New Report on IoT Security
Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”

Schneier on Security
MAY 2, 2024
The UK is the first country to ban default passwords on IoT devices. On Monday, the United Kingdom became the first country in the world to ban default guessable usernames and passwords from these IoT devices. IoT manufacturers aren’t making two devices, one for California and one for the rest of the US.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CyberSecurity Insiders
NOVEMBER 25, 2021
A new legislation was introduced in the Britain’s parliament last week aiming to better protect IoT devices from sophisticated hackers. Now, comes the big question…what if companies indulging in the manufacturing of IoT cannot comply with the newly planned Britain’s digital law.? Well, it’s simple….the Hope it does!

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. Read more of the ACT

Security Boulevard
APRIL 30, 2024
The post Brits Ban Default Passwords — and More IoT Stupidity appeared first on Security Boulevard. The UK’s Product Security and Telecommunications Infrastructure Act aims to improve the security of net-connected consumer gear.
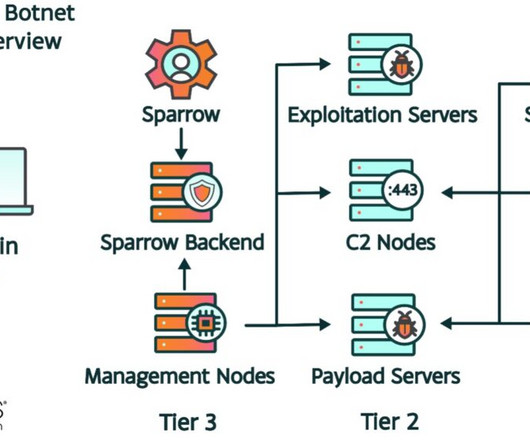
Security Affairs
SEPTEMBER 18, 2024
Researchers warn of a new IoT botnet called Raptor Train that already compromised over 200,000 devices worldwide. Cybersecurity researchers from Lumen’s Black Lotus Labs discovered a new botnet, named Raptor Train, composed of small office/home office (SOHO) and IoT devices. “This botnet has targeted entities in the U.S.

CSO Magazine
MAY 3, 2023
The ITU Telecommunication Standardization Sector (ITU-T) has approved a set of security specifications for internet of things (IoT) systems. The ITU-T is responsible for coordinating standards for telecommunications and information communication technology for cybersecurity.

Security Affairs
SEPTEMBER 26, 2024
internet service providers (ISPs) as part of a cyber espionage campaign code-named Salt Typhoon. internet service providers in recent months as part of a cyber espionage campaign code-named Salt Typhoon. internet-service providers in recent months in pursuit of sensitive information, according to people familiar with the matter.”

Security Affairs
APRIL 30, 2024
The law, known as the Product Security and Telecommunications Infrastructure act (or PSTI act), will be effective on April 29, 2024. is the first country in the world to ban default credentia from IoT devices. . is the first country in the world to ban default credentia from IoT devices. ” The U.K. ” The U.K.
Malwarebytes
NOVEMBER 25, 2021
The idea of connecting your entire home to the internet was once a mind-blowing concept. This law covers smartphones, routers, games consoles, toys, speakers, security cameras, internet-enabled white goods (fridge, washing machine, etc.) Thanks to smart devices, that concept is now a reality.

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. Read more of the ACT

eSecurity Planet
SEPTEMBER 1, 2021
Exposing the Internet of Things (IoT) Universe. Consumer electronics, business, network appliances, and industrial IoT (IIoT) devices are all driving the exponential growth of IoT systems. IoT products are notoriously vulnerable appliances because the build prioritizes ease of use and connectivity. Supply Chains.

The Security Ledger
NOVEMBER 26, 2018
Telecommunications firms like to talk up all the great things that so-called 5G cellular networks will bring to smart phones. But what new kinds of Internet of Things use cases may become possible? Telecommunications firms like to talk up all the great things that so-called 5G cellular networks will bring to smart phones.

Malwarebytes
JUNE 19, 2023
As it happens, you don’t have to buy an internet connected device for one of the most private areas of your home. There’s plenty of cheap Internet of Things (IoT) baby monitors out there with default passwords baked in, insecurely stored data, and an alarming amount of compromise stories in the news.

SecureWorld News
MARCH 24, 2022
Answer: The decision to pursue a career in cybersecurity came easy to me, as I was tenured as a technology and telecommunications professional for 15 years. As a military veteran of the United States Navy, I had a foundational background working in telecommunications. I enjoyed troubleshooting systems and solving problems.

Security Affairs
JANUARY 11, 2019
The British hacker Daniel Kaye (29) has been sentenced to 32 months in prison for the 2016 attack that took down telecommunications services in Liberia. An employee of the rival firm Cellcom paid Kaye to carry out a DDoS attack on the Liberian phone and internet provider Lonestar. ” reported the BBC. . ” reported the BBC.

