GUEST ESSAY: The Top 5 myths about SIEM –‘security information and event management’
The Last Watchdog
AUGUST 30, 2021
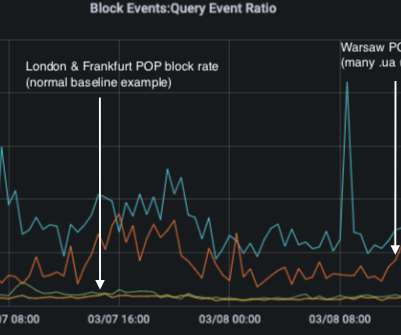
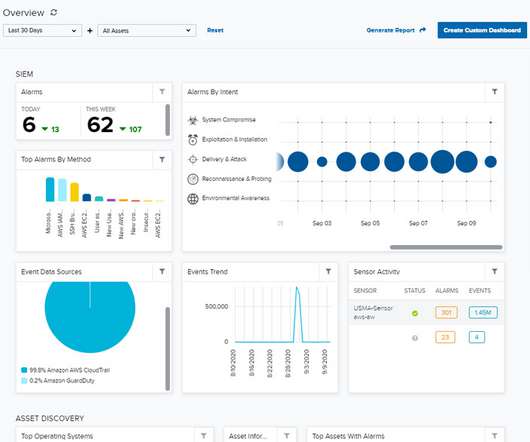
One of the most commonly repeated phrases in the security industry is, “Security teams hate their SIEM!”. Security Information and Event Management (SIEM) is not what it was 20 years ago. Related: The unfolding SIEM renaissance. Don’t get me wrong, SIEMs do take work through deployment, maintenance, and tuning.












































Let's personalize your content