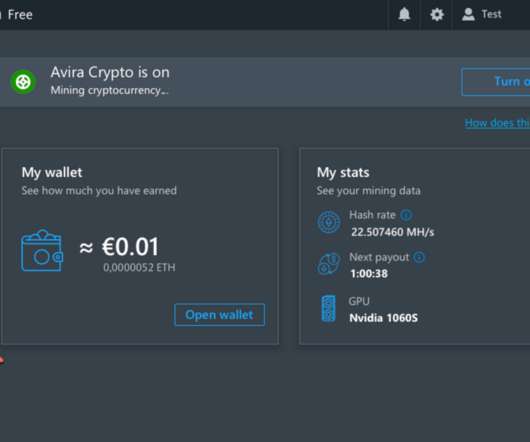
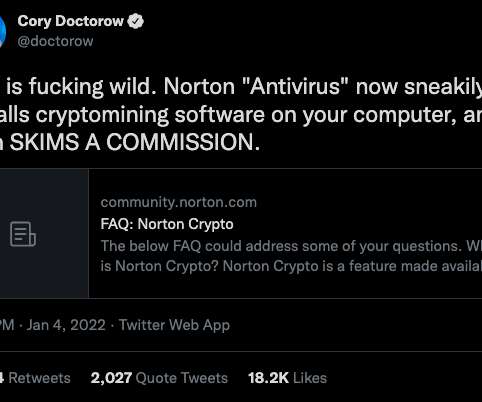
500M Avira Antivirus Users Introduced to Cryptomining
Krebs on Security
JANUARY 8, 2022
KG is a German multinational software company best known for their Avira Free Security (a.k.a. In 2017, the identity theft protection company LifeLock was acquired by Symantec Corp. Avira Free Antivirus). In January 2021, Avira was acquired by Tempe, Ariz.-based based NortonLifeLock Inc.,












Let's personalize your content