Feds Charge Five Men in ‘Scattered Spider’ Roundup
Krebs on Security
NOVEMBER 21, 2024
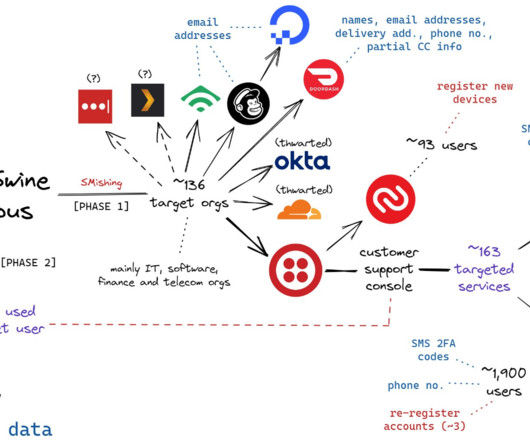
The targeted SMS scams asked employees to click a link and log in at a website that mimicked their employer’s Okta authentication page. Evans, Elbadawy, Osiebo and Urban were all charged with one count of conspiracy to commit wire fraud, one count of conspiracy, and one count of aggravated identity theft.


















































Let's personalize your content