New Report on IoT Security
Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”

Schneier on Security
MAY 2, 2024
The UK is the first country to ban default passwords on IoT devices. On Monday, the United Kingdom became the first country in the world to ban default guessable usernames and passwords from these IoT devices. IoT manufacturers aren’t making two devices, one for California and one for the rest of the US.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Trend Micro
JULY 29, 2021
We summarize the characteristics, threats, and recommendations to improve the security posture of enterprises' and telecommunications companies' IT infrastructure.

CyberSecurity Insiders
NOVEMBER 25, 2021
A new legislation was introduced in the Britain’s parliament last week aiming to better protect IoT devices from sophisticated hackers. Now, comes the big question…what if companies indulging in the manufacturing of IoT cannot comply with the newly planned Britain’s digital law.? Well, it’s simple….the Hope it does!

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. Read more of the ACT
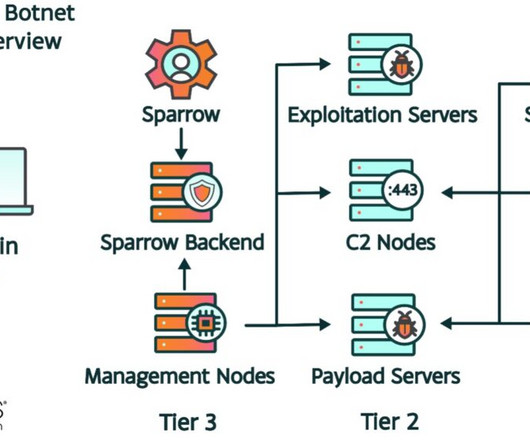
Security Affairs
SEPTEMBER 18, 2024
Researchers warn of a new IoT botnet called Raptor Train that already compromised over 200,000 devices worldwide. Cybersecurity researchers from Lumen’s Black Lotus Labs discovered a new botnet, named Raptor Train, composed of small office/home office (SOHO) and IoT devices. “This botnet has targeted entities in the U.S.

Security Boulevard
APRIL 30, 2024
The post Brits Ban Default Passwords — and More IoT Stupidity appeared first on Security Boulevard. The UK’s Product Security and Telecommunications Infrastructure Act aims to improve the security of net-connected consumer gear.

CSO Magazine
MAY 3, 2023
The ITU Telecommunication Standardization Sector (ITU-T) has approved a set of security specifications for internet of things (IoT) systems. The ITU-T is responsible for coordinating standards for telecommunications and information communication technology for cybersecurity.

Security Affairs
APRIL 30, 2024
The law, known as the Product Security and Telecommunications Infrastructure act (or PSTI act), will be effective on April 29, 2024. is the first country in the world to ban default credentia from IoT devices. . is the first country in the world to ban default credentia from IoT devices. ” The U.K. ” The U.K.

CyberSecurity Insiders
MARCH 18, 2021
It is known to offer services related to mobile data, broadband and voice and pretty soon will soon launch a business related to IoT in United Kingdom. The amount pronounced by AEPD against Vodafone is $9.72m is highest fine ever witnessed in a country against a multinational firm. The post Vodafone faces $9.7m

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. Read more of the ACT

eSecurity Planet
SEPTEMBER 1, 2021
Exposing the Internet of Things (IoT) Universe. Consumer electronics, business, network appliances, and industrial IoT (IIoT) devices are all driving the exponential growth of IoT systems. Consumer electronics, business, network appliances, and industrial IoT (IIoT) devices are all driving the exponential growth of IoT systems.

Bleeping Computer
MAY 10, 2024
Security flaws in Telit Cinterion cellular modems, widely used in sectors including industrial, healthcare, and telecommunications, could allow remote attackers to execute arbitrary code via SMS. [.]
Malwarebytes
NOVEMBER 25, 2021
To help address this cybersecurity and privacy problem, the UK government will soon roll out the Product Security and Telecommunications Infrastructure (PSTI) Bill that bans the use of default passwords for all internet-connected devices for the home, which we all call the Internet of Things (IoT).

Security Affairs
SEPTEMBER 26, 2024
Once compromised the networks of telecommunication companies, attackers can access to mobile phone users’ call data records. Based on the data available to us, Operation Soft Cell has been active since at least 2012, though some evidence suggests even earlier activity by the threat actor against telecommunications providers.

SecureWorld News
FEBRUARY 12, 2025
"Technology is an integral part of our lives that has become increasingly linked to critical infrastructure and the services we rely on daily like our hospitals, transit systems, energy suppliers, and telecommunications systems," said a press release from Public Safety Canada.

SecureWorld News
MARCH 24, 2022
Answer: The decision to pursue a career in cybersecurity came easy to me, as I was tenured as a technology and telecommunications professional for 15 years. As a military veteran of the United States Navy, I had a foundational background working in telecommunications. I enjoyed troubleshooting systems and solving problems.

