Why Businesses Can’t Afford Anything Less Than Zero Trust in IoT
Security Boulevard
JUNE 23, 2022
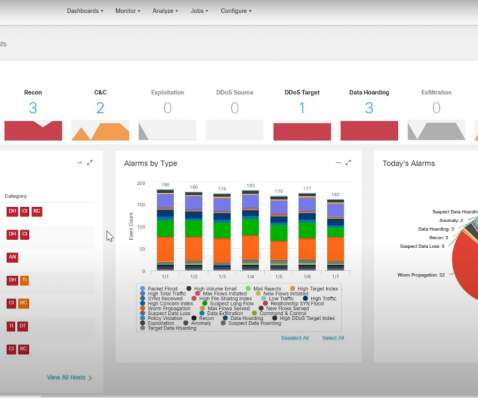
Why Businesses Can’t Afford Anything Less Than Zero Trust in IoT. The IoT Landscape and Threats. Considering the inherent insecurity of connected devices, the threats facing organizations today often involve weakly-defended IoT equipment as the first line of attack. brooke.crothers. Thu, 06/23/2022 - 16:26.










































Let's personalize your content