New Report on IoT Security
Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”

Trend Micro
JULY 29, 2021
We summarize the characteristics, threats, and recommendations to improve the security posture of enterprises' and telecommunications companies' IT infrastructure.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. What can be done?

eSecurity Planet
SEPTEMBER 1, 2021
Consumers and organizations are enthused about the operational benefits of more robust mobile connectivity, but the shift to 5G networks doesn’t come without risks. Here we’ll discuss the most significant risks posed by 5G, how U.S. Table of Contents What Are the Cybersecurity Risks of 5G? How is 5G Different?

Security Boulevard
APRIL 30, 2024
The post Brits Ban Default Passwords — and More IoT Stupidity appeared first on Security Boulevard. The UK’s Product Security and Telecommunications Infrastructure Act aims to improve the security of net-connected consumer gear.

eSecurity Planet
NOVEMBER 5, 2021
Enterprise risk management software can provide risk monitoring, identification, analysis, assessment, and mitigation, all in one solution. . While a number of solutions focus on the operational and financial risks posed to enterprises, this article focuses on software vendors specializing in cybersecurity risk management.

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. What can be done?

Security Boulevard
JUNE 2, 2023
The post 5G and Cybersecurity Risks in 2023 appeared first on Security Boulevard. Four years later, the number of people with 5G-enabled devices is still small in most countries. It’s uncertain if the reason behind the sluggish adoption is affordability, the lack of.
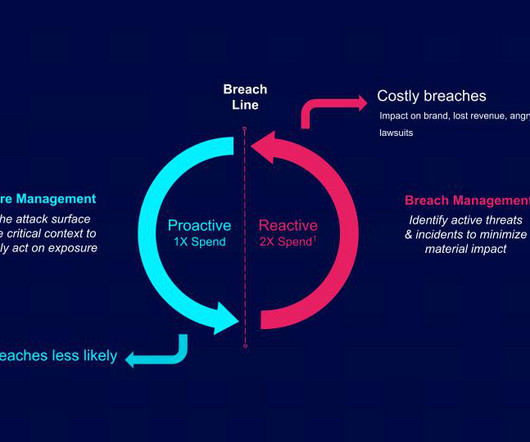
Security Boulevard
MARCH 17, 2025
In practice, even with reasonable service level agreements (SLAs), IT usually has to mitigate those risks. Just as alarming, the Tenable Cloud Risk Report 2024 shows that 74% of organizations have publicly exposed storage assets, including those containing sensitive data. As a result, security has become disjointed.

SecureWorld News
JANUARY 9, 2025
Richard Staynings , Chief Security Strategist for IoT security company Cylera and teaching professor for cybersecurity at the University of Denver, provides comments throughout. Also driving the growth in cyberattacks is the lack of cost or risk imposed on perpetrators of these crimes. Huawei and ZTE equipment ).

The Security Ledger
MARCH 11, 2020
In this Spotlight* podcast, Sayed Wajahat Ali the Senior Director of Security Risk Management at DU TELECOM in the UAE joins us to talk about how digital transformation is shaking up the once-staid telecommunications industry and how his company is staying on top of both the risks and opportunities created by digital transformation.

SecureWorld News
FEBRUARY 12, 2025
With cybercrime, state-sponsored attacks, and digital risks evolving rapidly, the strategy aims to modernize Canada's cyber defenses through enhanced collaboration, industry leadership, and proactive threat mitigation. Promote AI security guidelines to mitigate risks posed by generative AI and deepfake-driven cyber threats.

CyberSecurity Insiders
JUNE 22, 2021
Yet, there are some key concerns that telecommunication providers need to be aware of if they are going to successfully implement this next generation of connectivity, as well as inspire trust in customers. Below, we explore these risk factors in depth and determine what can be done to mitigate the threat moving forward.

IT Security Guru
DECEMBER 1, 2022
After all, cybersecurity is a matter of proper human risk management. Several reports, such as the World Economic Forum Global Risk Report 2022 and Verizon’s 2022 Data Breach Investigations Report highlight that human error is by far the biggest and dominant cause of illicit actions and cybersecurity issues. Reduce human risk.

Thales Cloud Protection & Licensing
SEPTEMBER 11, 2023
Thales 2023 Data Threat Report: The Increased Telco Cybersecurity Challenges in the 5G Era madhav Tue, 09/12/2023 - 05:15 Telecommunications firms have always faced a unique set of security challenges. Infrastructure extends to multiple cloud platforms and applications and the increased volume of connected IoT devices.

Malwarebytes
JUNE 19, 2023
There’s plenty of cheap Internet of Things (IoT) baby monitors out there with default passwords baked in, insecurely stored data, and an alarming amount of compromise stories in the news. Instead of Wi-Fi, they use other technologies called Digital Enhanced Cordless Telecommunications (DECT) and Frequency Hopping Spread Spectrum (FHSS).

