Weekly Update 219: IoT Unravelled with Scott Helme
Troy Hunt
NOVEMBER 28, 2020
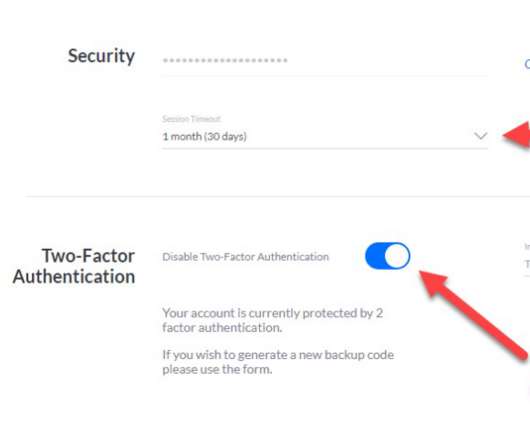
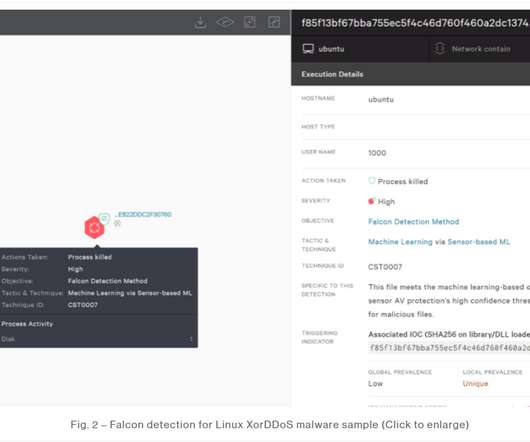
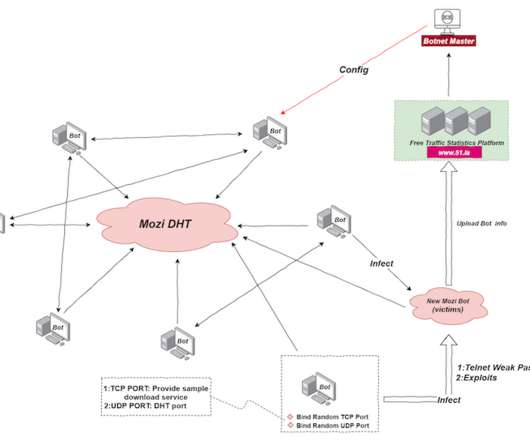
More than 200,000 unique visitors dropped by this week, mostly to read about IoT things. I topped the week off by spending a couple of hours talking to Scott Helme about our respective IoT experiences so that's the entirety of this week's update - Scott and I talking IoT.






































Let's personalize your content