5 Best VPNs for Social Media in 2024 (Free & Paid VPNs)
Tech Republic Security
MARCH 7, 2024
Which is the best VPN for social media? Use our guide to compare key features, pros, cons, and more.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
MARCH 7, 2024
Which is the best VPN for social media? Use our guide to compare key features, pros, cons, and more.

Malwarebytes
MARCH 11, 2021
Virtual Private Networks ( VPN s) are popular but often misunderstood. VPNs are for illegal activity. Some people think that VPNs are only useful for doing things like torrenting, accessing geo-locked content, or getting around work/school/government firewalls. I don’t need a mobile VPN. My VPN won’t let me watch Netflix.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
AUGUST 19, 2020
But one increasingly brazen group of crooks is taking your standard phishing attack to the next level, marketing a voice phishing service that uses a combination of one-on-one phone calls and custom phishing sites to steal VPN credentials from employees. The employee phishing page bofaticket[.]com. Image: urlscan.io. ” SPEAR VISHING.
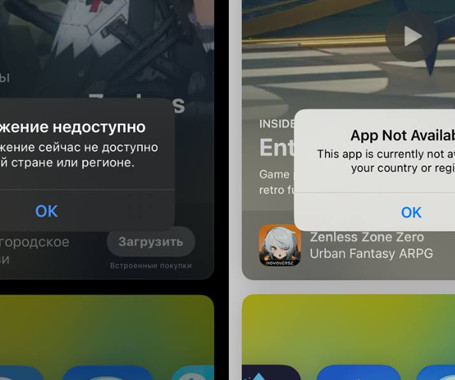
The Hacker News
JULY 7, 2024
Apple removed a number of virtual private network (VPN) apps in Russia from its App Store on July 4, 2024, following a request by Russia's state communications watchdog Roskomnadzor, Russian news media reported. It's worth noting that NordVPN previously shut
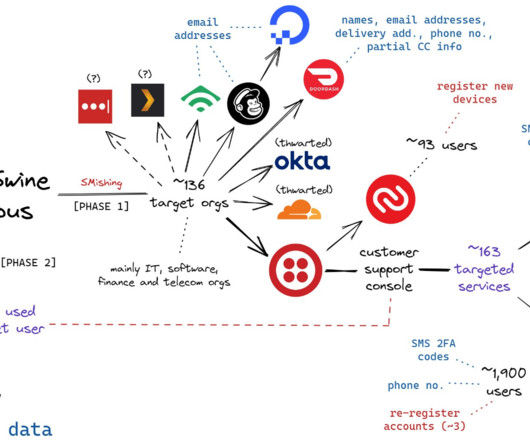
Krebs on Security
NOVEMBER 21, 2024
Some SMS phishing messages told employees their VPN credentials were expiring and needed to be changed; other phishing messages advised employees about changes to their upcoming work schedule. The targeted SMS scams asked employees to click a link and log in at a website that mimicked their employer’s Okta authentication page.

Security Affairs
DECEMBER 2, 2021
Russia’s internet watchdog, ‘Roskomnadzor’, has announced the ban of other VPN products, 15 VPN services are now illegal in Russia. Russian communications watchdog Roskomnadzor tightens the control over the Internet and blocked access to six more VPN services. SecurityAffairs – hacking, VPN services). Pierluigi Paganini.

Krebs on Security
AUGUST 21, 2020
The advisory came less than 24 hours after KrebsOnSecurity published an in-depth look at a crime group offering a service that people can hire to steal VPN credentials and other sensitive data from employees working remotely during the Coronavirus pandemic. authenticate the phone call before sensitive information can be discussed.

CSO Magazine
NOVEMBER 3, 2022
A new espionage campaign, dubbed SandStrike, has been detected using malicious VPN apps to load spyware on Android devices, cybersecurity company Kaspersky reports. To read this article in full, please click here
Krebs on Security
JULY 18, 2022
911 says its network is made up entirely of users who voluntarily install its “free VPN” software. Residential proxy services are often marketed to people seeking the ability to evade country-specific blocking by the major movie and media streaming providers. “The free VPN apps, and the other is trojanized torrents.

