6 persuasion tactics used in social engineering attacks
Tech Republic Security
DECEMBER 23, 2020
IT security teams need to educate employees about the psychological techniques cybercriminals often use in social engineering attacks.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
DECEMBER 23, 2020
IT security teams need to educate employees about the psychological techniques cybercriminals often use in social engineering attacks.

Security Through Education
MARCH 3, 2025
When I first heard of social engineering, about 6 years ago, I couldnt define it clearly and concisely if you had offered me millions of dollars. ’ Lets re-visit what social engineering really means, how people use it, and how you can start protecting yourself from it. Either way, lets refresh and learn together!
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Through Education
APRIL 7, 2025
I’ve seen people with disabilities in online discussions and on the Social Engineer Slack channel exploring suitable career paths. The Value of Diversity in Social Engineering Social engineering is, at its core, the art of human connection.

CyberSecurity Insiders
MAY 1, 2023
Social engineering is a term used to describe the manipulation of people into revealing sensitive information or performing actions that they otherwise wouldn’t. Social engineering is an age-old tactic that is often used in phishing attacks. In conclusion, social engineering is a significant threat to cybersecurity.
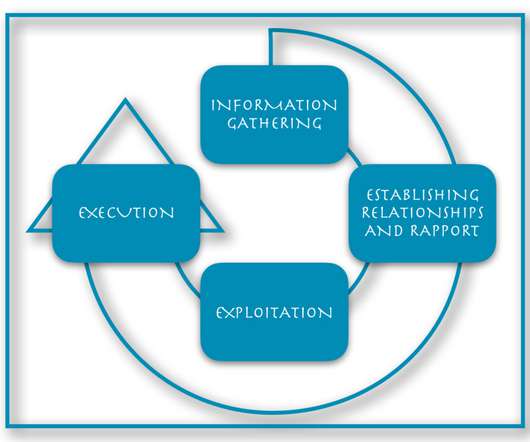
Security Through Education
FEBRUARY 9, 2022
At Social-Engineer, LLC (SECOM), we define social engineering as “any act that influences a person to take an action that may or may not be in their best interest.” If you Google “social engineering,” you will get a very different and more negative definition. Education is Key. Breaking it Down.

The Last Watchdog
MAY 1, 2019
Social engineering, especially phishing, continues to trigger the vast majority of breach attempts. In 2015, penetration tester Oliver Münchow was asked by a Swiss bank to come up with a better way to test and educate bank employees so that passwords never left the network perimeter. Talk more soon.

Security Through Education
FEBRUARY 20, 2024
In the ever-evolving landscape of cybersecurity, social engineering has undergone significant transformations over the years, propelled by advancements in technology. This article delves into the historical shifts in social engineering tactics and explores how adversaries embrace new technologies to achieve their objectives.

Security Through Education
NOVEMBER 4, 2024
Let me tell you about possibly my favorite onsite social engineering team engagement I have ever done! So, before we start, what exactly is tribe mentality, and why is it important to social engineering ? So, before we start, what exactly is tribe mentality, and why is it important to social engineering ?

Security Through Education
MARCH 9, 2022
As social engineers, we may wear different hats (sometimes literally) when it comes to getting into character for our pretexts. The first live APSE (Advance Practical Social Engineering) class in two years! We also wear different “hats” in relation to roles within our company. We start week one with a bang.

Security Affairs
FEBRUARY 20, 2023
Social engineering techniques are becoming increasingly sophisticated and are exploiting multiple emerging means, such as deep fakes. Education improves awareness” is his slogan. Deepfake technology, what’s it? He is also the author of the book “La Gestione della Cyber Security nella Pubblica Amministrazione”.

Dark Reading
FEBRUARY 27, 2023
Build a playbook for employees on how to handle suspicious communications, use mail filters, and screen and verify unfamiliar calls to bolster a defensive social engineering security strategy.

Security Through Education
APRIL 5, 2023
When I first started in the social engineering field, I had no idea how much it would impact my everyday life. What exactly is social engineering? Social Engineering: What is it? What is social engineering ? What is social engineering ? Why Should I Care About Social Engineering?

Dark Reading
SEPTEMBER 16, 2022
As digital applications proliferate, educating users against social engineering attempts is a key part of a strong defense. Be wary of being pestered into making a bad decision.

SecureWorld News
SEPTEMBER 17, 2022
According to this cyber wonderkid, they used social engineering to pull off the hack. This incident is yet another example of how easy it is for malicious threat actors to use social engineering to gain access to an organization's internal systems. They are openly taunting and mocking @Uber. September 16, 2022.