The Security Ledger
MARCH 13, 2019
Forget about Congress's latest attempt to regulate IoT security. The post Spotlight: CTIA’s IoT Cybersecurity Certification is a Big Deal. Forget about Congress’s latest attempt to regulate IoT security. to reign in insecure IoT endpoints. CTIAs new certification is the toothiest standard going.

Thales Cloud Protection & Licensing
JANUARY 14, 2020
The adoption of emerging technologies like 5G will fuel the proliferation of Internet of Things (IoT) that’s often built with only a few security controls and therefore creating a larger attack surface that enterprises have to deal with., 5G tech will make the IoT a greater part of our everyday lives. Conclusion.

The Security Ledger
MARCH 11, 2020
In this Spotlight* podcast, Sayed Wajahat Ali the Senior Director of Security Risk Management at DU TELECOM in the UAE joins us to talk about how digital transformation is shaking up the once-staid telecommunications industry and how his company is staying on top of both the risks and opportunities created by digital transformation.

The Security Ledger
OCTOBER 8, 2020
To achieve their 5G transformation, telecommunications providers require security solutions and platforms built from the ground up for modern, dynamic business models. The post Opinion: Staying Secure Through 5G Migration appeared first on The Security Ledger.

SC Magazine
MAY 18, 2021
It changed what was considered normal within that network, introducing more users overall, more mobile devices popping up on the network, and new cloud applications and IoT devices. They replaced their telecommunications network and built a new software-defined wide area network to handle policy, security and networking functions.

Security Affairs
JULY 13, 2019
“The password “gvt12345”, for example, suggests that hackers target users with routers from the former Brazilian internet service provider (ISP) GVT, which was acquired by Teleônica Brasil, and is the largest telecommunications company in the country.” ” states the analysis published by Avast.

eSecurity Planet
AUGUST 22, 2023
Expanding attack surfaces require additional skills to secure, maintain, and monitor an ever-expanding environment of assets such as mobile, cloud, and the internet of things (IoT). assets (endpoints, servers, IoT, routers, etc.), and installed software (operating systems, applications, firmware, etc.). Outsourcing U.S.

SC Magazine
MARCH 17, 2021
But supply chain controversies are nothing new to the telecommunications industry hardened by debates over Huawei. But supply chain issues have come to a head before in telecommunications and ICT with Huawei, for example. What was the genesis of the standards effort? I’ve spent 35 years in telecom. It’s all connected.

Security Boulevard
SEPTEMBER 28, 2022
Optus, the second-largest telecommunications company in Australia, has experienced an API security incident – and it might come with a $1 million price tag. According to a recent report published by Acumen Research and Consulting, the global telecommunications API market will experience a CAGR of more than 20% from 2022 to 2030.

CyberSecurity Insiders
NOVEMBER 26, 2021
Threat actors gained access to telecommunications providers, which then enabled them to access and monitor communications for customers of those providers. With the shift to work-from-home or hybrid work models, the rollout of 5G wireless, and the explosion of IoT (internet-of-things) devices, virtually everything is connected today.

Thales Cloud Protection & Licensing
OCTOBER 10, 2022
In fact, according to Gartner, the deployment of IoT devices will accelerate from 25 billion in 2023 to 75 billion in 2025. Both the renewable energy business and the telecommunications industry are projected to expand significantly over the next decade, and the green energy movement is gaining traction. Clean energy.

Thales Cloud Protection & Licensing
NOVEMBER 14, 2019
Technological developments, like the adoption of cloud computing and the proliferation of the Internet of Things (IoT), are disrupting traditional business models and bring new challenges to areas such as law, communication and business development practices. Australia requires health data to be stored locally).

eSecurity Planet
DECEMBER 7, 2023
ECC is used for email encryption, cryptocurrency digital signatures, and internet communication protocols. Encryption Tools and IT Security Fundamental protocols incorporate encryption to automatically protect data and include internet protocol security (IPSec), Kerberos, Secure Shell (SSH), and the transmission control protocol (TCP).

Thales Cloud Protection & Licensing
JULY 21, 2022
The threat of attacks against Critical National Infrastructure (CNI) – energy, utilities, telecommunications, and transportation – is now front of mind for many. From the ransomware attack that compromised a major U.S. gas pipeline in 2021 to the rise of nation-state attacks, critical infrastructure organizations are under siege.

SecureList
NOVEMBER 14, 2022
From a different angle, reporting from The Intercept revealed mobile surveillance capabilities available to Iran for the purposes of domestic investigations that leverage direct access to (and cooperation of) local telecommunication companies. In the past years, we have seen vulnerability researchers increasingly focus on emailing software.

