Hackers are working harder to make phishing and malware look legitimate
Tech Republic Security
MARCH 11, 2020
A Trend Micro report finds that spammers are using public and hosted cloud infrastructure to slip malicious emails past security defenses.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
MARCH 11, 2020
A Trend Micro report finds that spammers are using public and hosted cloud infrastructure to slip malicious emails past security defenses.

Trend Micro
OCTOBER 13, 2024
This group is targeting enterprises in Brazil, deploying banking malware using obfuscated JavaScript to slip past security defenses. Trend Micro researchers have uncovered a surge of malicious activities involving a threat actor group that we track as Water Makara.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

eSecurity Planet
OCTOBER 24, 2023
Malware attacks pose a significant risk to both individuals and businesses, infiltrating computer systems, compromising sensitive data and disrupting operations, leading to financial and data loss — and even extortion. Here are 15 important controls and best practices for preventing malware.

Security Affairs
FEBRUARY 28, 2024
Many of the detections were due to malicious attachments and previously unseen threats, showcasing the importance of using innovative security measures YARA Rules Impact YARA rules were pivotal in detecting millions of malicious attempts spotlighting statistical patterns and malware family indicators.

eSecurity Planet
AUGUST 23, 2023
Spear phishing is a more targeted and effective phishing technique that attempts to exploit specific individuals or groups within an organization. While phishing uses a broader range of tactics, such as mass emailing to random recipients, spear phishing is often well-researched and tailored to high-value targets.

eSecurity Planet
OCTOBER 26, 2023
Antivirus programs and firewalls are pretty good at catching malware before it can infect devices, but occasionally malware can slip through defenses, endangering personal and financial information. We’ll go over malware removal tools and steps, and offer some tips to keep your devices from getting reinfected.
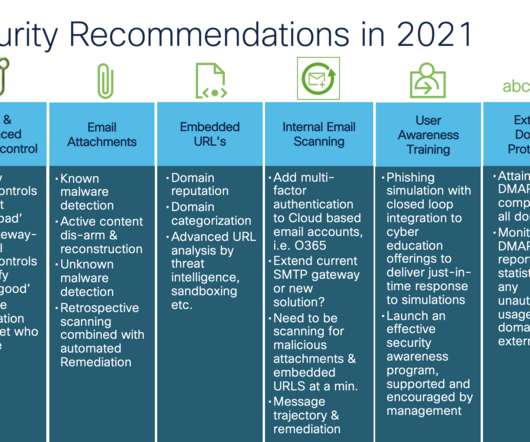
Cisco Security
AUGUST 17, 2021
Now mix in architectural changes that support cloud productivity suites like Microsoft 365 and Google’s G-Suite to accelerate your business to cloud-based email security services. When it comes to safeguarding email against today’s advanced threats like phishing and malware information is power.

Webroot
APRIL 4, 2022
Whether you operate a business or spend time online surfing the web, malware remains a concern. In the last year, 86% of malware remained unique to a PC, which has been consistent for the past few years. High-risk URLs are phishing for your data in the most benign of locations.

eSecurity Planet
OCTOBER 10, 2024
With malware increasingly targeting macOS, many users wonder how to protect their devices best. The answer is simple: invest in the right anti-malware and anti-virus software designed specifically for Mac users in 2025. This guide will explore the essential tools to help you secure your Mac against malware threats.

Hacker Combat
APRIL 6, 2022
The best ransomware protection combines solid, layered security defenses with data backups that an attacker can’t encrypt. Regular updates patch any security vulnerabilities as quickly as possible so hackers won’t exploit them. Several free anti-malware products that detect and block ransomware attacks are available.

eSecurity Planet
OCTOBER 6, 2023
Despite all the advances in cybersecurity, email remains the starting point for the vast majority of cyberattacks, as phishing, malware and social engineering remain effective attack techniques. That makes email security software a worthwhile investment for organizations of all sizes.

eSecurity Planet
SEPTEMBER 16, 2024
AI-Powered Security Tools AI-powered security tools are revolutionizing how organizations approach cybersecurity. These tools use advanced algorithms to protect against various threats, from malware to phishing attacks. They offer real-time analysis and responses, making them a valuable asset in any security strategy.
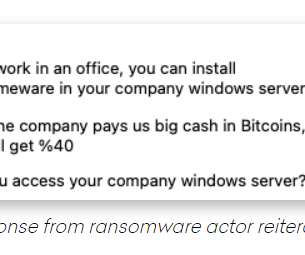
eSecurity Planet
AUGUST 23, 2021
Ransomware attackers, who use myriad methods to get their malware into the systems of businesses large and small in hopes of pulling down millions of dollars, are now going directly to the source. The malware, which also is known as Black Kingdom and DEMON, has been around for a few years and is available for free on GitHub.

