Setting Up Your Network Security? Avoid These 4 Mistakes
Tech Republic Security
OCTOBER 4, 2024
Learn how to execute the fundamentals, harden your defenses, and protect your business's network security with no high-tech software.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
OCTOBER 4, 2024
Learn how to execute the fundamentals, harden your defenses, and protect your business's network security with no high-tech software.

Tech Republic Security
MARCH 14, 2024
To protect company data and reputation, it is essential to ensure that the network is secured from unauthorized access, data loss, malware infestations and security breaches. This can include internal and external systems, either company-owned or leased/rented/subscribed to. This must be done.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

eSecurity Planet
APRIL 26, 2024
Network security architecture is a strategy that provides formal processes to design robust and secure networks. Effective implementation improves data throughput, system reliability, and overall security for any organization.

The Last Watchdog
APRIL 21, 2021
From January through March 2021, TLS concealed 45 percent of the malware Sophos analysts observed circulating on the Internet; that’s double the rate – 23 percent – seen in early 2020, Dan Schiappa, Sophos’ chief product officer, told me in a briefing. And then they may use off-the-shelf malware to carry out their attack.

Tech Republic Security
MARCH 14, 2024
This Complete 2024 CompTIA Certification Bundle is both a way for tech entrepreneurs to secure their own systems and a gateway to a career in cybersecurity.

Krebs on Security
JUNE 8, 2023
It’s not often that a zero-day vulnerability causes a network security vendor to urge customers to physically remove and decommission an entire line of affected hardware — as opposed to just applying software updates. Campbell, Calif. “That’s not a ransomware actor, that’s a state actor.

Tech Republic Security
MARCH 13, 2023
A new malware dubbed HiatusRAT infects routers to spy on its targets, mostly in Europe and in the U.S. Learn which router models are primarily targeted and how to protect from this security threat. The post New Hiatus malware campaign targets routers appeared first on TechRepublic.

eSecurity Planet
OCTOBER 24, 2023
Malware attacks pose a significant risk to both individuals and businesses, infiltrating computer systems, compromising sensitive data and disrupting operations, leading to financial and data loss — and even extortion. Here are 15 important controls and best practices for preventing malware.

Tech Republic Security
NOVEMBER 14, 2022
TechRepublic readers can get this tiny mesh router that blocks security threats for only $79. The post Get instant malware filtering with Gryphon Guardian appeared first on TechRepublic.

Security Boulevard
JUNE 28, 2024
A threat group dubbed Unfurling Hemlock infects targeted campaign with a single compressed file that, once executed, launches a 'cluster bomb' of as many as 10 pieces of malware that include loaders, stealers, and backdoors. The post Unfurling Hemlock Tossing ‘Cluster Bombs’ of Malware appeared first on Security Boulevard.

eSecurity Planet
FEBRUARY 14, 2024
However, some host-based firewalls , gateways, and specialized equipment also incorporate stateful inspection for specific security use cases to hide high-value assets or block DDoS attacks. Network Security Stateful inspection improves general network and cloud security for all assets screened by the feature.

Security Boulevard
JUNE 28, 2024
The post Temu is Malware — It Sells Your Info, Accuses Ark. AG appeared first on Security Boulevard. Chinese fast-fashion-cum-junk retailer “is a data-theft business.”

Krebs on Security
OCTOBER 8, 2020
There’s an old adage in information security: “Every company gets penetration tested, whether or not they pay someone for the pleasure.” ” Many organizations that do hire professionals to test their network security posture unfortunately tend to focus on fixing vulnerabilities hackers could use to break in.

Security Boulevard
DECEMBER 8, 2023
Newly discovered cracked applications being distributed by unauthorized websites are delivering Trojan-Proxy malware to macOS users who are looking for free or cheap versions of the software tools they want. The malware can be used by bad actors for a range of malicious activities, including hacking into systems or running phishing campaigns.

Security Boulevard
JANUARY 24, 2025
A malicious generative AI chatbot dubbed "GhostGPT" is being advertised to cybercriminals on underground forums as a tool for more quickly and efficiently creating malware, running BEC attacks, and other nefarious activities, lowering the barrier for less-skilled hackers to launch attacks.

