Mobile World Congress 2025: SOC in the Network Operations Center
Cisco Security
APRIL 3, 2025
Cisco is the sole supplier of network services to Mobile World Congress, expanding into security and observability, with Splunk.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Cisco Security
APRIL 3, 2025
Cisco is the sole supplier of network services to Mobile World Congress, expanding into security and observability, with Splunk.

Security Affairs
APRIL 19, 2025
Threat actors are actively exploiting a remote code execution flaw in SonicWall Secure Mobile Access (SMA) appliances since January 2025. Arctic Wolf researchers warn that threat actors actively exploit a vulnerability, tracked as CVE-2021-20035 (CVSS score of 7.1), in SonicWall Secure Mobile Access (SMA) since at least January 2025.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MAY 16, 2023
Related: The role of legacy security tools Yet the heaviest volume of routine, daily cyber attacks continue to target a very familiar vector: web and mobile apps. A10 has a birds eye view of the flow of maliciousness directed at web and mobile apps — via deployments of its Thunder Application Delivery Controller (ADC.)
Cisco Security
SEPTEMBER 27, 2021
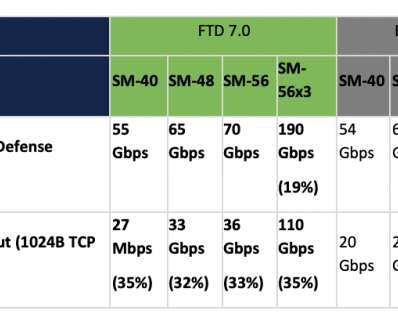
I distinctly remember my desktop and mobile updates that slowed my systems to a crawl. Secure Firewall Threat Defense 7.0 Secure Firewall Threat Defense 7.0 For Cisco Secure Firewall 1000, 2100, 4100 and 9300 series, updating your firewall to Threat Defense 7.0 and Snort 3 : The upgrade you definitely want to make.
Cisco Security
JULY 9, 2021
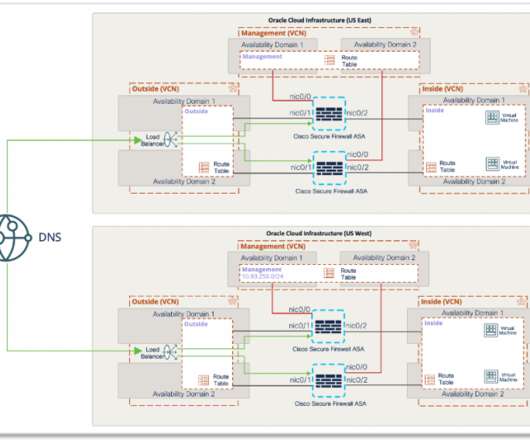
With Cisco Secure Firewall, organizations are able to build a scalable RAVPN architecture on OCI, providing employees secure remote access to their organization’s resources from any location or endpoint. Design 1 – Load balance RAVPN sessions to multiple firewalls using OCI DNS service.

The Last Watchdog
APRIL 29, 2020
It can be argued that we live in a cloud-mobile business environment. Mobile comes into play everywhere. The cloud-mobile environment is here to stay, and it will only get more deeply engrained going forward. LW: You’ve been speaking a lot about the cloud-mobile environment; please explain what you’re referring to.

IT Security Guru
JANUARY 22, 2025
The Evolving Web Landscape Before we dive into the plugins, let’s look at some website basics that are so crucial in 2025: Mobile-First Indexing: Google loves mobile-friendly websites. Equal attention should be given to both desktop and mobile experiences. Your site needs to be responsive and perform well on all devices.

eSecurity Planet
NOVEMBER 1, 2021
Firewalls are as central to IT security as antivirus programs are to PCs, and the multi-billion-dollar market remains large and growing. But the term “firewall” is far too broad to be of much use to IT security buyers. Types of Firewalls. What is a Firewall? Firewalls protect both on-premises and cloud environments.