The Security Ledger
NOVEMBER 26, 2018
Telecommunications firms like to talk up all the great things that so-called 5G cellular networks will bring to smart phones. And, just as important, what are the security implications of massively distributed IoT endpoints connected to capacious 5G cellular infrastructure? Read the whole entry. »

SecureWorld News
MARCH 24, 2022
Dr. Cooper works as a Senior Security Design Engineer and Risk Manager with T-Mobile Corporation and is an adjunct professor teaching course curriculum under cybersecurity degree programs with the University of Wisconsin and University of New York. In this installment, we introduce you to Dr. Cheryl Cooper.
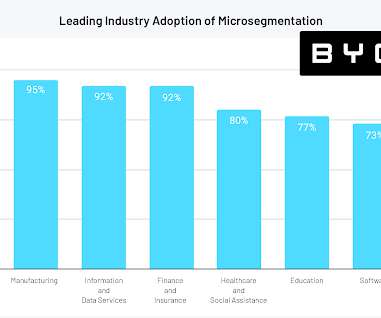
eSecurity Planet
NOVEMBER 10, 2021
The idea of walling off the most critical assets in a network is a particularly good fit for critical infrastructure and industrial IoT, in which a wide range of legacy devices simply aren’t able to run traditional EDR software. So I assume that it’s perceived as an operational or business risk to them.”

Thales Cloud Protection & Licensing
JANUARY 14, 2020
The adoption of emerging technologies like 5G will fuel the proliferation of Internet of Things (IoT) that’s often built with only a few security controls and therefore creating a larger attack surface that enterprises have to deal with., 5G tech will make the IoT a greater part of our everyday lives. Conclusion.

SC Magazine
MARCH 17, 2021
The world recently came face-to-face with supply chain risk when nation-state hackers breached government and business alike through SolarWinds servers and other attack vectors. But supply chain controversies are nothing new to the telecommunications industry hardened by debates over Huawei. So the risk has gone up exponentially.

CyberSecurity Insiders
NOVEMBER 26, 2021
Looking ahead to what Cybereason and our customers need to be aware of for 2022, it’s important to keep those things in mind, but let us consider the broader threat landscape—and what we are seeing in terms of emerging attacks and current threat research—to identify key risks that defenders need to prepare for. 2022 Cybersecurity Predictions.

eSecurity Planet
OCTOBER 26, 2021
SBOMs also offer protection against licensing and compliance risks associated with SLAs with a granular inventory of software components. With a universe of open source and proprietary components, SBOMs provide transparency by identifying risk-prone elements or later deemed vulnerable to attack. SBOM Use Cases.

SC Magazine
MAY 18, 2021
While zero trust may be ill defined for some in the research community, the concept is helping to translate previously abstract or technical concepts about risk to a new audience, and spurring systemic transformation of security operations across companies in a way that other frameworks or guidance have failed to do.

Security Boulevard
SEPTEMBER 28, 2022
Optus, the second-largest telecommunications company in Australia, has experienced an API security incident – and it might come with a $1 million price tag. Growing API Usage in Telco Sector Increases Security Risks. APIs now exist in every IoT device, from security cameras to video doorbells. That’s a huge risk!

eSecurity Planet
DECEMBER 7, 2023
Yet, Internet of Things (IoT) devices tend to be designed with the minimum computing resources required to accomplish the designed task of the device (security camera, printer, TV, etc.). While less computationally constrained than IoT, mobile devices constrain computations to avoid consuming power and draining battery life.

Thales Cloud Protection & Licensing
NOVEMBER 14, 2019
Many of the new legal frameworks and regulations bring unknown future risks. Technological developments, like the adoption of cloud computing and the proliferation of the Internet of Things (IoT), are disrupting traditional business models and bring new challenges to areas such as law, communication and business development practices.

Thales Cloud Protection & Licensing
JULY 21, 2022
The threat of attacks against Critical National Infrastructure (CNI) – energy, utilities, telecommunications, and transportation – is now front of mind for many. Reducing the risk of attacks such as ransomware and malware on CNI will be of paramount importance to the stability of nation states for years to come.

eSecurity Planet
AUGUST 22, 2023
Expanding attack surfaces require additional skills to secure, maintain, and monitor an ever-expanding environment of assets such as mobile, cloud, and the internet of things (IoT). assets (endpoints, servers, IoT, routers, etc.), and installed software (operating systems, applications, firmware, etc.). Outsourcing U.S.

Thales Cloud Protection & Licensing
OCTOBER 10, 2022
In fact, according to Gartner, the deployment of IoT devices will accelerate from 25 billion in 2023 to 75 billion in 2025. Both the renewable energy business and the telecommunications industry are projected to expand significantly over the next decade, and the green energy movement is gaining traction. Clean energy.