Security Boulevard
JANUARY 15, 2025
A Chinese-based threat group called Mustang Panda was using a variant of the PlugX malware to infected U.S. The post FBI Deletes PlugX Malware From Computers Infected by China Group appeared first on Security Boulevard. Windows computers and steal information.

Security Boulevard
FEBRUARY 13, 2024
Hackers are increasingly deploying “ultra-evasive, highly aggressive” malware with the ability to find and shut down enterprise security tools in compromised systems, allowing the bad actor to go undetected longer, according to researchers with Picus Security.

Security Boulevard
APRIL 10, 2024
Raspberry Robin, the highly adaptable and evasive worm and malware loader that first appeared on the cyberthreat scene in 2021, is now using a new method for spreading its malicious code. According to a report this week by threat researchers with HP Wolf Security, a new campaign detected last month indicated that the operators behind.

Security Boulevard
SEPTEMBER 6, 2024
Cisco Talos researchers found that multiple bad actors were abusing the MacroPack framework, continuing an ongoing trend of hackers repurposing legitimate security software tools to run cyber campaigns against organizations. The post Threat Actors Abuse Red Team Tool MacroPack to Deliver Malware appeared first on Security Boulevard.

Security Boulevard
MAY 30, 2024
Hackers with possible ties to the notorious North Korea-linked Lazarus Group are exploiting a recent critical vulnerability in Palo Alto Network’s PAN-OS software to run a sophisticated cryptomining operation that likely has nation-state backing.
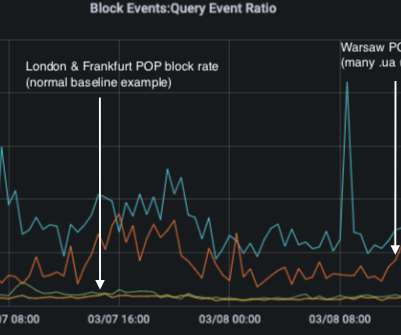
Krebs on Security
MARCH 11, 2022
As their cities suffered more intense bombardment by Russian military forces this week, Ukrainian Internet users came under renewed cyberattacks, with one Internet company providing service there saying they blocked ten times the normal number of phishing and malware attacks targeting Ukrainians. that are easier for computers to manage. .”

Tech Republic Security
DECEMBER 6, 2023
Based on the security researchers' analysis of the 2023 cyberthreat landscape, we highlight new or heightened risks.

Security Affairs
MARCH 13, 2025
To deploy malware, the threat actor had to first bypass this security mechanism. ” reads the report published by Mandiant“This specific technique is now tracked as CVE-2025-21590, as detailed in Juniper Networks security bulletin JSA93446.”

Security Boulevard
MARCH 24, 2025
A Cato Networks threat researcher with little coding experience was able to convince AI LLMs from DeepSeek, OpenAI, and Microsoft to bypass security guardrails and develop malware that could steal browser passwords from Google Chrome.

Security Boulevard
MARCH 17, 2025
A software programmer developed a way to use brute force to break the encryption of the notorious Akira ransomware using GPU compute power and enabling some victims of the Linux-focused variant of the malware to regain their encrypted data without having to pay a ransom.

The Hacker News
MARCH 5, 2025
USB drive attacks constitute a significant cybersecurity risk, taking advantage of the everyday use of USB devices to deliver malware and circumvent traditional network security measures. An example is the Stuxnet worm discovered in 2010, a malware designed to

The Last Watchdog
DECEMBER 13, 2020
The problem here is that a secured, cost-effective, and efficient networkmust be developed to support remote operations at scale. Many enterprises have accelerated their use of Virtual Private Network (VPN) solutions to support remote workers during this pandemic. The makeup of SASE . Ransomware.

Joseph Steinberg
APRIL 21, 2022
Likewise, employing techniques ranging from anomaly detection of certificates to utilizing artificial intelligence to detect irregular traffic patterns, suspicious file transfers, and/or attempts by malware to beacon, modern countermeasures can help ensure that zero trust initiatives do not undermine internal network security analysis processes.