CyberSecurity Insiders
FEBRUARY 2, 2022
.–( BUSINESS WIRE )– Menlo Security , a leader in cloud security, today announced it has identified a surge in cyberthreats, termed Highly Evasive Adaptive Threats (HEAT), that bypass traditional security defenses. Since July 2021, Menlo Security has seen a 224% increase in HEAT attacks. minutes.
Security Affairs
NOVEMBER 3, 2022
It focused on deploying POS malware and launching targeted spear-phishing attacks against organizations worldwide. In order to weaken the security defenses installed on the target machine, Black Basta targets installed security solutions with specific batch scripts downloaded into the Windows directory.

eSecurity Planet
AUGUST 20, 2024
Keep Your Software Updated Software updates often come with bug fixes for security vulnerabilities that attacks might exploit. Running outdated software increases the risk of being targeted by malware or other attacks. Enable automatic updates on your operating system, web browser, and apps whenever possible.
eSecurity Planet
JULY 13, 2023
“WormGPT produced an email that was not only remarkably persuasive but also strategically cunning, showcasing its potential for sophisticated phishing and BEC attacks” (screenshot below). ” Just last week, Acronis reported that AI tools like ChatGPT have been behind a 464% increase in phishing attacks this year.

eSecurity Planet
JUNE 28, 2024
Hackers with administrator access can deface websites, steal sensitive data like customer information, or even install malware that can harm visitors’ computers. If a hacker infiltrated a widely used library, they might have administered malware that would be embedded in all plugins using that library.

SiteLock
AUGUST 27, 2021
Even a company with the most sophisticated cybersecurity tools and expert security teams can fall prey to cybercriminals if they overlook one area of vulnerability: their people. In fact, 97% of us can’t tell a phishing email from a legitimate one. Business Email Compromise (BEC) is similar to phishing. billion.

eSecurity Planet
JANUARY 30, 2024
Collaborate with external cloud security specialists or managed service providers to enhance internal capabilities. 8 Common Cloud Storage Security Risks & Mitigations Cloud storage risks include misconfiguration, data breaches, insecure interfaces, DDoS attacks, malware, insider threats, encryption issues, and patching issues.

eSecurity Planet
OCTOBER 8, 2024
Phishing: Among the possible methods used was phishing , where attackers deceive employees into revealing sensitive credentials, allowing them access to internal systems. Learn network security best practices to strengthen your security measures further and avoid such breaches. telecom networks.

eSecurity Planet
JULY 31, 2024
AV software blocks malware, EPP passively prevents threats, and EDR actively mitigates network attacks. Identifies and eliminates known malware. Limited to blocking, quarantining, and removing discovered malware. Individuals and home users: Recommended for personal devices that require basic security against typical threats.
eSecurity Planet
DECEMBER 10, 2023
This can be done through a variety of attacks, such as spear phishing , and may require the attacker to steal multiple sets of credentials before they reach the information they need. Process Injection When threat actors inject malicious code into a standard computing process while it runs, they disguise the malware.

SecureWorld News
NOVEMBER 8, 2023
Whether manifesting itself in a sophisticated phishing email or as a calculated series of conversations between employees and seemingly innocuous or "legitimate" parties with ulterior motives, a social engineering attack can have dire consequences. The average business faces more than 700 of these types of attacks every single year.

Security Boulevard
JULY 7, 2023
Summary Discover the intricate layers of a new sophisticated and persistent malware campaign targeting businesses in the LATAM region delivering the TOITOIN Trojan. Delve into the multi-stage attack methodology, from deceptive phishing emails to custom-built modules, as we dissect its techniques and shed light on its impact.

SiteLock
AUGUST 27, 2021
Most simply don’t have the resources to employ a dedicated cybersecurity team or invest in comprehensive security awareness training, leaving employees more vulnerable to phishing attacks and other scams. That means you need to have a plan for responding to attacks that break through even the most secure defenses.

eSecurity Planet
APRIL 23, 2021
Standalone security products are not enough to maintain the security posture of an entire organization. Between malware , phishing attacks , zero-day threats, advanced persistent threats , reconnaissance and brute force attacks, hackers are looking for any and every avenue into a network. EDR benefits.

eSecurity Planet
AUGUST 22, 2024
Attackers steal cookies through phishing, malware, and MITM attacks, resulting in data theft, financial loss, and identity theft. Long-term threats need a serious effort to secure stolen data and safeguard your privacy against further misuse.

Security Boulevard
APRIL 30, 2021
Almost every week we see new examples of highly sophisticated organizations and enterprises falling victim to another nation-state cyberattack or other security breach. This presents problems for traditional security solutions because most approaches are based on pattern matching, using signatures of past malware or malicious actions.

eSecurity Planet
AUGUST 3, 2023
” Also read: ChatGPT Security and Privacy Issues Remain in GPT-4 Growing AI Cybercrime Potential Kelley, who also exposed WormGPT in early July, noted that FraudGPT shares the same foundational capabilities as WormGPT and might have been developed by the same people, but FraudGPT has the potential for even greater malicious use.

eSecurity Planet
APRIL 29, 2022
Standalone cybersecurity tools are not enough to maintain the security posture of an entire organization. Between malware , phishing attacks , zero-day threats , advanced persistent threats , reconnaissance, and brute force attacks, hackers are looking for any and every avenue into a network. SIEM Benefits. Types Of Threats.

