DDoS Mitigation Firm Founder Admits to DDoS
Krebs on Security
JANUARY 20, 2020
DDoS attacks involve flooding a target Web site with so much junk Internet traffic that it can no longer accommodate legitimate visitors.

Krebs on Security
JANUARY 20, 2020
DDoS attacks involve flooding a target Web site with so much junk Internet traffic that it can no longer accommodate legitimate visitors.

Schneier on Security
DECEMBER 19, 2019
Arbitrary code execution: unauthenticated root shell access through Android Debug Bridge (ADB) leads to arbitrary code execution and system administration (CVE-2019-16273). These are stupid design decisions made by engineers who had no idea how to create a secure system.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
JUNE 15, 2022
Today, the Internet Explorer (IE) 11 desktop application goes out of support and will be retired for certain versions of Windows 10. Microsoft’s Internet Explorer 1.0 With Windows 10, Edge became the default Microsoft browser, but Internet Explorer could still be found in the Windows Accessories folder. Not so much.

Security Affairs
SEPTEMBER 2, 2019
Akamai researcher Larry Cashdollar reported that a cryptocurrency miner that previously hit only Arm-powered IoT devices it now targeting Intel systems. The researchers revealed that one of his honeypots was hit by this IoT malware that targets Intel machines running Linux. “This one seems to target enterprise systems.”

SecureList
DECEMBER 9, 2024
was used by tens of millions of websites approximately 4% of all sites on the internet which highlights the severity of the incident, whose full impact is yet to be determined. It is a critical tool in various fields, including system administration, development, and cybersecurity. Why does it matter?

The Last Watchdog
JUNE 2, 2021
PKI is the authentication and encryption framework on which the Internet is built. It works by issuing digital certificates to verify the authenticity of the servers ingesting the data trickling in from our smartphones, Internet of Things sensors and the like. Encrypting just once. I’ll keep watch, and keep reporting.
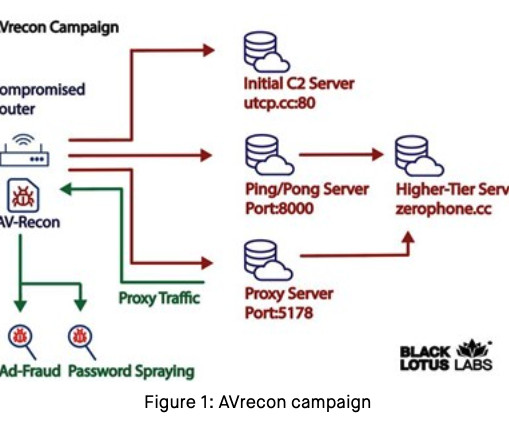
Krebs on Security
JULY 25, 2023
Researchers this month uncovered a two-year-old Linux-based remote access trojan dubbed AVrecon that enslaves Internet routers into botnet that bilks online advertisers and performs password-spraying attacks. md , and that they were a systems administrator for sscompany[.]net. SocksEscort[.]com
Let's personalize your content