CrowdStrike 2024 Global Threat Report: 6 Key Takeaways
Tech Republic Security
FEBRUARY 26, 2024
Identity-based and social engineering attacks still take center stage, according to the CrowdStrike 2024 Global Threat Report.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
FEBRUARY 26, 2024
Identity-based and social engineering attacks still take center stage, according to the CrowdStrike 2024 Global Threat Report.

Security Boulevard
DECEMBER 5, 2024
From phishing schemes and ransomware attacks to social engineering and doxxing, high-net-worth individuals (HNWIs) face an ever-evolving array of cyber threats, and the risks of digital exposure are greater than ever.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureWorld News
JUNE 17, 2024
Ezra Graziano, Director of Federal Accounts at Zimperium, emphasized the urgency for defense against such evolving social engineering tactics. Scams like this will continue with great frequency and success with the weaponization of AI-generated voice, video, and text," warned Patrick Harr, CEO of email security provider SlashNext.

Security Boulevard
MAY 18, 2023
Experts are worried that ChatGPT’s ability to source recent data about an organization could make social engineering and phishing attacks more effective than ever. The post When ChatGPT Goes Phishing appeared first on Security Boulevard.

eSecurity Planet
DECEMBER 10, 2023
The consistent implementation of firewall best practices establish a strong defense against cyber attacks to secure sensitive data, protect the integrity and continuity of business activities, and ensure network security measures function optimally. Why It Matters By restricting access, this strategy mitigates potential damage.
eSecurity Planet
OCTOBER 3, 2022
PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and the muPDF/Subliminal Recording software installer have been backdoored to perform a wide range of social engineering campaigns that started in April 2022. Admins and security teams can use them to assess potential attacks and block inbound traffic from listed IPs.

Security Boulevard
APRIL 8, 2024
A beleaguered health care industry that already is a top target of cybercriminals is under attack again, with bad actors recently using social engineering techniques in calls to IT helpdesks to gain access into the systems of targeted organizations.

eSecurity Planet
MARCH 17, 2023
Whether you’re operating a global enterprise network or a small family business, your network’s security needs to be optimized with tools, teams, and processes to protect customer data and valuable business assets. Many of these tools protect resources connected to networks, thus shutting down threats as early as possible.

Security Boulevard
JANUARY 27, 2023
In this blog post, we will explore both the advantages and dangers of AI in cybersecurity, including examples of how cybercriminals could use AI to improve social engineering attacks and how cybersecurity companies can use AI to better protect users.

SecureList
DECEMBER 9, 2024
This case underscores the serious risk that social engineering and supply chain attacks pose to open-source projects. It emphasizes the importance of implementing stricter security measures, adopting a more vigilant approach to project management, and maintaining careful oversight in regard to projects’ contributors.

The Last Watchdog
MARCH 4, 2024
Nonprofits can bolster their network security by insisting on strong login credentials. Ransomware: This attack involves criminals holding a network and its precious data hostage until the enterprise pays the demanded amount. Strengthen authentication. Lack of proper staff training is the biggest culprit in this case.

CyberSecurity Insiders
MAY 28, 2023
Network Security: Study network protocols, such as TCP/IP, and analyze common network attacks like DDoS, phishing, and man-in-the-middle attacks. Research network security mechanisms, such as firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs).

SecureWorld News
FEBRUARY 10, 2025
The good news is that security teams can learn to anticipate these events and know exactly what to do to stop or prevent them. Why network security matters Before zooming in on specific attack methods, it's important to understand what network security is and why it's a top priority.

SecureWorld News
OCTOBER 13, 2024
Network security Furthermore, Internet of Things (IoT) VR applications , particularly those enhanced by AI, are more resource-intensive. The high bandwidth and low-latency connections of these systems can strain traditional network resources, and as such, security may often not be up to scratch.
eSecurity Planet
FEBRUARY 24, 2022
BeEF , or Browser Exploitation Framework, makes classic tasks such as enumeration, phishing, or social engineering seamless. SET , or Social Engineer Toolkit, focuses on the human factor, as scanners won’t do social engineering pen tests. As many apps are now web-based, adversaries use browser exploitation.