The Last Watchdog
OCTOBER 25, 2021
Traditional network security solutions, such as firewalls, are not effective at detecting and stopping lateral attack movement – and that’s where the real damage is done. About the essayist: Ofer Israeli is Founder and CEO of Illusive , a supplier of advanced network security systems.

Security Affairs
FEBRUARY 27, 2025
At the end of May, the network security solutions provider Barracuda warned customers that some of its Email Security Gateway (ESG) appliances were recently breached by threat actors exploiting a now-patched zero-day vulnerability. The company confirmed that the CVE-2023-2868 was first exploited in October 2022.

Security Boulevard
MARCH 9, 2025
With a background in IT and a Master's degree in computer science, Masrani secured an internship and later a full-time position at AWS, focusing on data and network security. Hackers infiltrated home networks through TVs, stealing data and using devices to mine cryptocurrencies, leading to increased energy bills.

Tech Republic Security
APRIL 28, 2023
Europe and Ukraine are reportedly targets in this malware threat. Learn how to protect affected Cisco routers. The post Threat actor APT28 targets Cisco routers with an old vulnerability appeared first on TechRepublic.

SecureWorld News
FEBRUARY 10, 2025
The good news is that security teams can learn to anticipate these events and know exactly what to do to stop or prevent them. Why network security matters Before zooming in on specific attack methods, it's important to understand what network security is and why it's a top priority.

The Last Watchdog
JULY 25, 2022
Having spiked during the COVID-19 pandemic, threats such as malware, ransomware, and DDoS attacks continue to accelerate. A10’s security research team recorded a significant spike in the number of potential DDoS weapons available for exploitation in 2021 and early 2022. Related: Apple tools abuse widespread. Key findings follow.

SecureList
DECEMBER 9, 2024
Fortinet products are integral to many organizations’ network security. When critical vulnerabilities in such widely deployed products are exploited, it opens a pathway for attackers to breach the security of multiple organizations through a single vendor’s software or appliances.

The Last Watchdog
JUNE 22, 2022
During the first two decades of this century, virtual private networks —VPNs—served as a cornerstone of network security. VPNs encrypt data streams and protect endpoints from unauthorized access, essentially by requiring all network communications to flow over a secured pipe. Related: Deploying human sensors.

Security Boulevard
MARCH 10, 2025
A massive malvertising campaign that targeted individuals watching pirated videos on illegal streaming sites redirected them several times before landing them at GitHub repositories that hosted infostealers and other malware, according to Microsoft The post Microsoft: Massive Malvertising Campaign Infects a Million Devices appeared first on Security (..)

Security Affairs
DECEMBER 27, 2023
On December 21, the vendor also released security updates to fix the issue on already compromised ESG appliances where the threat actors installed SeaSpy and Saltwater malware. Barracuda, with the support of Mandiant, discovered the issue was exploited to deploy malware on a subset of appliances allowing for persistent backdoor access.

The Last Watchdog
MARCH 4, 2024
Nonprofits can bolster their network security by insisting on strong login credentials. Malware : Hackers deploy malicious software designed to cause significant disruptions and compromise data integrity. Investing in top-notch firewalls is also essential, as they serve as the first line of defense against external threats.

Schneier on Security
DECEMBER 9, 2020
FireEye’s Red Team tools are essentially built from malware that the company has seen used in a wide range of attacks. .’s tools were most likely more useful than FireEye’s since the U.S. government builds purpose-made digital weapons. Russia is presumed to be the attacker. Reuters article. Boing Boing post. Slashdot thread.

The Last Watchdog
NOVEMBER 8, 2021
With the benefits of the cloud comes the heavy responsibility of securing sensitive data. Not only is providing secure and reliable access of critical importance, it is a HIPAA requirement. The network security perimeter is dynamically created and policy-based, and must be guarded by secure and highly managed access controls.

Security Boulevard
JUNE 5, 2023
Malware Déjà Vu: Perhaps as many as 87 million victims—maybe more. The post Chrome Extensions Warning — Millions of Users Infected appeared first on Security Boulevard.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content