CyberSecurity Insiders
JULY 19, 2021
As the media around the world is busy speculating about the targets related to Pegasus Mobile Spying malware, Apple Inc, the American company that is into the production of iPhones has issued a press statement that its engineers are working on a fix to protect the users from becoming victims to the said spying Israeli malware.

Cisco Security
JUNE 10, 2021
Today, we are driving simplified security to your hyperconverged infrastructure (HCI), delivering support for Cisco Secure Firewall Threat Defense Virtual (formerly FTDv/NGFWv) on Cisco HyperFlex. Cisco Secure Firewall Threat Defense Virtual for Private Cloud. Support is available now, running on Threat Defense 7.0. Cisco HyperFlex.

The Last Watchdog
MARCH 30, 2020
Here are the key takeaways: Micro-managing workloads Companies today are immersed in digital transformation; they’re migrating to cloud-based business systems, going all in on mobile services and embracing Internet of Things systems whole hog. So we don’t break anything or leave too many things open, like a firewall might do.”

Tech Republic Security
MARCH 10, 2022
Firewalls have been an integral part of the enterprise network architecture. But with the shift to digital business models the once-sturdy firewall has gone from a security staple to a security risk. Read more to learn the five major risks brought on by legacy firewalls in a world of cloud and mobile.

eSecurity Planet
FEBRUARY 6, 2024
A host-based firewall is installed directly on individual networked devices to filter network traffic on a single device by inspecting both incoming and outgoing data. How Host-Based Firewalls Work Organizations often adopt host-based firewalls for device-specific security control.

The Last Watchdog
MAY 9, 2022
Keep your firewall turned on. Software based firewalls are widely recommended for single computers, while hardware firewalls are typically provided with routers for networks. Some operating systems provide native software firewalls (such as Windows OS).

Krebs on Security
AUGUST 3, 2020
A California company that helps telemarketing firms avoid getting sued for violating a federal law that seeks to curb robocalls has leaked the phone numbers, email addresses and passwords of all its customers, as well as the mobile phone numbers and other data on people who have hired lawyers to go after telemarketers.

The Last Watchdog
OCTOBER 16, 2023
Vodnjan, Croatia, October 16, 2023 – Global cloud communications platform Infobip has identified five common frauds impacting mobile users in the messaging ecosystem. Infobip explains the security challenges enterprises and mobile network operators (MNOs) face in the application-to-person (A2P) messaging ecosystem.

eSecurity Planet
AUGUST 29, 2023
Firewall-as-a-Service (FWaaS) offers firewall capabilities as a cloud-based service. Traditional firewalls protect the network perimeter, enforcing security standards by regulating incoming and outgoing traffic according to rules and traffic analysis. Why Is There a Need for FWaaS?

eSecurity Planet
DECEMBER 12, 2022
Team82 researchers have disclosed an attack technique that bypasses industry-leading web application firewalls (WAFs) by appending JSON syntax to SQL injection payloads. The researchers used a WAF shortcoming against the firewalls: Lack of support for native JSON syntax. ” Also read: How to Prevent SQL Injection Attacks.

Security Affairs
DECEMBER 4, 2024
Strong segmentation with firewalls and DMZs, securing VPN gateways, and ensuring encrypted traffic with TLS v1.3 T-Mobile detected recent infiltration attempts but confirmed no unauthorized system access occurred, and no sensitive data was compromised. This is not the case at T-Mobile.” are essential for protecting data.
Krebs on Security
JANUARY 19, 2022
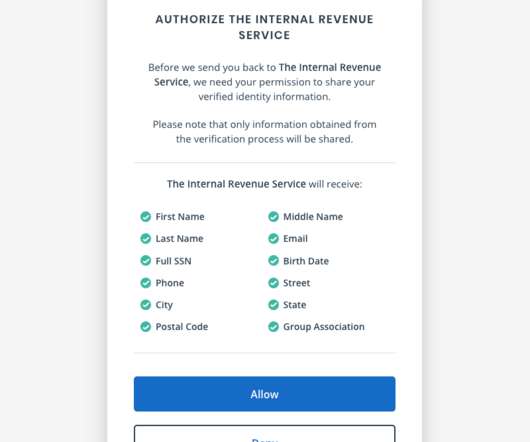
The agency says that by the summer of 2022, the only way to log in to irs.gov will be through ID.me , an online identity verification service that requires applicants to submit copies of bills and identity documents, as well as a live video feed of their faces via a mobile device. The IRS says it will require ID.me McLean, Va.-based

