Defending your ever-changing attack surface
IT Security Guru
JUNE 17, 2024
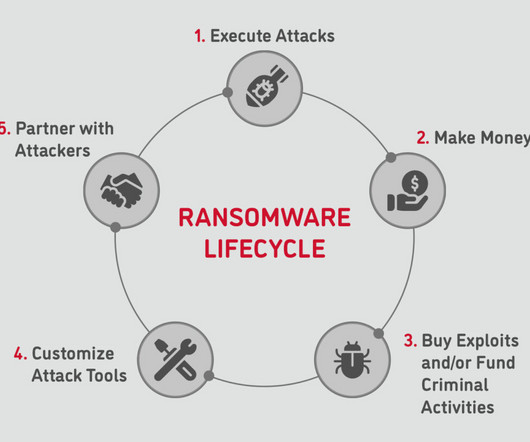
It also includes network vulnerabilities, like open or unprotected ports, unpatched software, and avenues for phishing or social engineering attacks. However, this necessary flexibility may come at the expense of security, in a vertical which is consistently ranked top (or close to top) in terms of the most targeted sectors.














Let's personalize your content