Cisco to Acquire Splunk for $28 Billion
eSecurity Planet
SEPTEMBER 21, 2023
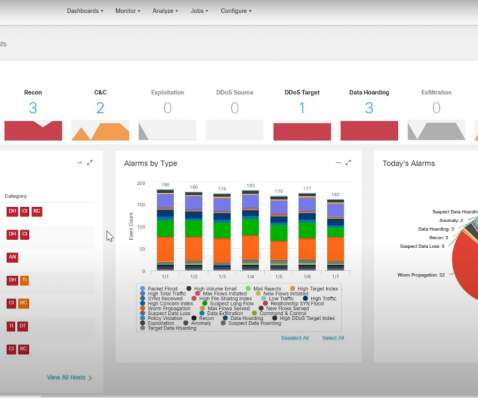
In a blockbuster deal that could shake up the cybersecurity market, Cisco announced this morning that it will acquire Splunk for $28 billion. Why Cisco and Splunk Are a Match Splunk was an early mover in the market for cloud SIEM solutions, which gave it a strong early advantage.




































Let's personalize your content