Security Affairs
JANUARY 23, 2021
x and Secure Mobile Access ( SMA ). x and Secure Mobile Access ( SMA ) that are used to provide users with remote access to internal resources.” x (released in 2020) utilized to connect to SMA 100 series appliances and SonicWall firewalls Secure Mobile Access (SMA) version 10.x ” reported TheHackerNews.

Krebs on Security
APRIL 26, 2019
iLnkP2P is designed to allow users of these devices to quickly and easily access them remotely from anywhere in the world, without having to tinker with one’s firewall: Users simply download a mobile app, scan a barcode or enter the six-digit ID stamped onto the bottom of the device, and the P2P software handles the rest.

The Last Watchdog
FEBRUARY 28, 2022
This has resulted in astounding innovations in cloud services, mobile computing, IoT systems and agile software development. Whether it’s IoT (Internet of Things) devices, desktop applications, web applications native to the web browsers, or mobile applications – all these types of software rely on APIs in one way or another.

The Last Watchdog
MARCH 29, 2022
I’m referring to Security Information and Event Management ( SIEM ) systems and to firewalls. Then about five years ago SIEMs got recast as the ideal mechanism for ingesting event log data arriving from Internet traffic, corporate hardware, mobile and IoT devices and cloud-hosted resources — the stuff of digital transformation.
Krebs on Security
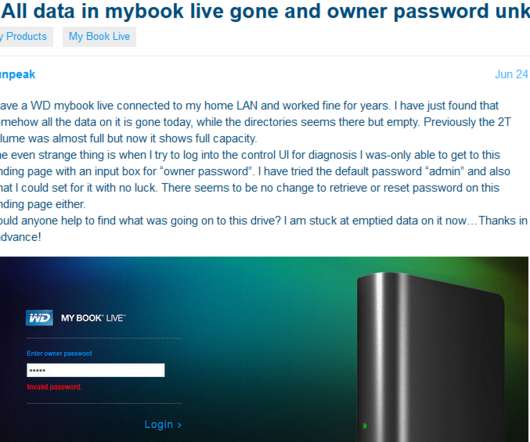
JUNE 25, 2021
We encourage users who wish to continue operating these legacy products to configure their firewall to prevent remote access to these devices, and to take measures to ensure that only trusted devices on the local network have access to the device.” ” A local administration page for the MyBook Live Duo.

Security Affairs
FEBRUARY 15, 2025
CISA adds Apple iOS and iPadOS and Mitel SIP Phones flaws to its Known Exploited Vulnerabilities catalog Attackers exploit recently disclosed Palo Alto Networks PAN-OS firewalls bug U.S. custody in exchange for Marc Fogel North Korea-linked APT Emerald Sleet is using a new tactic U.S.

The Last Watchdog
OCTOBER 25, 2021
Related: T-Mobile breach reflects rising mobile device attacks. Traditional network security solutions, such as firewalls, are not effective at detecting and stopping lateral attack movement – and that’s where the real damage is done. Attackers will get in, it’s only a matter of time.

The Last Watchdog
MAY 19, 2022
Security is also necessary if your retrieval system (such as a website or mobile app) has a paywall or is restricted to only a subset of people, such as customers or resellers. What about public information? Even if you give your content away, you don’t want to allow unauthorized people to add, delete, or tamper with your files. •The

Krebs on Security
NOVEMBER 11, 2019
Multiple firewall products. Mobile payment services. Orvis says the exposure was inadvertent, and that many of the credentials were already expired. Data backup services. Linux servers. Cisco routers. Netflow data. Call recording services. DNS controls. Orvis wireless networks (public and private). Employee wireless phone services.

eSecurity Planet
NOVEMBER 6, 2024
Installing up-to-date firewalls , secure access controls, and intrusion detection systems is a must. By requiring a second form of authentication, such as a code from a mobile device, you can reduce the risk of account compromise to a great extent.