Thales Cloud Protection & Licensing
SEPTEMBER 11, 2023
Thales 2023 Data Threat Report: The Increased Telco Cybersecurity Challenges in the 5G Era madhav Tue, 09/12/2023 - 05:15 Telecommunications firms have always faced a unique set of security challenges. Infrastructure extends to multiple cloud platforms and applications and the increased volume of connected IoT devices.

Thales Cloud Protection & Licensing
JANUARY 14, 2020
The adoption of emerging technologies like 5G will fuel the proliferation of Internet of Things (IoT) that’s often built with only a few security controls and therefore creating a larger attack surface that enterprises have to deal with., 5G tech will make the IoT a greater part of our everyday lives. Conclusion.

CyberSecurity Insiders
JUNE 22, 2021
Yet, there are some key concerns that telecommunication providers need to be aware of if they are going to successfully implement this next generation of connectivity, as well as inspire trust in customers. Securing millions of new IoT connections.

The Security Ledger
MARCH 13, 2019
Forget about Congress's latest attempt to regulate IoT security. The post Spotlight: CTIA’s IoT Cybersecurity Certification is a Big Deal. Forget about Congress’s latest attempt to regulate IoT security. to reign in insecure IoT endpoints. Setting a Bar on IoT Cyber Security. Here’s why.

The Security Ledger
JANUARY 19, 2022
Spotlight: Automation Beckons as DevOps, IoT Drive PKI Explosion Spotlight: COVID Broke Security. He has more than 30 years of business development and product management experience in software, security, and telecommunications to the company. Read the whole entry. » » Click the icon below to listen. Can We Fix It In 2022?

The Security Ledger
OCTOBER 8, 2020
To achieve their 5G transformation, telecommunications providers require security solutions and platforms built from the ground up for modern, dynamic business models. The post Opinion: Staying Secure Through 5G Migration appeared first on The Security Ledger.

CyberSecurity Insiders
OCTOBER 27, 2021
As for IoT devices, it is expected that more than 3 billion devices will be connected to cellular networks over the next five years and eSIM capable devices will exhibit CAGR of? It can also be deployed in consumer IoT and M2M devices, allowing connected devices to operate from anywhere. Simplifying connectivity .

The Security Ledger
MARCH 11, 2020
In this Spotlight* podcast, Sayed Wajahat Ali the Senior Director of Security Risk Management at DU TELECOM in the UAE joins us to talk about how digital transformation is shaking up the once-staid telecommunications industry and how his company is staying on top of both the risks and opportunities created by digital transformation.
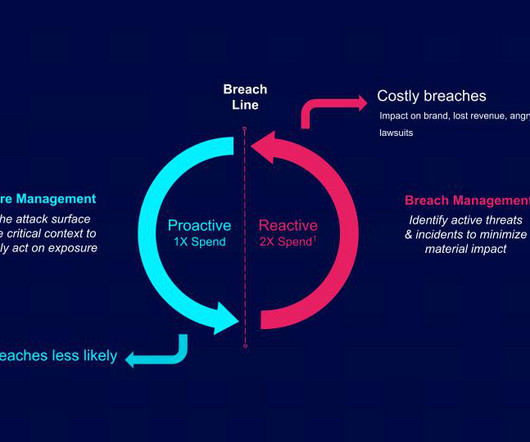
Security Boulevard
MARCH 17, 2025
Step 1: Know your attack surface Exposure management platforms discover and aggregate asset data across the entire external and internal attack surface, including cloud, IT, OT, IoT, identities and applications, providing a holistic view of the attack surface.

Malwarebytes
JUNE 19, 2023
There’s plenty of cheap Internet of Things (IoT) baby monitors out there with default passwords baked in, insecurely stored data, and an alarming amount of compromise stories in the news. Instead of Wi-Fi, they use other technologies called Digital Enhanced Cordless Telecommunications (DECT) and Frequency Hopping Spread Spectrum (FHSS).
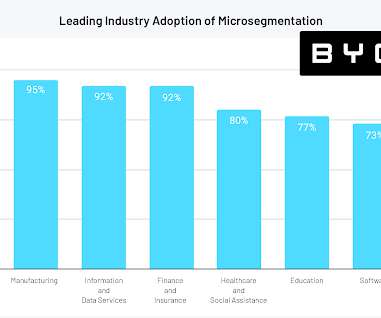
eSecurity Planet
NOVEMBER 10, 2021
The idea of walling off the most critical assets in a network is a particularly good fit for critical infrastructure and industrial IoT, in which a wide range of legacy devices simply aren’t able to run traditional EDR software. Critical Infrastructure, IIoT a Good Fit. “The companies are reliant on the perimeter.”

