Just Culture and Information Security
Adam Shostack
JANUARY 2, 2025
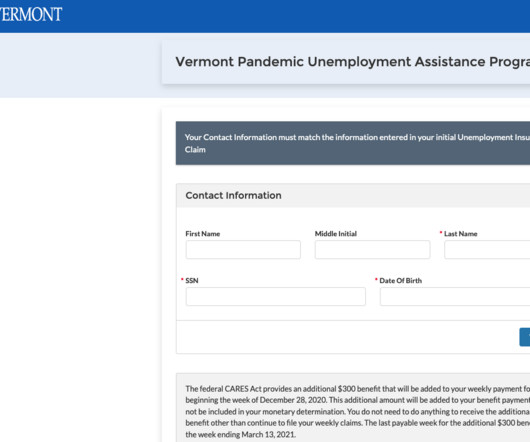
[no description provided] Yesterday Twitter revealed they had accidentally stored plain-text passwords in some log files. There was no indication the data was accessed and users were warned to update their passwords. There was no known breach, but Twitter went public anyway, and was excoriated in the press and on Twitter.













Let's personalize your content