Zero-day vulnerabilities in Chrome and Android exploited by commercial spyware
Malwarebytes
MAY 24, 2022
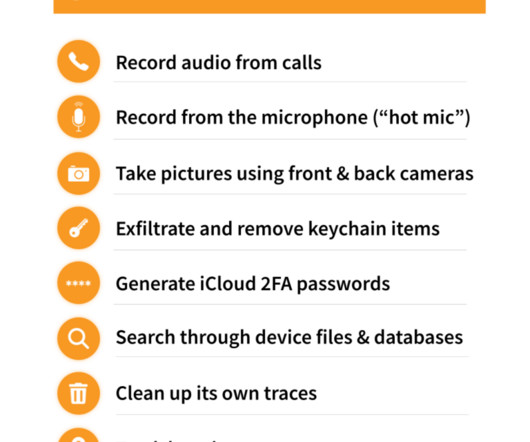
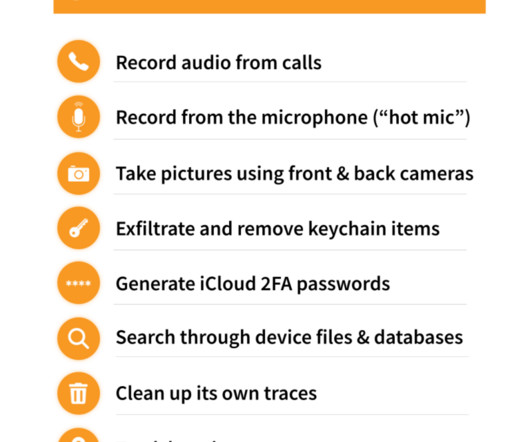
An educated guess, but wrong in this case. The name of the surveillance company—or better said, professional spyware vendor—is Cytrox and the name of its spyware is Predator. In the campaign uncovered by TAG, the spyware vendor used the zero-days in conjunction with other already-patched vulnerabilities.















































Let's personalize your content