Troy Hunt
APRIL 17, 2018
Often, you'll see this pattern play out ad nauseam as the organisation involved takes the shotgun approach of blasting their message out over and over again: When you look for a VPN, you really want to be confident they're responsible, ethical and behave in a professional manner. link] — Troy Hunt (@troyhunt) April 12, 2018.
Security Affairs
NOVEMBER 3, 2024
The botnet operators are targeting multiple SOHO devices and VPN appliances, including TP-LINK, Zyxel, Asus, D-Link, and Netgear, exploiting both known and previously unknown vulnerabilities. The operators maintain the botnet to launch distributed brute-force attacks on VPNs, Telnet, SSH, and Microsoft 365 accounts.

Malwarebytes
FEBRUARY 27, 2021
VPNs have been a subject of deliberation for a long time. I think the pandemic has made it clear that, yes, using a VPN is useful, even necessary, most especially for those working remotely. We’re going to take a look at free VPNs and paid VPNs in general. The honest free VPN. The mystery free VPN.
Krebs on Security
NOVEMBER 2, 2021
.” In the first week of September, Groove posted on its darknet blog nearly 500,000 login credentials for customers of Fortinet VPN products, usernames and passwords that could be used to remotely connect to vulnerable systems. “It’s so funny to read Twitter and the news these days But the result is great so far.

SecureBlitz
MAY 19, 2021
If you are looking for the best VPN for Nigeria, this post reveals the best options. Also, in the end, we will reveal the VPN service providers that have VPN servers in Nigeria. VPN in Nigeria is a must-use based on the recent clamor of Nigeria’s ruling political class to regulate social media usage by.

Pen Test Partners
AUGUST 29, 2024
Secure networks : Avoid using untrusted public Wi-Fi to access social media accounts, instead, use mobile data. If you have to use a trusted VPN then use that, but be aware a VPN doesn’t make your connection secure it just moves the threat to the VPN provider. Multi-Factor authentication (MFA). Why do I need it?

Malwarebytes
APRIL 11, 2022
A credential-stealing Windows-based malware, Spyware.FFDroider , is after social media credentials and cookies, according to researchers at ThreatLabz. The malware also plans to steal saved VPN/dial up credentials from the AppdataMicrosoftNetworkConnectionsPbkrasphone.pbk and Pbkrasphone.pbk phonebooks if present. Social media.

Hot for Security
FEBRUARY 16, 2021
A virtual private network (VPN) provides anonymity and digital privacy by creating a secure and private tunnel between the user and the online destinations he visits. A VPN encrypts computer traffic, masking your IP address and location, preventing snoopers or hackers from viewing or intercepting your data. Netflix and chill anywhere.

CyberSecurity Insiders
FEBRUARY 16, 2021
Published in collaboration with the Cybersecurity Insiders, the report includes findings from a global survey of more than 350 cybersecurity professionals on the current state of remote access environments, the rise in VPN vulnerabilities, and the role zero-trust security models play in providing access to enterprise applications.

Malwarebytes
MAY 24, 2021
In just the past year, free VPN for Android apps have exposed the data of as many as 41 million users, revealing consumers’ email addresses, payment information, clear text passwords, device IDs, and more. All these people that work on [the VPN service], nobody is going to do it for free. There is no best free VPN for Android.

Identity IQ
APRIL 22, 2021
If you want to help secure your digital identity, a virtual private network (VPN) is a great tool you can use for added online privacy. In this guide, we discuss VPNs in detail, including how they work, how they protect you and why you should use one when browsing the web. What is a VPN? How does a VPN Work?

Krebs on Security
NOVEMBER 21, 2020
The phishers often will explain that they’re calling from the employer’s IT department to help troubleshoot issues with the company’s email or virtual private networking (VPN) technology. Restrict VPN access hours, where applicable, to mitigate access outside of allowed times.

