White hat hackers gained access more than 150,000 surveillance cameras
Security Affairs
MARCH 10, 2021
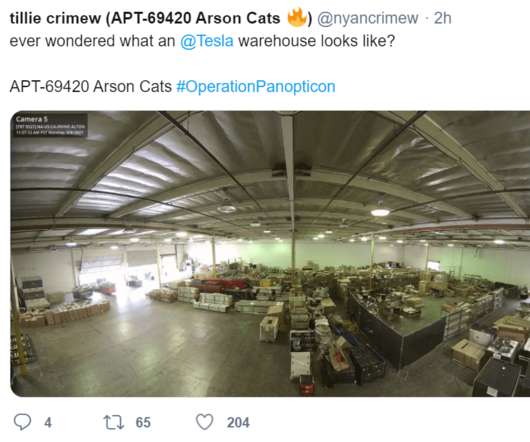
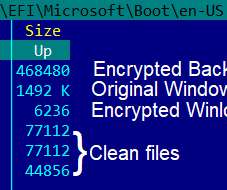
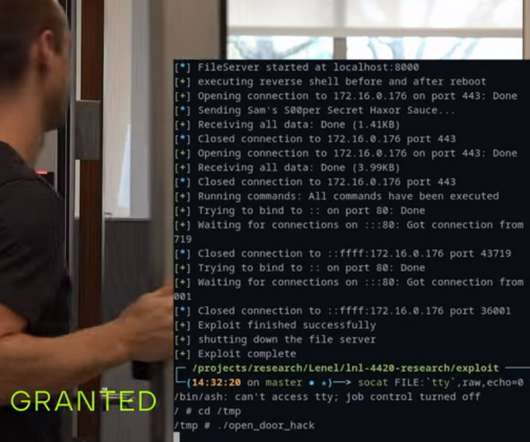
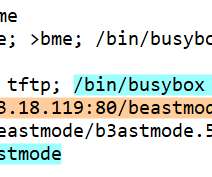
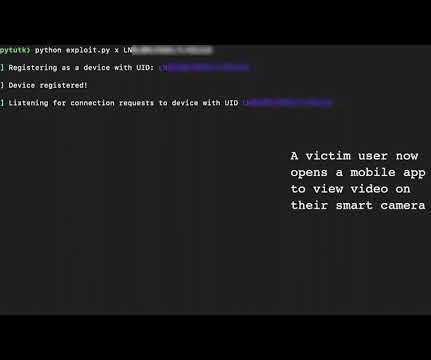
A group of hackers claimed to have compromised more than 150,000 surveillance cameras at banks, jails, schools, and prominent companies like Tesla and Equinox. A group of US hackers claimed to have gained access to footage from 150,000 security cameras at banks, jails, schools, healthcare clinics, and prominent organizations.






















Let's personalize your content