Does AI Enhance Virtual Reality Experiences?
SecureWorld News
OCTOBER 13, 2024
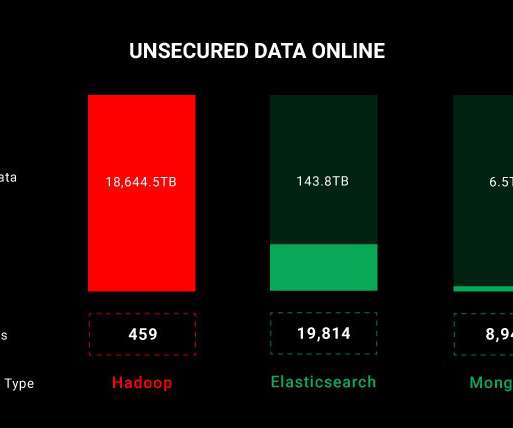
Malicious actors can unveil stored system data, potentially utilizing it for identity theft, false profiling, data harvesting , fraudulent activity, and many other activities that violate a person's privacy. However, unauthorized access to this data is entirely possible without proper encryption and data protection measures.


















Let's personalize your content