PseudoManuscrypt: a mass-scale spyware attack campaign
SecureList
DECEMBER 16, 2021
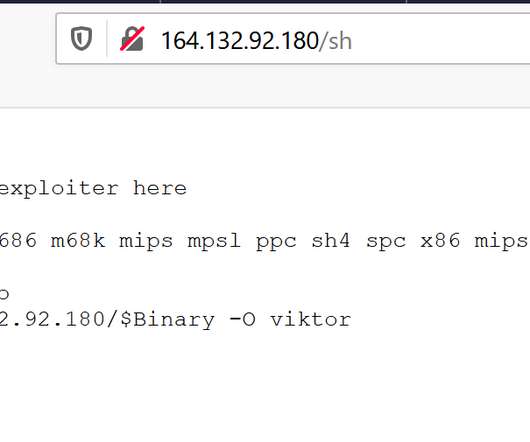
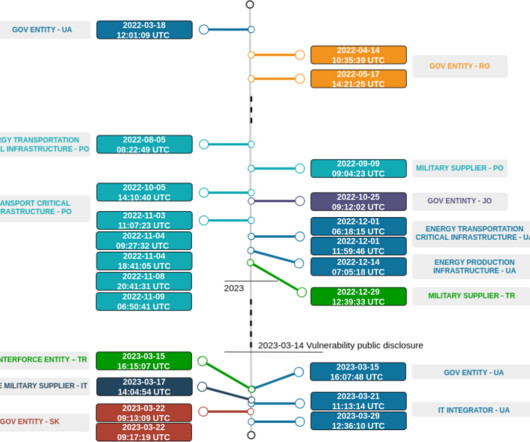
of all computers attacked by the PseudoManuscrypt malware are part of industrial control systems (ICS) used by organizations in various industries, including Engineering, Building Automation, Energy, Manufacturing, Construction, Utilities, and Water Management. According to our telemetry, at least 7.2%













Let's personalize your content