SiteLock
AUGUST 27, 2021
Setting up a VPN can ensure your data is safe when you’re not using a trusted connection by encrypting data as it’s transmitted across shared or public networks, keeping your sensitive information from being exposed. What to Look for in a VPN. The first feature to look for in a VPN is military-grade (256-bit) encryption.
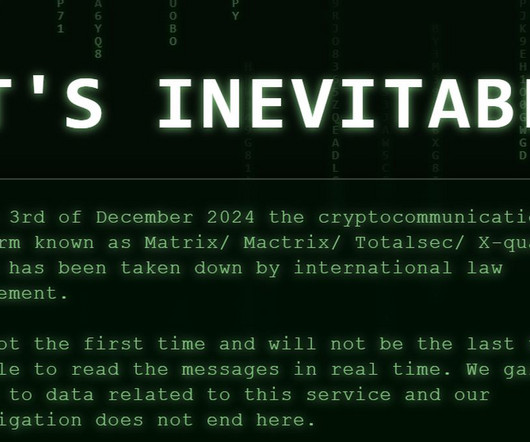
Malwarebytes
DECEMBER 9, 2024
Although I appreciated the hint of the splash page to the media franchise The Matrix. Keep your online privacy yours by using Malwarebytes Privacy VPN. We dont want US citizens looking for an encrypted messaging service to shy away from apps built on the Matrix protocol just because it has the same name.

The Hacker News
JUNE 18, 2021
Russia's telecommunications and media regulator Roskomnadzor (RKN) on Thursday introduced restrictions on the operation of VyprVPN and Opera VPN services in the country. "In

SC Magazine
APRIL 8, 2021
Kaspersky reported how recent attacks against a series of European industrial networks were accomplished at a vulnerability in Fortinet’s FortiGate VPN. Kaspersky is the first to report how those attacks were accomplished: a vulnerability in Fortinet’s FortiGate VPN. Alexxsun / CC BY-SA 4.0 ).

Security Affairs
JULY 13, 2021
NetBlocks reported partial disruption to social media and messaging platforms in Cuba from 12 July 2021 shortly after Cubans went to the streets to protest the government. VPN services have yet to be blocked in the country, allowing citizens to bypass internet censorship. Follow me on Twitter: @securityaffairs and Facebook.

Malwarebytes
MARCH 29, 2021
In addition, we speak to Malwarebytes senior security researcher JP Taggart about the importance of trusting your VPN. But obscuring your Internet activity—including the websites you visit, the searches you make, the files you download—doesn’t mean that a VPN magically disappears those things. Source: ComputerWeekly).

Security Affairs
OCTOBER 29, 2024
Change passwords : After malware removal, update passwords for key accounts (email, banking, work, social media) and enable two-factor authentication. Consider extra security layers : Use additional protection like a VPN for safer online activity. Use a password manager : Simplifies managing strong, unique passwords across accounts.

Security Affairs
JANUARY 18, 2022
Some administrators and users reported problems with L2TP VPN connections on Windows 10 after installing the recent Windows 10 and Windows 11 cumulative updates. The post Microsoft releases Windows out-of-band emergency fixes for Win Server, VPN issues appeared first on Security Affairs. Pierluigi Paganini.

Webroot
MARCH 3, 2025
Common attacks to consumer protection Identity theft and fraud Some common types of identity theft and fraud include account takeover fraud , when criminals use stolen personal information such as account numbers, usernames, or passwords to hijack bank accounts, credit cards, and even email and social media accounts.

Approachable Cyber Threats
SEPTEMBER 30, 2021
You can’t access that app someone mentioned, so you ask them and they tell you to “just use the VPN.” And why can you access the app after using the VPN, but you couldn’t before? A Virtual Private Network, or VPN, is a technology that allows you to connect your device to another IT network. This is where a VPN comes in.

SC Magazine
MAY 28, 2021
FireEye Mandiant, working in in tandem with the Cybersecurity and Infrastructure Security Agency and Ivanti, reported details of 16 malware families exclusively designed to infect Ivanti Pulse Connect Secure VPN appliances, and used by several cyber espionage groups believed to be affiliated with the Chinese government.