Security Boulevard
JULY 9, 2024
Businesses need to know that pure prevention is in the past and, instead, automatically assume compromised security. Defense in depth and operational resiliency are the future for organizations that want to survive in the new world of cyber threats. Phishing attacks and DNS spoofing : Attackers using C2 communication rely on DNS.
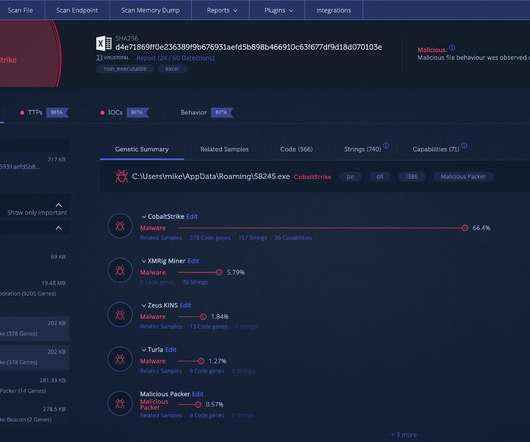
eSecurity Planet
MARCH 14, 2022
Pentesting involves vulnerability exploitation and post-exploitation actions – the idea is to conduct a real attack, like cybercriminals would do, except with an explicit authorization from the company in order to identify weaknesses and improve security defenses.

eSecurity Planet
MAY 2, 2024
Compromised Credentials Compromised identities from phishing, info stealers, keyloggers, and bad password habits provide the entry point for most ransomware attacks and data breaches. Sophos: Noted that 43% of all 2023 malware signature updates are for stealers, spyware, and keyloggers often used to steal credentials from devices.

eSecurity Planet
SEPTEMBER 13, 2024
Below, we explore the banking sector’s most common cyber security threats, highlighting real-world incidents and current trends. Phishing Attacks Phishing remains one of the most prevalent threats in the banking industry. Malware & Ransomware Malware, including ransomware, is another major threat to the banking sector.

eSecurity Planet
JUNE 7, 2022
As the demand for robust security defense grows by the day, the market for cybersecurity technology has exploded, as well as the number of available solutions. Application security, information security, network security, disaster recovery, operational security, etc. Improved Data Security.

eSecurity Planet
AUGUST 30, 2023
A new Cloudflare phishing report notes that most of the 1 billion brand impersonation emails the company detected “passed” SPF, DKIM, and DMARC email authentication protocols. At the same time, an organization is also quite likely to fall for business email compromise and phishing attacks from their vendors.

Security Boulevard
SEPTEMBER 20, 2021
The dissemination phase consists of active processing and dissemination of the processed data for the purpose of communicating the actionable intelligence for the purpose of ensuring that an organizations defense is actively aware of the threats facing its infrastructure and security defense mechanisms.

eSecurity Planet
SEPTEMBER 9, 2024
The following are some of the most significant threats ICS environments face today: Malware & Ransomware Malware and ransomware attacks specifically target ICS to disrupt industrial operations, encrypt critical data, or cause widespread damage to the system.

eSecurity Planet
NOVEMBER 13, 2023
Phishing When a threat actor sends an email with a malicious link and the target user clicks on that link, the compromised link can install malware onto the user’s machine or give the threat actor access to the user’s credentials, depending on the attack. Read our guide to securing your network next.

eSecurity Planet
NOVEMBER 10, 2023
After all, with most processes now touching the internet, a secure DNS solution can block threats beyond DNS processes and help secure email, endpoints, remote users, and more. Of these options, one of the most important is DNSSEC, which should be incorporated by organizations of all sizes.

Spinone
DECEMBER 17, 2019
It quietly makes its way past your security defenses into the heart of your data and keeps it hostage until you pay a ransom. Let’s take a phishing email that one of our colleagues got some time ago as an example to illustrate the most common signs: 1. Ransomware is a sly, silent, and vicious criminal.

eSecurity Planet
JUNE 10, 2024
June 5, 2024 DarkGate MaaS Switches to AutoHotkey for Stealthier Malware Delivery Type of vulnerability: Malware delivery mechanism. The problem: The DarkGate malware-as-a-service (MaaS) operation , notorious for its powerful remote access trojan (RAT) capabilities, has switched from using AutoIt scripts to AutoHotkey in version 6.

eSecurity Planet
AUGUST 9, 2024
Here are some tips for both users and network administrators to secure your network with a VPN. It does not scan for malware. It does not block phishing scams, hacking attempts, viruses, or malware. Kill Phishing This may be the easiest and hardest user behavior to control. A VPN can establish a perimeter.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content