Security Through Education
JUNE 21, 2023
Social engineering is defined as influencing someone to take an action that may or may not be in a person’s best interest. Written by: Rosa Rowles At Social Engineer LLC, our purpose is to bring education and awareness to all users of technology. The amygdala “hijacks” the frontal lobe.

Malwarebytes
MAY 1, 2023
Both Staffin and his employer were victims of business email compromise (BEC) , also known as CEO fraud, a type of social engineering attack. Social engineering attacks are cyberattacks where a criminal tricks a victim into doing something against their interests, such as revealing sensitive information of making a bank transfer.

SecureWorld News
OCTOBER 3, 2023
And one of the most successful and increasingly prevalent ways of attack has come from social engineering, which is when criminals manipulate humans directly to gain access to confidential information. Social engineering is more sophisticated than ever, and its most advanced iteration is the topic of today's discussion: deepfakes.

The Last Watchdog
NOVEMBER 11, 2024
Quite like how pilots use AR simulation in training, cybersecurity professionals can use AR-enabled training simulations that immerse them in hyper-realistic scenarios, offering hands-on cyber defense training and education. One significant risk is the potential for the technology to become a host to sophisticated social engineering attacks.

SecureWorld News
FEBRUARY 15, 2024
The hackers rely heavily on social engineering tactics to distribute the malware. Education on verifying app downloads, MFA, advanced threat detection, encrypted communications, and tighter mobile device management controls can all contribute to protecting users.

SecureWorld News
FEBRUARY 13, 2025
Evolution of social engineering Social engineering exploits human psychology to manipulate individuals into revealing sensitive information or taking harmful actions. Deepfakes are revolutionizing social engineering attacks, making them more deceptive and harder to detect.

Security Boulevard
JULY 9, 2023
Permalink The post BSides Knoxville 2023 – Reanna Schultz – Social Engineering: Training The Human Firewall appeared first on Security Boulevard. Our thanks to BSides Knoxville for publishing their presenter’s outstanding BSides Knoxville 2023 content on the organizations’ YouTube channel.

Adam Levin
AUGUST 26, 2020
Schools and companies should consider the following: Set up accounts with competing services: While Zoom holds a dominant position, it is by no means the only video conferencing platform for meetings or for education. If your school or educator hasn’t provided these, check online for one of several free resources for education. .
Krebs on Security
FEBRUARY 26, 2023
GoDaddy described the incident at the time in general terms as a social engineering attack, but one of its customers affected by that March 2020 breach actually spoke to one of the hackers involved. But we do know the March 2020 attack was precipitated by a spear-phishing attack against a GoDaddy employee.

SecureWorld News
JANUARY 22, 2025
Additionally, these conventional tools lack the contextual awareness needed to identify sophisticated social engineering tactics employed by AI-powered phishing campaigns. Traditional security measures struggle to keep pace with the rapid evolution of AI-driven threats, often relying on outdated signature-based detection methods.

eSecurity Planet
OCTOBER 22, 2024
Cybercriminals employ social engineering techniques to trick you into believing you must resolve fictitious technical issues. The hallmark of ClickFix campaigns is their clever use of social engineering. Adjust security settings: Use the security features provided by your video conferencing platform.

eSecurity Planet
APRIL 8, 2025
Xanthorox reasoner advanced mimics human reasoning, helping attackers craft more believable phishing messages or manipulate targets through social engineering. Generative AI tools are being used increasingly for good, from writing code to helping with education. ” How are security teams responding?

The Last Watchdog
NOVEMBER 19, 2023
Using routine social engineering strategies, the cyber-thieves gathered information about key employees. Professional networking and social media platforms continue to prove a rich landscape for phone numbers, locations, hobbies, dates of birth, family members, and friendships.

IT Security Guru
FEBRUARY 25, 2025
Other Ways Threat Actors Exploit Human Behaviour In addition to fatigue attacks, malefactors weaponise social engineering. MFA fatigue is often coupled with social engineeringan attacker might contact the victim, masquerading as IT support, and advise them to approve the prompt to “resolve an issue.”

Hacker's King
DECEMBER 26, 2024
Educate Yourself on Social Engineering Tactics Hacking isnt always about code; social engineeringmanipulating users into sharing sensitive informationis one of the most effective tools for cybercriminals. Common Social Engineering Techniques: Fake messages from accounts posing as Instagram support.

Webroot
JANUARY 19, 2022
Through a series of effective delivery modules, SAT provides employees with relevant information and knowledge on topics like social engineering, malware, compliance and information security. Whether you’re an enterprise, SMB or MSP, make security awareness training part of your regular cyber education routine.

