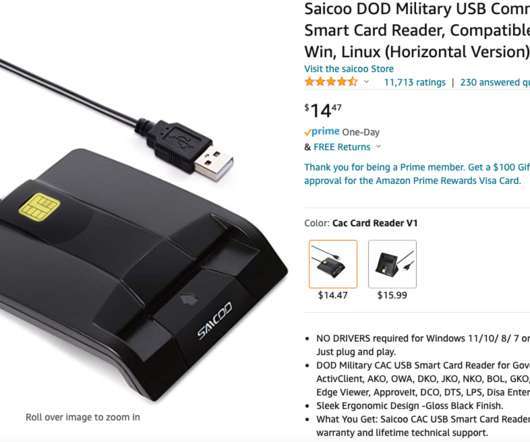
When Your Smart ID Card Reader Comes With Malware
Krebs on Security
MAY 17, 2022
“From the details you offered, issue may probably caused by your computer security defense system as it seems not recognized our rarely used driver & detected it as malicious or a virus,” Saicoo’s support team wrote in an email. “When driver installed, this message will vanish out of sight.

















































Let's personalize your content