Your Network Is Showing – Time to Go Stealth
Security Boulevard
APRIL 17, 2025
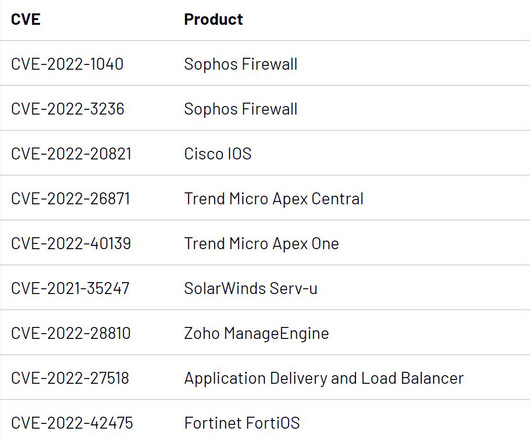
The Old Guard: Firewalls, VPNs and Exposed Control Planes Cyberattacks have evolved beyond the perimeter. No longer limited to opportunistic breaches, attackers are now executing coordinated campaigns that target the very foundations of enterprise network infrastructure firewalls, VPNs, and control planes. The takeaway?






















Let's personalize your content