CISA Order Highlights Persistent Risk at Network Edge
Krebs on Security
JUNE 15, 2023
The directive applies to any networking devices — such as firewalls, routers and load balancers — that allow remote authentication or administration.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Security Boulevard
MAY 6, 2021
The most important and integral part of any data security begins with having firewalls installed in the environment. Not just that, installing firewalls is an essential requirement of the Payment Card Industry Data Security Standard (PCI DSS ). What is a PCI DSS Compliant Firewall? Protect cardholder data with a firewall.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Cisco Security
SEPTEMBER 26, 2022
As Technology Audit Director at Cisco, Jacob Bolotin focuses on assessing Cisco’s technology, business, and strategic risk. Risk Management and Formula One. Meanwhile, InfoSec is the designer and implementor of risk management capabilities (for instance, ensuring the latest technology is deployed and within expected specifications).

eSecurity Planet
OCTOBER 18, 2024
(ISC)2 : This organization offers free self-paced training for a limited time but is more recognized for its high-end Certified Information Systems Security Professional (CISSP) designation, acknowledging your ability to design and monitor a secure system environment, qualifying holders for engineering and executive infosec positions.

Security Boulevard
JULY 9, 2023
Permalink The post BSides Knoxville 2023 – Reanna Schultz – Social Engineering: Training The Human Firewall appeared first on Security Boulevard. Our thanks to BSides Knoxville for publishing their presenter’s outstanding BSides Knoxville 2023 content on the organizations’ YouTube channel.

Cisco Security
AUGUST 26, 2021
We constantly see new threats, and threat vectors, come and go; which puts a tremendous strain on the InfoSec teams that have to protect organizations and businesses from these threats. Cisco Secure Firewall integrations. Cisco Secure Firewall has several new partner integrations. Cisco Secure Firewall version 7.0

CyberSecurity Insiders
JUNE 18, 2022
Last week the infosec community was hit with news about a new Windows 0-day vulnerability, Follina. Therefore, mitigating the risk from this vulnerability requires a comprehensive approach. Prior to Action1, Mike co-founded Netwrix, whose visibility platform for cybersecurity and risk mitigation is helping more than 10,000 customers.

CyberSecurity Insiders
JUNE 16, 2023
They typically safeguard web applications with application security tooling or Web Application Firewalls (WAF). However, sensitive data is transmitted freely across internal and external APIs, increasing the risk of accidental or malicious exposure of different sensitive data types.

eSecurity Planet
MAY 6, 2021
Web application firewalls (WAFs) are a critical component for robust application security. At the same time, WAF technology is increasingly a part of more comprehensive security solutions like next-generation firewalls (NGFW), unified threat management (UTM), and more. Best Web Application Firewalls (WAFs). Amazon Web Services.

Security Affairs
OCTOBER 4, 2020
The vulnerabilities have been reported to HP by the infosec researchers Nick Bloor, an attacker could chain the three issues to achieve SYSTEM privileges on targeted devices and potentially take over them. However, the company provides customers with remediation steps that should at least partially mitigate the security risks.

The Falcon's View
JANUARY 3, 2019
Consider, if you will, that fundamentally we in infosec want people to make better decisions. That's right, it's infosec. From a functional perspective, this means a few very specific things for infosec: 1) We must continue to work in a collaborative and consultative manner with everyone else in the organization.

The Last Watchdog
OCTOBER 31, 2023
The company has been honored by the Cybersecurity Breakthrough Awards, the Globee Information Technology Awards, TMCNet Zero Trust Security Excellence Awards, Cybersecurity Excellence Awards, Fortress Cybersecurity Awards, and the Global InfoSec Innovator award. Media contact: Shannon Cieciuch, Touchdown PR, traceable@touchdownpr.com

CyberSecurity Insiders
SEPTEMBER 21, 2021
Every device you use, the app you download, the bit of information you share, or the message you open comes with a certain amount of risk. Hardening the human firewall. In our digital age, cybersecurity is everyone’s responsibility. Many of the most worrying cyber security vulnerabilities involve human negligence or ignorance.

Herjavec Group
MAY 19, 2022
No matter how many firewalls or network controls you have in place, the risk of insider threat will always be present. I’ve been in infosec for over 30 years and have had the great privilege of evolving and learning as a cybersecurity executive in a space I love.

Herjavec Group
MARCH 24, 2022
Internet-facing architecture that is being ASV scanned has grown more complex over the last years with the implementation of HTTPS load balancers, web application firewalls, deep packet inspection capable intrusion detection/prevention (IDS/IPS) systems, and next-gen firewalls. Ensure that all of the above that do remain in web page *.html

SecureWorld News
OCTOBER 19, 2023
Increased risk of cyberattacks The rising cost of living can lead to an increase in cybercrime, as people become more desperate to make money. Economic effects, including inflationary pressures, have had a broad impact across the InfoSec landscape," Smeaton said. Many are facing multifaceted challenges.