SecureList
FEBRUARY 16, 2021
In October, telecommunications firm Telenor Norway was another to fall victim. In 2020, when much of life shifted online, internet resources repeatedly suffered from surges in totally legitimate activity. Extortionists’ activity regularly made the news throughout 2020.

Pen Test
OCTOBER 12, 2023
In contemporary times, with the exponential growth of the Internet of Things (IoT), smart homes, connected cars, and wearable devices, the importance of RF pentesting has soared significantly. GHz and 5 GHz bands, providing high-speed wireless internet connectivity (Kurkovsky, 2006). IoT Security Techniques and Implementation.
eSecurity Planet
MARCH 7, 2023
Limited tests can focus on narrower targets such as networks, Internet of Things (IoT) devices, physical security, cloud security, web applications, or other system components. Known as black , white , and gray box pentests, these differ in how much information is provided to the pentester before running the simulated attacks.

SC Magazine
MAY 1, 2021
He was previously senior manager at Deloitte, focused on IoT and industrial cybersecurity. He was also director of the SANS Internet Storm Center. John Johnson is cybersecurity leader for a large consumer manufacturing company. Krishna Vedula is chief operating officer at 365 Retail Markets.
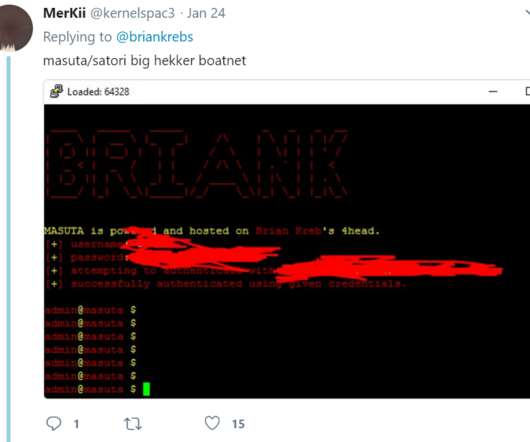
Krebs on Security
JUNE 25, 2020
Justice Department today criminally charged a Canadian and a Northern Ireland man for allegedly conspiring to build botnets that enslaved hundreds of thousands of routers and other Internet of Things (IoT) devices for use in large-scale distributed denial-of-service (DDoS) attacks. telecommunications provider TalkTalk.

eSecurity Planet
APRIL 26, 2022
Company Sector Year Status Abnormal Security Cloud email security 2019 Private Sqreen Application security 2019 Acquired: Datadog Demisto SOAR 2018 Acquired by PAN Skyhigh Cloud security 2012 Acquired: McAfee OpenDNS Internet security 2009 Acquired: Cisco Palo Alto Networks Cloud and network security 2006 NYSE: PANW. Insight Partners.

Security Boulevard
JUNE 26, 2023
However, there are some high-target industries, including healthcare, financial services, technology and telecommunications, retail and e-commerce, and the government and public sector, which are at a heightened risk of being targeted by cyber criminals. Supply chain security and third-party vulnerabilities.

Centraleyes
SEPTEMBER 23, 2024
The law applies to businesses across all industries that engage in commercial activities, including retail, banking, telecommunications, and online services. PIPEDA and Emerging Technologies As technologies like artificial intelligence (AI), big data, and the Internet of Things (IoT) continue to grow, so do privacy concerns.

eSecurity Planet
MAY 27, 2021
Larger organizations most targeted by advanced persistent threats (APTs) like enterprises and government agencies, financial services, energy, and telecommunications make up Kaspersky EDR’s clientele. Web application firewalls (WAF) offer monitoring, filtering, and blocking of internet communications.

eSecurity Planet
AUGUST 9, 2023
Backup and disaster recovery services Cloud services Data analytics Data center hosting Email services Endpoint and server management Hardware repair Help desk Infrastructure-as-a-Service (IaaS) IT architecture design IT policy and program development IT system auditing and gap assessments IT system implementations and integrations Managed detection (..)

eSecurity Planet
AUGUST 9, 2023
Backup and disaster recovery services Cloud services Data analytics Data center hosting Email services Endpoint and server management Hardware repair Help desk Infrastructure-as-a-Service (IaaS) IT architecture design IT policy and program development IT system auditing and gap assessments IT system implementations and integrations Managed detection (..)

Thales Cloud Protection & Licensing
OCTOBER 23, 2023
The threat of attacks against Critical National Infrastructure (CNI) – energy, utilities, telecommunications, and transportation – is a top priority. Data Breach Cloud Security Internet Of Things Access Control Chris Harris | EMEA Technical Director More About This Author > Schema

eSecurity Planet
JANUARY 28, 2021
As attack methodologies evolve due to AI, machine learning and nation-state hackers , security startups are receiving a lot of funding to develop products that can secure application access for remote workers , provide real-time visibility into cyber attacks and protect data as it travels from the cloud to IoT devices. SpiderSilk.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content