Responsible Cyber
NOVEMBER 23, 2024
The incident revealed that the company’s network security protocols were inadequate, allowing cybercriminals to infiltrate their systems through compromised vendor credentials. As a direct outcome, organizations utilizing this payment processor faced severe reputational damage, and many customers reported fraudulent transactions.

eSecurity Planet
FEBRUARY 21, 2023
Blue teams consist of security analysts, network engineers and system administrators. The team may be divided into sub-teams depending on the type of security controls it is responsible for, such as network security, endpoint security, or the security operations center (SOC).
eSecurity Planet
JUNE 28, 2023
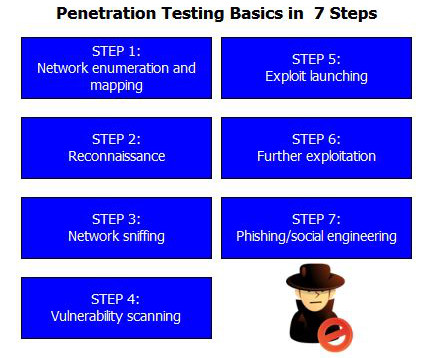
This ensures the entirety of the network and its endpoints are marked for testing and evaluation. Network tests Some organizations differentiate internal from external network security tests. Most cyberattacks today start with social engineering, phishing , or smishing.

CyberSecurity Insiders
JUNE 18, 2022
As more and more businesses increase the number of their digital assets and incorporate new technology to operate, they turn their attack surface into an intricate network. Securing all the systems that include remote employees’ endpoint devices and multi-cloud environments has been a challenge. To Conclude.

Security Boulevard
APRIL 17, 2023
It’s Help|About Time: Chrome’s “V8” JavaScript engine has high-severity vuln. The post Drop Everything: Update Chrome NOW — 0-Day Exploit in Wild appeared first on Security Boulevard. Scrotes already exploiting it.

Security Boulevard
DECEMBER 17, 2021
Researchers have reverse engineered NSO group’s recent zero-click iPhone exploit. The post NSO Zero-Click Exploit: Turing-Complete CPU in Image File appeared first on Security Boulevard. And it’s a doozy.

Security Boulevard
NOVEMBER 25, 2024
During a vishing call, a skilled scammer uses social engineering […] The post Voice Phishing Attacks: How to Prevent and Respond to Them appeared first on CybeReady. The post Voice Phishing Attacks: How to Prevent and Respond to Them appeared first on Security Boulevard.

Security Boulevard
OCTOBER 16, 2024
The post Apple Enrages IT — 45-Day Cert Expiration Fury appeared first on Security Boulevard. CA/B testing: Ludicrous proposal draws ire from “furious” systems administrators.

The Last Watchdog
MARCH 21, 2023
They may incorporate tools such as firewalls or antivirus software , which are helpful, but not the only tactics that can keep a network secure. Unfortunately, having a large cybersecurity budget does not necessarily mean a company has a solid, comprehensive security plan.

Security Boulevard
OCTOBER 25, 2024
The post 100 MILLION Americans in UnitedHealth PII Breach appeared first on Security Boulevard. Not cute: $UNH’s Change Healthcare unit paid a big ransom—its IT was as weak as a kitten.

CyberSecurity Insiders
MAY 18, 2022
Not long ago, it was revealed that T-Mobile had been breached by bad actors who convinced employees to switch their SIM cards to let them bypass two-factor identification — reminding us how effective social engineering can still be. The issue likely comes down to awareness.

Security Boulevard
APRIL 17, 2024
The OpenJS Foundation, which oversees multiple JavaScript projects, thwarted a takeover attempt of at least one project that has echoes of the dangerous backdoor found in versions of the XZ Utils data compression library that failed only because a Microsoft engineer incidentally discovered it.