SC Magazine
MAY 1, 2021
Cedric Leighton is founder and president of Cedric Leighton Associates, a strategic risk and leadership management consultancy. Since founding Cedric Leighton Associates, he has become an internationally known strategic risk expert. Leighton is also a founding partner of CYFORIX, specializing in the field of cyber risk.

eSecurity Planet
JANUARY 28, 2021
As attack methodologies evolve due to AI, machine learning and nation-state hackers , security startups are receiving a lot of funding to develop products that can secure application access for remote workers , provide real-time visibility into cyber attacks and protect data as it travels from the cloud to IoT devices.
eSecurity Planet
MARCH 7, 2023
Limited tests can focus on narrower targets such as networks, Internet of Things (IoT) devices, physical security, cloud security, web applications, or other system components. Pros and Cons of Penetration Testing Like all security solutions and approaches, penetration tests have benefits, risks, and challenges.

Security Boulevard
APRIL 5, 2024
Fast enough for government work: The Federal Communications Commission is finally minded to do something about decades-old vulnerabilities. The post FCC: Phone Network Bugs Must Be Fixed — But are SS7/Diameter Beyond Repair? appeared first on Security Boulevard.

eSecurity Planet
JUNE 10, 2024
The fix: To prevent the risk, federal agencies and companies that use Oracle WebLogic Server should apply the most recent fixes before June 24, 2024. The problem: The Muhstik botnet exploited a severe RCE issue in Apache RocketMQ ( CVE-2023-33246 ) to attack Linux systems and IoT devices for DDoS and cryptomining.

eSecurity Planet
APRIL 26, 2022
Company Sector Year Status Vicarius Vulnerability management 2022 Private Dragos ICS and OT security 2021 Private Safeguard Cyber Risk management 2021 Private CyberGRX Risk management 2019 Private Signifyd Fraud protection 2018 Private RedOwl Security analytics 2015 Acquired: Forcepoint. AllegisCyber Investments. BVP Investments.

Pen Test
OCTOBER 12, 2023
In contemporary times, with the exponential growth of the Internet of Things (IoT), smart homes, connected cars, and wearable devices, the importance of RF pentesting has soared significantly. It has significantly impacted various industries, from telecommunications and healthcare to transportation and entertainment.
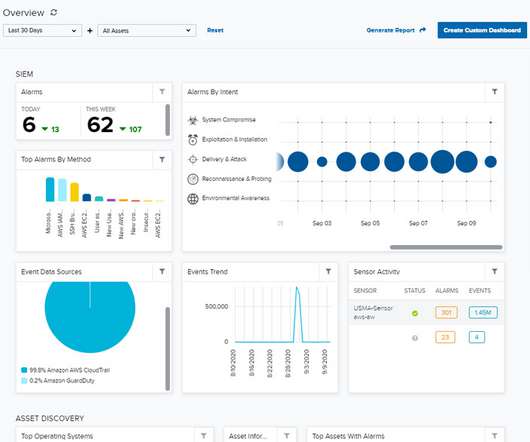
eSecurity Planet
FEBRUARY 9, 2022
According to Jay McBain, an analyst at Forrester Research, spending on IT and telecommunications will be worth about $7 trillion by 2030. EDR is a centralized management tool for endpoints (laptops, mobile devices, servers and even IoT devices for some products), used to manage and respond to threats on an organization’s devices.

Security Boulevard
JUNE 26, 2023
In this article, we will dive deep into different types of data breaches , how organizations can mitigate their risk of falling victim to a breach, and what industries face the highest risk of falling victim to a cyber security attack. Every organization is, to varying degrees, potentially at risk of experiencing a data breach.

eSecurity Planet
JANUARY 26, 2022
With Reveal(x) Advisor, organizations can have an on-demand analyst help with deployment, application mapping, and SOC or risk optimization. Spun off from the telecommunications vendor JDS Uniphase in 2015, Viavi Solutions is a newer name, but it has four-plus decades of IT services experience. Datadog Features. VIAVI Solutions.

eSecurity Planet
MAY 27, 2021
The Tel Aviv-based vendor focuses on cyber risk analytics and cloud security software to give network administrators more robust visibility into threats. With integrated threat intelligence and risk assessments, protecting your infrastructure is that much easier. Breach and attack simulation (BAS): XM Cyber. XM Cyber Platform.

Centraleyes
SEPTEMBER 23, 2024
The law applies to businesses across all industries that engage in commercial activities, including retail, banking, telecommunications, and online services. Breach Notification : Organizations must notify individuals and the Privacy Commissioner of any data breach that poses a real risk of significant harm.

eSecurity Planet
AUGUST 9, 2023
Quality MSPs easily deliver the additional IT capability for surges and, more importantly, can easily accommodate decreases in demand without the risk of layoffs or losing experienced employees. An MSP knows that if they betray their customer’s trust, they risk having their reputation actively attacked by the burned customer.

eSecurity Planet
AUGUST 9, 2023
Quality MSPs easily deliver the additional IT capability for surges and, more importantly, can easily accommodate decreases in demand without the risk of layoffs or losing experienced employees. An MSP knows that if they betray their customer’s trust, they risk having their reputation actively attacked by the burned customer.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content