Krebs on Security
SEPTEMBER 17, 2020
Earlier this year, for example, the group was tied to a particularly aggressive malware campaign that exploited recent vulnerabilities in widely-used networking products, including flaws in Cisco and D-Link routers, as well as Citrix and Pulse VPN appliances.

Krebs on Security
APRIL 6, 2022
In fact, the group often announces its hacks on social media. The group of teenagers who hacked Twitter hailed from a community that traded in hacked social media accounts. On top of that, LAPSUS$ has a habit of posting screenshots on social media touting its access to internal corporate tools. ADVANCED PERSISTENT TEENAGERS.

Krebs on Security
FEBRUARY 14, 2022
Wazawaka has since “lost his mind” according to his erstwhile colleagues, creating a Twitter account to drop exploit code for a widely-used virtual private networking (VPN) appliance, and publishing bizarre selfie videos taunting security researchers and journalists. Wazawaka, a.k.a. Matveev, a.k.a. “Orange,” a.k.a.

Schneier on Security
SEPTEMBER 17, 2018
A 2006 document from the Snowden archives outlines successful NSA operations against "a number of "high potential" virtual private networks, including those of media organization Al Jazeera, the Iraqi military and internet service organizations, and a number of airline reservation systems.".

CyberSecurity Insiders
APRIL 18, 2021
As of now, the alliance has approved mobile apps and Virtual Private Network (VPN) services and is planning to include all cloud connected services like social media apps in near future. Google’s Pixel series of phones 4, XL and 4a became the first devices to pass through the IOT certification last year.

Security Affairs
JANUARY 23, 2021
The company was targeted with a coordinated attack on its internal systems, threat actors exploited zero-day vulnerabilities in their VPN solutions, such as NetExtender VPN client version 10.x Below the list of affected products shared by THN: NetExtender VPN client version 10.x x and Secure Mobile Access ( SMA ).

SecureList
MARCH 19, 2025
It grabs account information from VPN and gaming clients, and all kinds of network utilities like ngrok, Playit, Cyberduck, FileZilla and DynDNS. Send your videos to the #MEDIA chat 2. Access to @everyone in the #MEDIA chat 5. Possible compensation in rubles for high traffic MEDIA Criteria: 1. Personal server role 3.
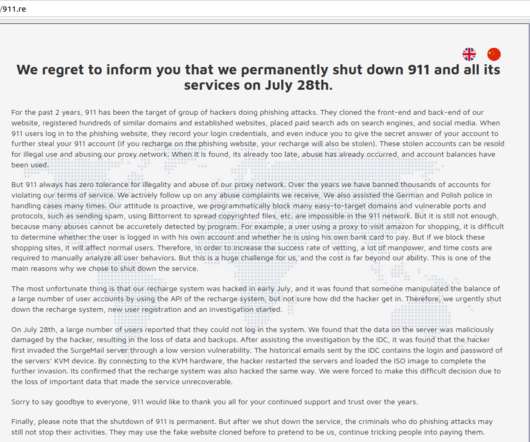
Krebs on Security
JULY 29, 2022
Residential proxy services are often marketed to people seeking the ability to evade country-specific blocking by the major movie and media streaming providers.

eSecurity Planet
NOVEMBER 12, 2024
Aside from antivirus, Norton offers ransomware and hacking protection, privacy monitoring, and a VPN. Even McAfee’s most basic plan includes a VPN, identity monitoring, and text scam detection. I recommend McAfee if you’re looking for features like social media privacy, personal data monitoring, and scans of old internet accounts.

Malwarebytes
APRIL 25, 2025
I also used a VPN so I didnt give away my current location. With social media being used for AI training , it is likely that these results will rapidly gain even more in accuracy. We don’t just report on threats – we help protect your social media Cybersecurity risks should never spread beyond a headline.

The Last Watchdog
JANUARY 3, 2023
With the rise in social media, criminals have more platforms with which to target potential phishing victims. Since many people use the same passwords across social media platforms and for sites for banks or credit cards, a criminal needs access to just one account to gain access to every account.

Krebs on Security
MAY 16, 2023
“Hello Brian Krebs!
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content