Storm-1977 targets education sector with password spraying, Microsoft warns
Security Affairs
APRIL 27, 2025
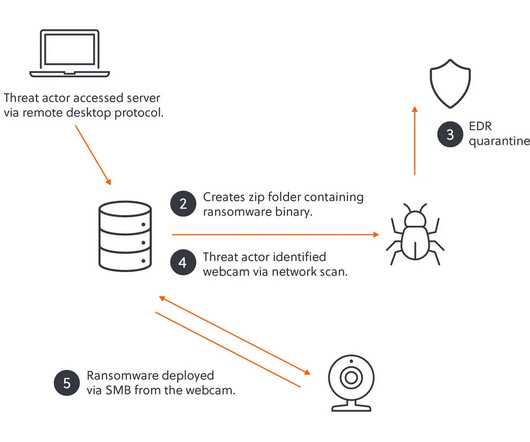
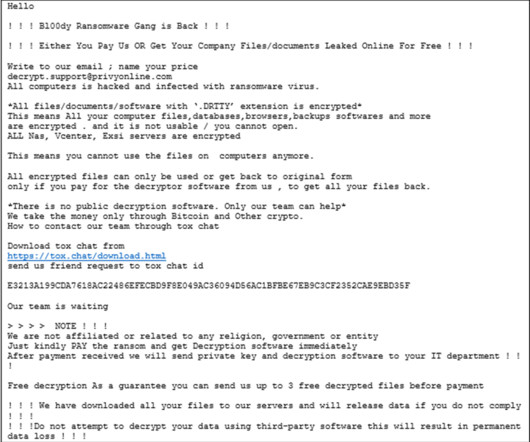
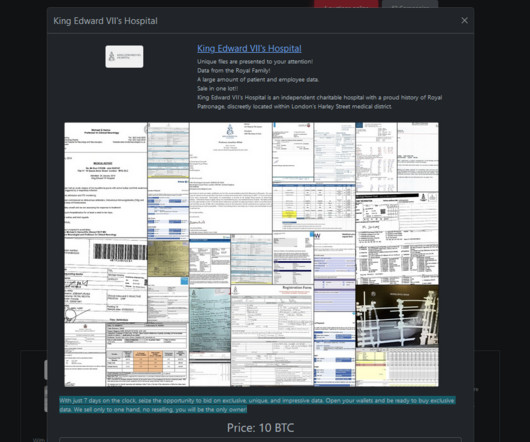
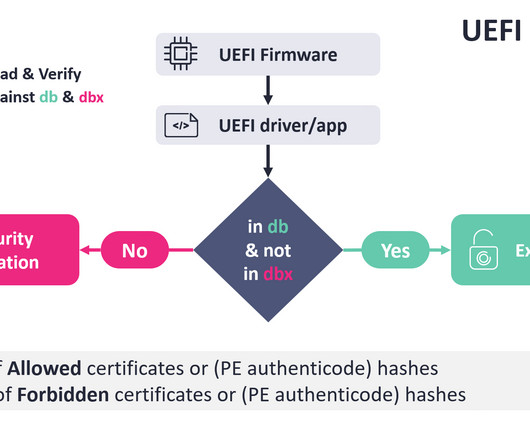
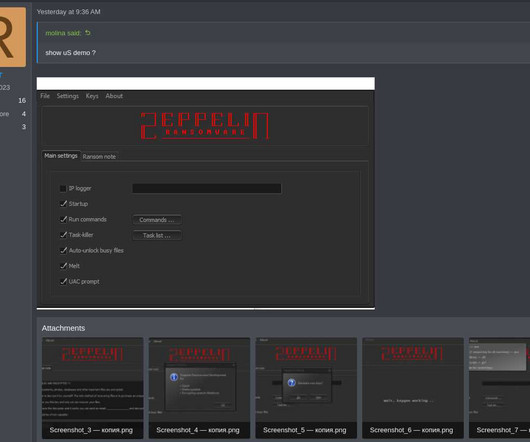
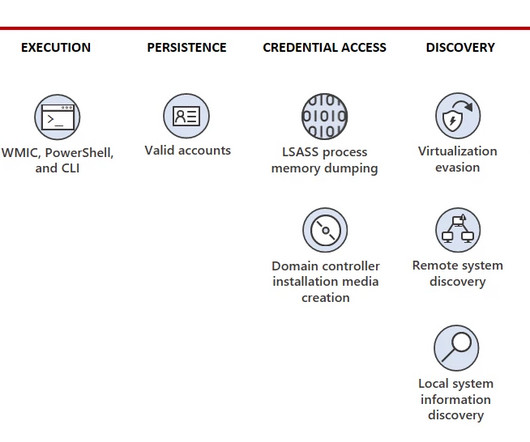
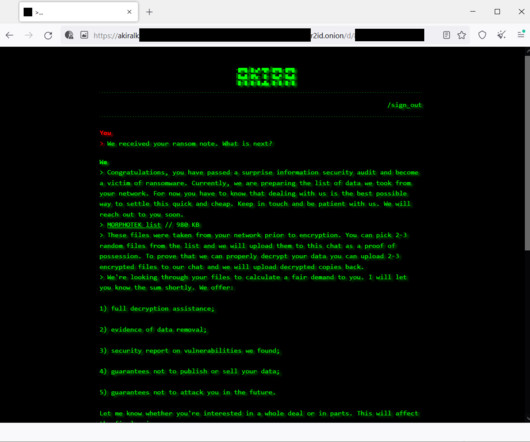
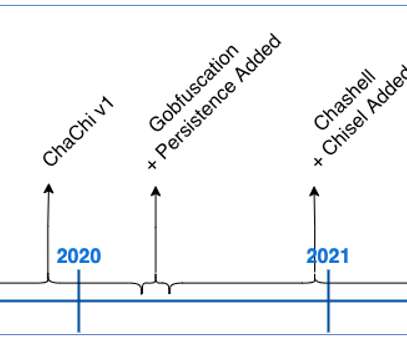
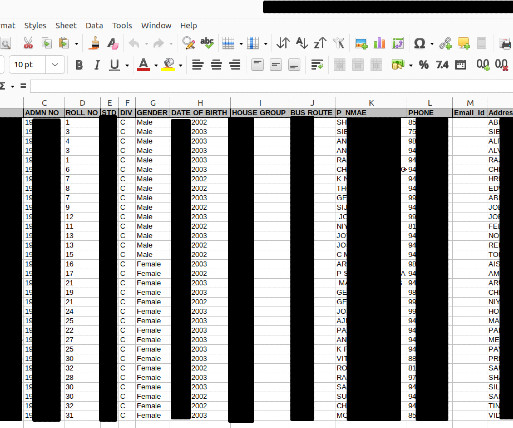
