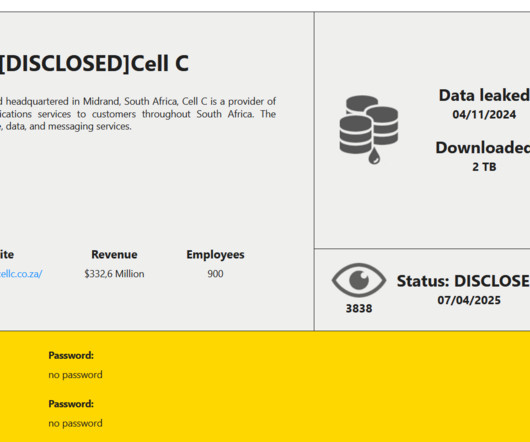
Cell C, one of the biggest telecom providers in South Africa confirms a data breach following a 2024 cyberattack. Cell C is the fourth-largest mobile network operator in South Africa, , after Vodacom, MTN, and Telkom. They continue to monitor for potential data misuse and urge vigilance against fraud, phishing, and identity theft.














Let's personalize your content