Legal Threats Make Powerful Phishing Lures
Krebs on Security
MAY 22, 2019
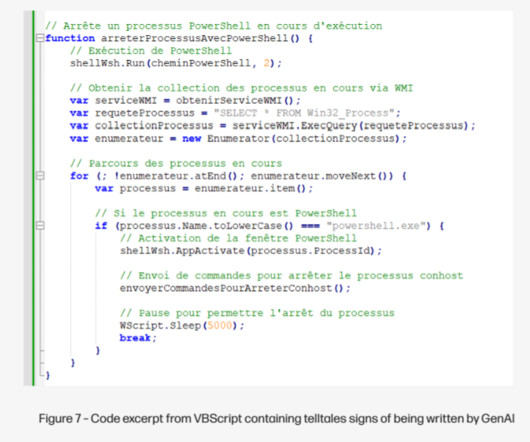
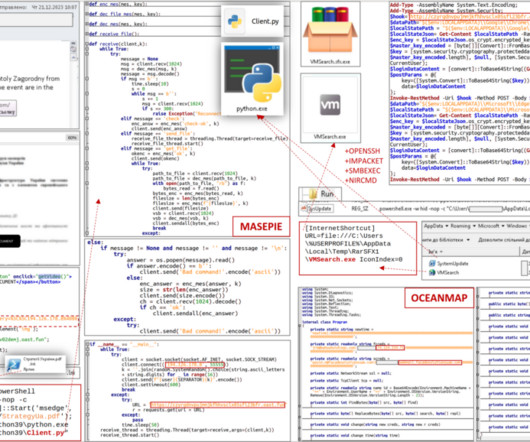
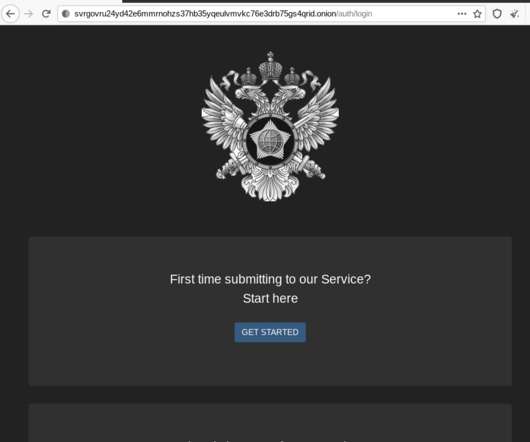
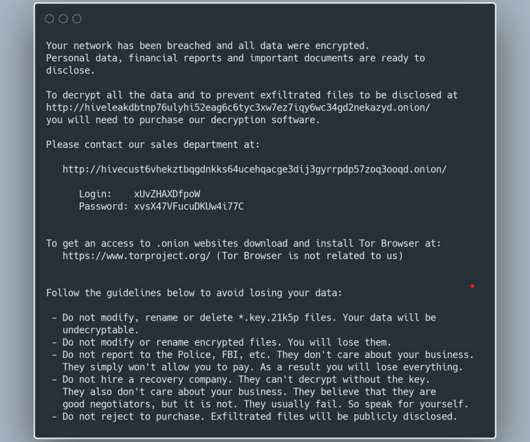
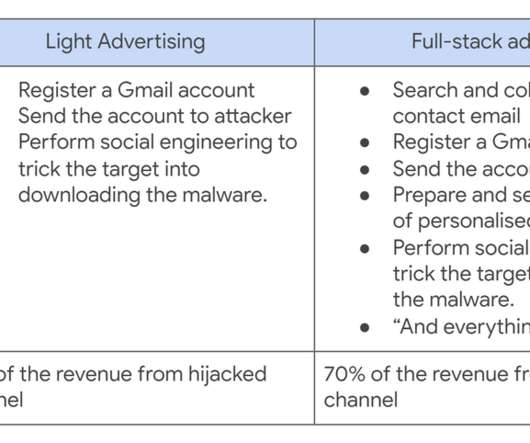
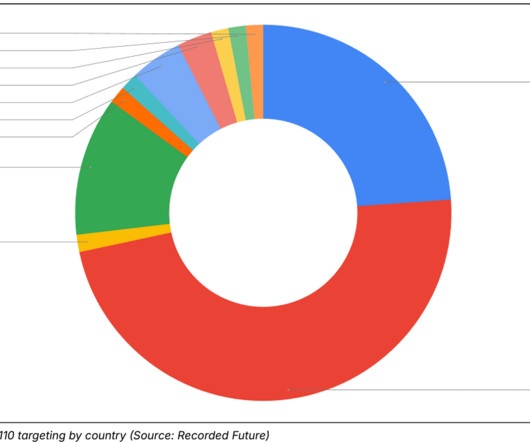
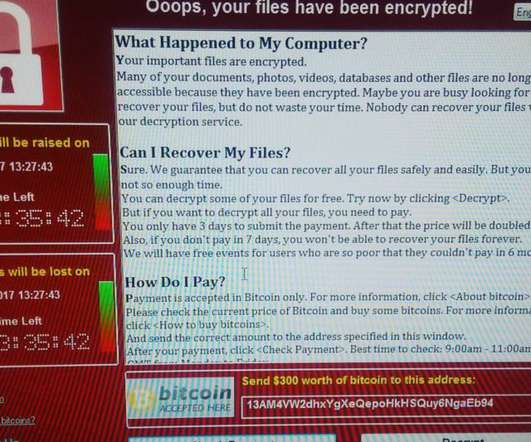
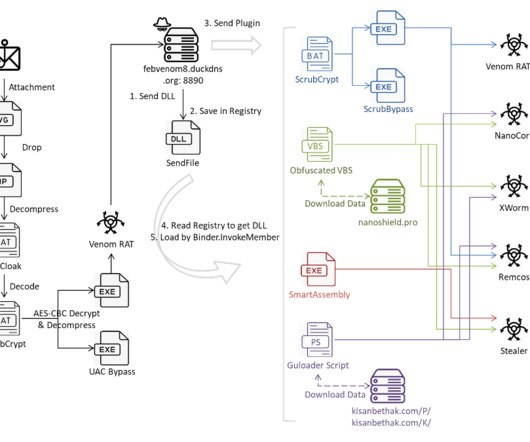
Some of the most convincing email phishing and malware attacks come disguised as nastygrams from a law firm. Here’s a look at a recent spam campaign that peppered more than 100,000 business email addresses with fake legal threats harboring malware. Please download and read the attached encrypted document carefully.




































Let's personalize your content