PTZOptics cameras zero-days actively exploited in the wild
Security Affairs
NOVEMBER 2, 2024
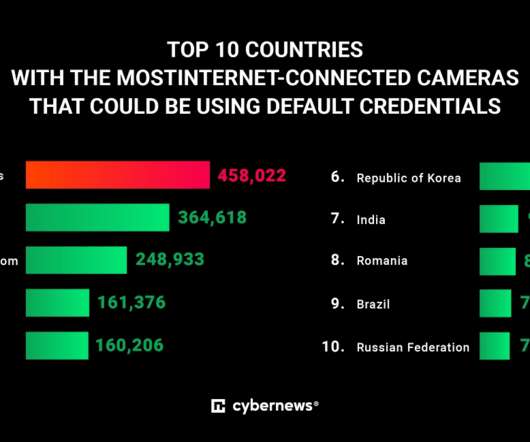
GreyNoise worked with VulnCheck to disclose the two vulnerabilities responsibly. “The vulnerabilities impact NDI-enabled pan-tilt-zoom (PTZ) cameras from multiple manufacturers. Affected devices use VHD PTZ camera firmware < 6.3.40 “Organizations using VHD PTZ camera firmware < 6.3.40




































Let's personalize your content