Columbus Ransomware Attack Exposes 500,000+ Residents’ Data: How to Stay Safe
eSecurity Planet
NOVEMBER 6, 2024
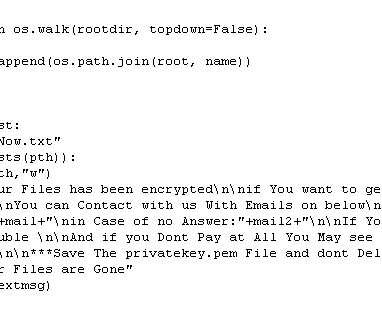
Following a July 18 attack by the Rhysida ransomware group — believed to have Russian affiliations — Columbus is still reeling from the exposure of vast amounts of sensitive resident data. For instance, penetration testing simulates potential attacks, allowing you to assess your response capabilities.
















































Let's personalize your content