Schneier on Security
JUNE 4, 2019
The period has seen major platform evolution, with the mobile phone replacing the PC and laptop as the consumer terminal of choice, with Android replacing Windows, and with many services moving to the cloud.The use of social networks has become extremely widespread. In this paper,we report what has changed in the seven years since.

The Last Watchdog
DECEMBER 13, 2020
It can also deploy web filtering, threat prevention, DNS security, sandboxing, data loss prevention, next-generation firewall policies, information security and credential theft prevention. . SASE then provides secure connectivity between the cloud and users, much as with a VPN. But it much further. The cyber threats landscape.

CyberSecurity Insiders
NOVEMBER 1, 2021
Develop a mobile device protection strategy. All workers must follow mobile-first security protocols in order to mask their phones, use security applications, and add layers to confidential information. Enact robust data security processes and firewalls.

The Last Watchdog
AUGUST 4, 2021
That said, there is one venerable technology – web application firewalls ( WAFs) – that is emerging as a perfect fit for SMBs in today’s environment, as all companies shift to a deeper reliance on cloud services and mobile apps. Web apps and mobile apps are where they action is. Here are the big takeaways: WAF resurgence.

eSecurity Planet
APRIL 25, 2022
In addition to standard firewalls , features in UTMs often include intrusion detection and prevention systems (IDPS) , secure web gateways , secure email gateways , remote access , routing and WAN connectivity. Some vendors have ditched the UTM label and prefer to call their tools next-generation firewalls (NGFW). URL filtering.
Krebs on Security
FEBRUARY 22, 2024
But Will Thomas , a cyber threat intelligence researcher at Equinix, found an Internet address in the leaked data that corresponds to a domain flagged in a 2019 Citizen Lab report about one-click mobile phone exploits that were being used to target groups in Tibet.

eSecurity Planet
JUNE 23, 2022
FortiGate Network Firewall. Fortinet delivers FortiGate Network Firewalls that are right sized for small businesses to deliver easy-to-use enterprise-level security, good price-to-performance, and offer centralized cloud management that integrates into the larger Fortinet Security Fabric as the business grows. Key Differentiators.

The Last Watchdog
JUNE 22, 2022
However, VPN pipes have become less efficient with the rising use of personally-owed mobile devices increasing reliance on cloud-centric IT resources. In each case, these are usually multifunction devices that function as firewalls, IPS, gateway anti-malware, or content filtering. For SMB you see more SonicWall and Fortinet.

CyberSecurity Insiders
MAY 28, 2023
Research network security mechanisms, such as firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs). Learn about secure coding practices, web application firewalls (WAFs), and vulnerability scanning tools.

Security Affairs
DECEMBER 1, 2024
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

eSecurity Planet
FEBRUARY 4, 2022
Antivirus Software WiFi 6 Routers Virtual Private Networks Password Managers Email Security Software Web Application Firewall Bot Management Software. Also Read: Mobile Malware: Threats and Solutions. Mobile applications. Web Application Firewall (WAF). Key Features of Web App Firewalls. Antivirus Software.

The Last Watchdog
FEBRUARY 18, 2020
It authenticates connections that take place between a smartphone and a mobile app, for instance, as well as between an IoT device and a control server, and even between a microservice and a software container. Sophos’ new XG Firewall is a good start to the improved technologies that are needed.

The Last Watchdog
MAY 24, 2023
It’s not enough to know, for instance, that a user’s mobile phone banking app is calling their bank’s server. We must also authorize that the action the mobile app is doing is allowed on the server. Multi-tier policies Importantly, in addition to these five core principles, 207A introduces the concept of Multi-Tier Policies.

Security Affairs
MARCH 16, 2025
SuperBlack Ransomware operators exploit Fortinet Firewall flaws in recent attacks U.S. New MassJacker clipper targets pirated software seekers Cisco IOS XR flaw allows attackers to crash BGP process on routers LockBit ransomware developer Rostislav Panev was extradited from Israel to the U.S.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content