Cisco Security
JANUARY 28, 2021
When boiled down to its essence, InfoSec is all about risk mitigation, and risk is based on probability and impact. If you have a different kind of firewall, if you have a different kind of antivirus, you can get the same intel within the same dashboard. You don’t need to have just Cisco products.
Thales Cloud Protection & Licensing
DECEMBER 13, 2024
Global Infosec Awards At the 2024 RSA Conference, Imperva nabbed an astounding eleven Cyber Defense Magazine Global InfoSec Awards. Global Infosec Awards At the 2024 RSA Conference, Imperva nabbed an astounding eleven Cyber Defense Magazine Global InfoSec Awards. Check out the full report to find out why.

SC Magazine
APRIL 26, 2021
However, such modernization is not without risk. Infosec professionals at the plant must worry about malicious actors potentially sabotaging OT systems using the connected IT systems as an initial vector of compromise. So far, “it’s been going really well,” she said.

Notice Bored
NOVEMBER 14, 2020
A member asked: ‘Should a control be discontinued because a reassessment showed a lower acceptable risk score?’ A dubious firewall rule, for example, might be set to 'warn and log only', rather than simply being dropped from the ruleset, the reverse of how new firewall rules can be introduced. See what you think.

eSecurity Planet
MARCH 31, 2022
Some of the top email protection tools include: Mimecast Secure Email Gateway Barracuda Spam Firewall Proofpoint Enterprise Protection ClearSwift Secure Email Gateway. Phishing simulators give employees a safe space to test their knowledge of phishing attacks without risking personal or company information.

SiteLock
AUGUST 27, 2021
Regardless of whether your website is a personal blog, a small eCommerce site, or a corporate business, you are at risk of a cyber attack. However, you may not be at risk for the reasons you think. Use a malware scanner and web application firewall (WAF). Why WordPress? Why My Website? Once identified, the malware is removed.

SecureList
NOVEMBER 23, 2021
Further evolution of cyberthreats as a response to infosec tools and measures. Cybercriminals will protect themselves better and hedge the risks. Update firewalls and SSL VPN gateways in good time. We can say with high confidence that many of these trends will not only continue, but gain new traction in the coming year.
Security Boulevard
DECEMBER 13, 2024
Global Infosec Awards At the 2024 RSA Conference, Imperva nabbed an astounding eleven Cyber Defense Magazine Global InfoSec Awards. This year, MarCom recognized the success of our Data Threat Report (DTR), which achieved nearly 800 media mentions, 295 million impressions, and more than 5 million in the sales pipeline.

Herjavec Group
AUGUST 2, 2021
He founded Herjavec Group, in 2003, introducing the first managed firewall in the Canadian Market. Along with these contributions, Robert is active in a number of impactful infosec initiatives. This is Cyber Defense Magazine’s third year of honoring global InfoSec innovators with the Black Unicorn Awards. Connect with Robert.

The Security Ledger
SEPTEMBER 25, 2019
» Related Stories Spotlight Podcast: Security Automation is (and isn’t) the Future of Infosec Episode 159: Deep Fakes and Election (in)Security with ZeroFOX Spotlight Podcast: Rethinking Your Third Party Cyber Risk Strategy. Read the whole entry. » grid happened in March of this year.

Thales Cloud Protection & Licensing
SEPTEMBER 25, 2024
With the acquisition, Thales adds Imperva’s partners to its extensive partner ecosystem, expanding its portfolio into data governance, data risk and analytics, and application security. Thales’s primary route to market is with the channel, generating around 85% of its worldwide revenues via partners.

Digital Shadows
OCTOBER 23, 2024
Infosec teams may have a false sense of security when critical servers are equipped with EDR technology and redundant logging. To mitigate this risk, organizations should implement stringent help desk procedures and standard IT interaction processes. The following log shows the shutdown process being initiated on the domain controller.

Security Boulevard
OCTOBER 12, 2021
But there are security principles every development and IT team can follow to reduce the risks of a damaging breach. These machines are usually the heaviest guarded against attacks: they are protected by firewalls and monitored for suspicious activities. This will lower your risks of complete system compromise during an attack.

eSecurity Planet
MAY 5, 2021
BAS offers more than just pen testing and red team insights, going further in recommending and prioritizing fixes to maximize security resources and minimize cyber risk. CyCognito is committed to exposing shadow risk and bringing advanced threats into view. See our in-depth analysis of AttackIQ’s BAS platform. DXC Technology.

Security Boulevard
APRIL 22, 2025
Exploit Chain Targets Unpatched Juniper EX Switches and SRX Firewalls CVE-2023-36845 Juniper Networks Junos OS PHP External Variable Modification Vulnerability 9.8 Security isnt just for infosec professionals its everyones responsibility. CVE-2024-47575 FortiManager Missing Authentication in fgfmsd Vulnerability (FortiJump) 9.8

Security Boulevard
OCTOBER 10, 2022
Reduce the risk of misuse and compromise by the bad guys who use identities in their attacks. Developers want to go incredibly fast and infosec wants to be secure even if it slows down development. Infosec must provide the intellectual property and expertise to accelerate development while securing it. fastsecure.