Security Boulevard
NOVEMBER 1, 2024
Plus brillants exploits: Canadian Centre for Cyber Security fingers Chinese state sponsored hackers. China Hacks Canada too, Says CCCS appeared first on Security Boulevard. The post Ô!

eSecurity Planet
OCTOBER 8, 2024
Unpatched vulnerabilities: In addition, the hackers may have exploited unpatched software or vulnerabilities in network configurations, which are common weak points in large-scale telecom systems. Regular security audits: Regularly assessing network security measures can help identify and address vulnerabilities before they can be exploited.

eSecurity Planet
OCTOBER 13, 2023
BreachLock offers a wide range of services covering cloud , network , application , API , mobile, social engineering and third-party partner tests, and can help with SOC 2, PCI DSS, HIPAA, and ISO 27001 regulatory requirements too. Like BreachLock, ScienceSoft also offers a mix of manual and automated testing.

Security Boulevard
APRIL 3, 2025
The post App Stores OKed VPNs Run by China PLA appeared first on Security Boulevard. Bad Apple: Chinese firm banned by the U.S. is the shady entity behind a clutch of free VPN appswith over a million downloads.

Security Boulevard
JANUARY 24, 2025
The post GhostGPT: A Malicious AI Chatbot for Hackers appeared first on Security Boulevard.

Security Boulevard
DECEMBER 10, 2024
The post Scam Kit Maker Rebuilding Business After Telegram Channel Shut Down appeared first on Security Boulevard.

Security Boulevard
FEBRUARY 7, 2025
FCC Gets Tough on Robocall Fraud appeared first on Security Boulevard. KYC isnt a Thing, claims telco: Commissioner Brendan Carr (pictured) wants $4.5 million fine on Telnyx, for enabling illegal robocall scheme. The post FINALLY!

Security Boulevard
JANUARY 8, 2025
The post Insecure Medical Devices Illumina DNA Sequencer Illuminates Risks appeared first on Security Boulevard. IEI-IEI, Oh: Running an obsolete OS, on obsolete hardware, configured with obsolete settings.

Security Boulevard
DECEMBER 12, 2024
The post AI Slop is Hurting Security LLMs are Dumb and People are Dim appeared first on Security Boulevard. Artificial stupidity: Large language models are terrible if you need reasoning or actual understanding.

Security Boulevard
MARCH 14, 2025
The post Symantec Uses OpenAI Operator to Show Rising Threat of AI Agents appeared first on Security Boulevard. Symantec threat researchers used OpenAI's Operator agent to carry out a phishing attack with little human intervention, illustrating the looming cybersecurity threat AI agents pose as they become more powerful.

Security Boulevard
APRIL 23, 2025
Bacon Redux: Pig butchering and other serious scams still thriving, despite crackdowns in Dubai and Myanmar The post Asian Scam Farms: Industrial Scale, Warns UN Report appeared first on Security Boulevard.

Security Boulevard
DECEMBER 16, 2024
The post Rhode Island Benefits and Services Systems Hit by Ransomware appeared first on Security Boulevard.

The Last Watchdog
FEBRUARY 1, 2021
Here are excerpts of an exchange Last Watchdog had with Harrington about his new book, edited for clarity and length: LW: Why is it smart for companies to make addressing app security a focal point? Harrington: Software runs the world.

Security Boulevard
JANUARY 9, 2025
The post Fortinet CISO Details Phish-Free Phishing Scheme Using PayPal appeared first on Security Boulevard.

Security Boulevard
OCTOBER 30, 2024
The post Proofpoint Boosting Data Security with Normalyze Acquisition appeared first on Security Boulevard.

SecureList
APRIL 21, 2025
Lumma has also been observed using exploit kits, social engineering, and compromised websites to extend its reach and evade detection by security solutions. This communication is typically performed over HTTP or HTTPS, often disguised as legitimate traffic to avoid detection by network security monitoring tools.

eSecurity Planet
DECEMBER 7, 2022
This helps to explain the rise of social engineering attacks , especially with phishing. Earlier this year, Ballistic Ventures invested $7 million in Nudge Security because of its focus on the modern workforce. This startup takes an interesting approach to security. Kubernetes Security and Observability.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content