Apple Phone Phishing Scams Getting Better
Krebs on Security
JANUARY 3, 2019
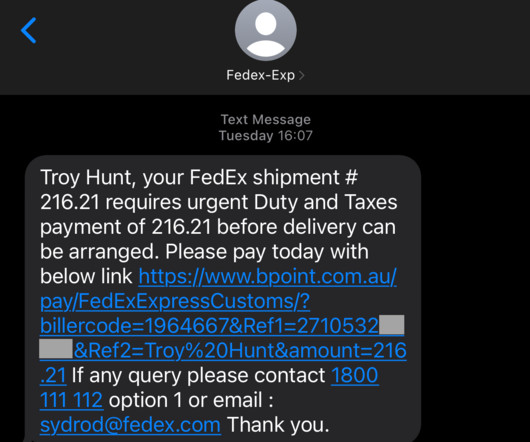
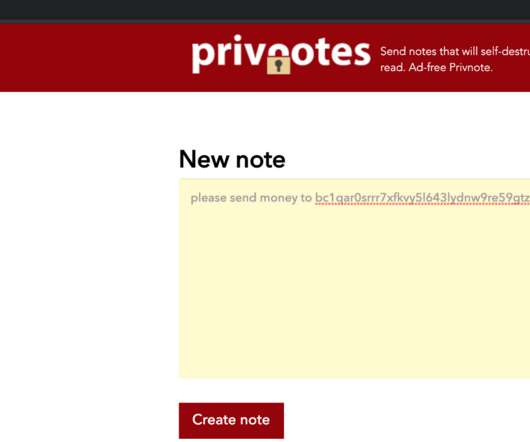
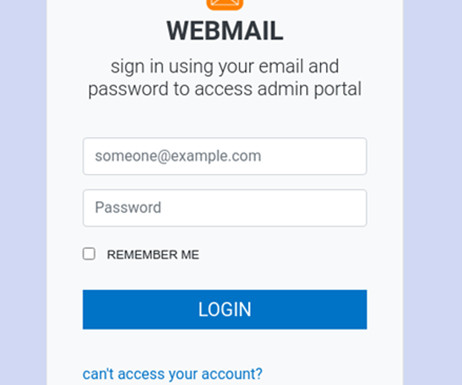
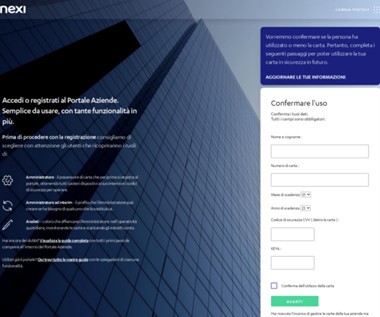
A new phone-based phishing scam that spoofs Apple Inc. 2, 2019: What Westby’s iPhone displayed as the scam caller’s identity. Westby said the Apple agent told her that Apple had not contacted her, that the call was almost certainly a scam, and that Apple would never do that — all of which she already knew.











































Let's personalize your content