ForAllSecure
JUNE 2, 2021
With more than 600K followers on YouTube, LiveOverflow is one of infosec’s first social media influencers. In a moment you hear from someone who’s been publishing high quality infosec content on YouTube for the last six years and now has over half a million subscribers. Vamosi: There’s a need for more Infosec content.

ForAllSecure
JUNE 2, 2021
With more than 600K followers on YouTube, LiveOverflow is one of infosec’s first social media influencers. In a moment you hear from someone who’s been publishing high quality infosec content on YouTube for the last six years and now has over half a million subscribers. Vamosi: There’s a need for more Infosec content.

Pentester Academy
FEBRUARY 23, 2023
or sign up for a 7-day, risk-free trial with INE and access this lab and a robust library covering the latest in Cyber Security, Networking, Cloud, and Data Science! or sign up for a 7-day, risk-free trial with INE to access this lab and a robust library covering the latest in Cyber Security, Networking, Cloud, and Data Science!

Digital Shadows
OCTOBER 23, 2024
Infosec teams may have a false sense of security when critical servers are equipped with EDR technology and redundant logging. To mitigate this risk, organizations should implement stringent help desk procedures and standard IT interaction processes. The following log shows the shutdown process being initiated on the domain controller.

ForAllSecure
MARCH 24, 2021
That meant I tested the release candidates -- not the final product you’d buy in the stores - for consumer-grade antivirus programs, desktop firewalls, and desktop Intrusion detection systems. My job as an IT manager is to minimize the risk and put out fires.” Shellshock, as a name, stuck and became the name going forward.

ForAllSecure
MARCH 24, 2021
That meant I tested the release candidates -- not the final product you’d buy in the stores - for consumer-grade antivirus programs, desktop firewalls, and desktop Intrusion detection systems. My job as an IT manager is to minimize the risk and put out fires.” Shellshock, as a name, stuck and became the name going forward.

eSecurity Planet
DECEMBER 3, 2021
How to screen for natural infosec talent: Ask for a worst case scenario for any common situation. Haddix continues to provide his insights while serving as the Head of Security and Risk Management for Ubisoft. Street is an industry-respected speaker and analyst and currently is the VP of InfoSec for SphereNY.
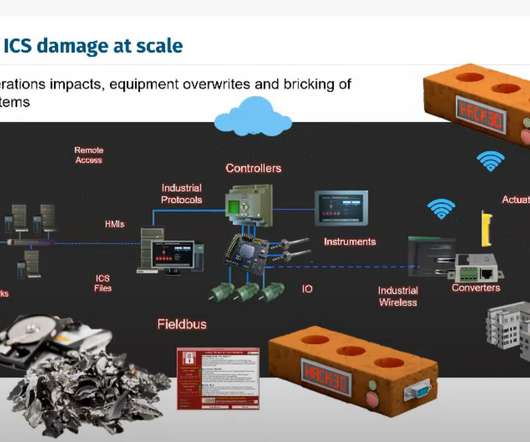
eSecurity Planet
FEBRUARY 25, 2022
Inventory B2B VPNs and block all high-risk protocols (see slide below). Have contingency plans in place for disconnecting all B2B VPNs, especially high-risk ones. Firewalls work both ways. “If my boutique infosec consultancy has these resources…what does a state sponsored one have?”

The Last Watchdog
MARCH 15, 2021
Since we are quickly putting out large technologies, security risks always come with this. Related: Integrating ‘pen tests’ into firewalls. Penetration tests are one way of mitigating the security risks that arise and make sure that we are not endangering users, their data, and the trust they inherently place in technology.

SecureWorld News
JANUARY 11, 2024
Working as CISO, DeSouza's areas of expertise include strategic planning, risk management, identity management, cloud computing, and privacy. While it fosters innovation, automation, and productivity, it simultaneously introduces significant cybersecurity and privacy risks. With the maturation of Zero Trust, propelled by the U.S.
DoublePulsar
DECEMBER 28, 2023
Three of the victims are cybersecurity vendors, and I suspect they may have access to another larger infosec vendor that they haven’t disclosed. So even if you firewall off all incoming network traffic, if outgoing traffic is allowed they can still reach back to the server. Risk assess your MSPs.
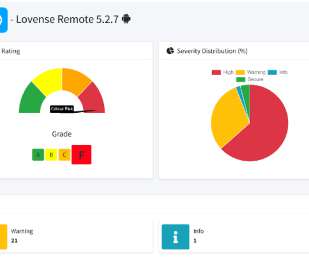
Security Affairs
FEBRUARY 14, 2022
A CyberNews investigation has revealed that Lovense remote sex toy users might be at risk from threat actors, due to poor security features. Lovense uses Cloudflare web application firewall (WAF) and IP proxying tools, meaning that a malicious actor would still have difficulty pinpointing the attack surface. Risk of DoS.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?



Let's personalize your content