Krebs on Security
NOVEMBER 21, 2020
In response to questions from KrebsOnSecurity, GoDaddy acknowledged that “a small number” of customer domain names had been modified after a “limited” number of GoDaddy employees fell for a social engineering scam. GoDaddy said the outage between 7:00 p.m. and 11:00 p.m. PST on Nov.

Security Boulevard
JULY 10, 2024
Google and Apple look to give users better protections against social engineering attacks like phishing, with Google giving high-risk users access to the APP service with a passkey and Apple educating users about the threats with a detailed support document in the wake of a recent smishing campaign.

Security Boulevard
SEPTEMBER 16, 2024
As digital exploitation, fraud and deception move deeper into society, it is incumbent on organizations to educate their employees on digital literacy skills, make them aware of the risks posed by phishing and social engineering threats.

SecureList
FEBRUARY 27, 2024
” For instance, educational robots that connect to the internet and support video calls. Subject of the study: educational robot The toy is designed to educate and entertain children; it is an interactive device running the Android operating system. In other words, this is a “tablet on wheels.”

NetSpi Executives
OCTOBER 15, 2024
TL;DR Don’t wait for a breach to happen before you pursue social engineering testing. Get the most value out of your social engineering testing by asking the questions below to maximize results. 73% of Breaches Are Due to Phishing and Pretexting Social engineering remains a prevalent threat.

SecureWorld News
FEBRUARY 5, 2025
Ransomware and state-sponsored attacks continue to escalate Canada's critical sectorsincluding healthcare, energy, education, and retailhave become prime targets for cybercriminals. Education: Budget constraints make institutions a low-hanging fruit for cybercriminals. Key findings: the cyber threat landscape in 2025 1.

eSecurity Planet
FEBRUARY 26, 2025
Strengthening mobile security also requires enforcing strict access controls to limit exposure and continuously educating employees on the latest social engineering tactics. As cybercriminals refine their methods, companies that fail to adapt risk being the next target.
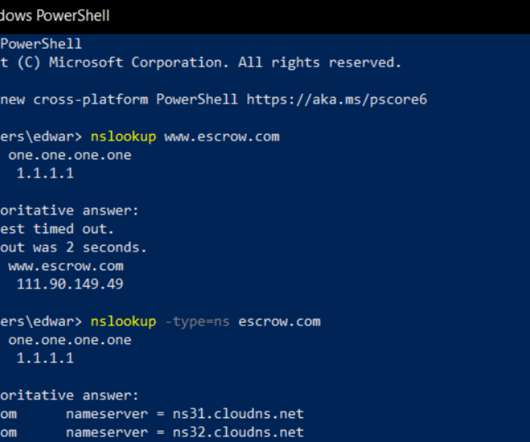
Krebs on Security
MARCH 31, 2020
The employee involved in this incident fell victim to a spear-fishing or social engineering attack. We have taken steps across our technology, processes and employee education, to help prevent these types of attacks in the future.” Nation-state level attackers also are taking a similar approach.

Malwarebytes
MARCH 19, 2025
Additional social engineering techniques Phishing emails and messages : Scammers send convincing emails or text messages that appear to be from legitimate government agencies or financial institutions, urging users to click on malicious links or provide personal information. on unverified websites.

The Last Watchdog
JANUARY 2, 2024
Lack of security awareness and education. Often, employees within organizations lack sufficient security awareness and education. This lack of knowledge makes them susceptible to phishing attacks, social engineering, and other cyber threats. Promote security awareness and education among employees.

Security Boulevard
MARCH 17, 2025
In reality, many of the most successful breaches stem from simple tactics like phishing emails, social engineering, and exploiting basic security misconfigurations. Human error and susceptibility to social engineering tactics continue to be significant vulnerabilities in cybersecurity, accounting for a majority of compromises.

SecureWorld News
DECEMBER 17, 2024
This operation, which blends social engineering and technical exploitation, has resulted in the theft of more than 390,000 WordPress credentials. Educate Security Teams : Train red teams and researchers to recognize phishing attempts, especially those exploiting operational needs like kernel upgrades.

Security Through Education
NOVEMBER 19, 2024
Social engineering scams frequently exploit our desire to help by using themes of sympathy and assistance to manipulate us. Sympathy and Assistance Themes in Vishing Simulations Now you might be wondering, do these social-engineering tactics actually work?

Security Through Education
NOVEMBER 19, 2024
Social engineering scams frequently exploit our desire to help by using themes of sympathy and assistance to manipulate us. Sympathy and Assistance Themes in Vishing Simulations Now you might be wondering, do these social-engineering tactics actually work?
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content