Google Security
FEBRUARY 23, 2023
After we participated in a recent White House Workshop on IoT security labeling , we shared more about our commitment to security and transparency by announcing the extension of device security assessments – which started with Pixel 3 and now includes Nest, and Fitbit hardware.

The Security Ledger
NOVEMBER 26, 2018
Telecommunications firms like to talk up all the great things that so-called 5G cellular networks will bring to smart phones. And, just as important, what are the security implications of massively distributed IoT endpoints connected to capacious 5G cellular infrastructure? Read the whole entry. »

Thales Cloud Protection & Licensing
DECEMBER 21, 2022
Subscriber authentication and privacy are among the most critical data in telecommunication networks. In 5G networks, HSMs act as trust anchors that protect the cryptographic infrastructure used to establish identities across the network.

SC Magazine
MAY 18, 2021
It changed what was considered normal within that network, introducing more users overall, more mobile devices popping up on the network, and new cloud applications and IoT devices. They replaced their telecommunications network and built a new software-defined wide area network to handle policy, security and networking functions.

Security Affairs
JANUARY 11, 2019
The British hacker Daniel Kaye (29) has been sentenced to 32 months in prison for the 2016 attack that took down telecommunications services in Liberia. The British hacker Daniel Kaye has been sentenced to 32 months in prison for the cyberattack on Liberian telecom firms.

Security Boulevard
SEPTEMBER 28, 2022
Optus, the second-largest telecommunications company in Australia, has experienced an API security incident – and it might come with a $1 million price tag. According to a recent report published by Acumen Research and Consulting, the global telecommunications API market will experience a CAGR of more than 20% from 2022 to 2030.

SC Magazine
MARCH 17, 2021
But supply chain controversies are nothing new to the telecommunications industry hardened by debates over Huawei. But supply chain issues have come to a head before in telecommunications and ICT with Huawei, for example. What was the genesis of the standards effort? I’ve spent 35 years in telecom. It’s all connected.

eSecurity Planet
AUGUST 22, 2023
Expanding attack surfaces require additional skills to secure, maintain, and monitor an ever-expanding environment of assets such as mobile, cloud, and the internet of things (IoT). assets (endpoints, servers, IoT, routers, etc.), and installed software (operating systems, applications, firmware, etc.). Outsourcing U.S.

IT Security Guru
DECEMBER 1, 2022
The fast rise in endpoint devices, the expansion of IoT, businesses’ desire to go digital , and the altering workforce models. Christos is intrigued by new challenges, open minded, and excited for exploring the impact of cybersecurity on industrial, critical infrastructure, telecommunications, financial, aviation, and maritime sectors.

CyberSecurity Insiders
NOVEMBER 22, 2021
NYSE: S) today announced that it is scheduled to present at the following virtual investor conferences: Barclays Global Technology, Media and Telecommunications Conference. .–( BUSINESS WIRE )–SentinelOne, Inc. Wednesday, December 8, 2021. 24th Annual Needham Growth Conference. Tuesday, January 11, 2022. About SentinelOne.

Thales Cloud Protection & Licensing
OCTOBER 10, 2022
In fact, according to Gartner, the deployment of IoT devices will accelerate from 25 billion in 2023 to 75 billion in 2025. Both the renewable energy business and the telecommunications industry are projected to expand significantly over the next decade, and the green energy movement is gaining traction. Clean energy.

Security Affairs
JULY 13, 2019
. “The password “gvt12345”, for example, suggests that hackers target users with routers from the former Brazilian internet service provider (ISP) GVT, which was acquired by Teleônica Brasil, and is the largest telecommunications company in the country.” ” states the analysis published by Avast.

CyberSecurity Insiders
OCTOBER 6, 2021
The list includes entrepreneurs, C-level executives, pioneers, and innovators who are working to streamline artificial intelligence, cybersecurity, machine learning, IoT, AR/VR, big data analytics, NLP, cloud computing, computer vision, intelligent automation, and many others.

CyberSecurity Insiders
NOVEMBER 26, 2021
Threat actors gained access to telecommunications providers, which then enabled them to access and monitor communications for customers of those providers. With the shift to work-from-home or hybrid work models, the rollout of 5G wireless, and the explosion of IoT (internet-of-things) devices, virtually everything is connected today.

SecureList
NOVEMBER 14, 2022
From a different angle, reporting from The Intercept revealed mobile surveillance capabilities available to Iran for the purposes of domestic investigations that leverage direct access to (and cooperation of) local telecommunication companies.

eSecurity Planet
DECEMBER 7, 2023
Yet, Internet of Things (IoT) devices tend to be designed with the minimum computing resources required to accomplish the designed task of the device (security camera, printer, TV, etc.). While less computationally constrained than IoT, mobile devices constrain computations to avoid consuming power and draining battery life.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content