Understanding Have I Been Pwned's Use of SHA-1 and k-Anonymity
Troy Hunt
JUNE 30, 2022
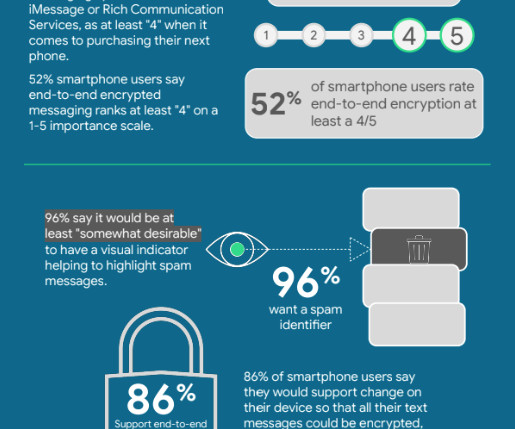
Four and a half years ago now, I rolled out version 2 of HIBP's Pwned Passwords that implemented a really cool k-anonymity model courtesy of the brains at Cloudflare. Actually, the multiple problems, the first of which is that it's just way too fast for storing user passwords in an online system.
























Let's personalize your content