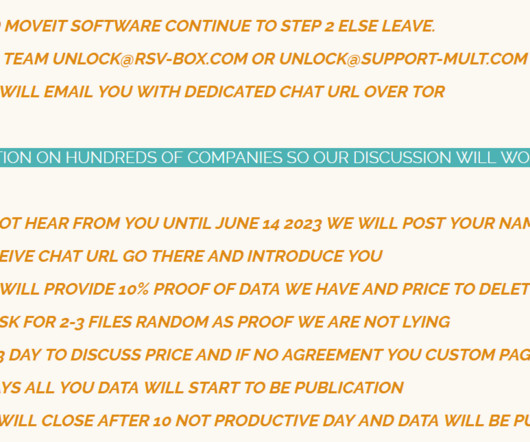
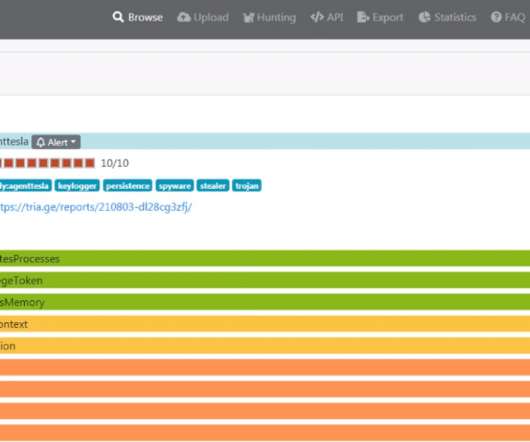
Microsoft warns that threat actor Storm-1977 is behind password spraying attacksagainst cloud tenants in the education sector. Over the past year, Microsoft Threat Intelligence researchers observed a threat actor, tracked as Storm-1977, using AzureChecker.exe to launch password spray attacks against cloud tenants in the education sector.




































Let's personalize your content