Excellent Write-up of the SolarWinds Security Breach
Schneier on Security
AUGUST 30, 2021
Robert Chesney wrote up the Solar Winds story as a case study, and it’s a really good summary.

Schneier on Security
AUGUST 30, 2021
Robert Chesney wrote up the Solar Winds story as a case study, and it’s a really good summary.

Krebs on Security
SEPTEMBER 2, 2021
Some of the most successful and lucrative online scams employ a “low-and-slow” approach — avoiding detection or interference from researchers and law enforcement agencies by stealing small bits of cash from many people over an extended period. Here’s the story of a cybercrime group that compromises up to 100,000 email inboxes per day, and apparently does little else with this access except siphon gift card and customer loyalty program data that can be resold online.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Anton on Security
AUGUST 30, 2021
As you are reading our recent paper “Autonomic Security Operations?—?10X Transformation of the Security Operations Center” , some of you may think “Hey, marketing inserted that 10X thing in there.” Well, 10X thinking is, in fact, an ancient tradition here at Google. We think that it is definitely possible to apply “10X thinking” to many areas of security (at the same link , they say that sometimes it is “easier to make something 10 times better than it is to make it 10 percent better” ).

Troy Hunt
SEPTEMBER 3, 2021
I'm back from the most epic of holidays! How epic? Just have a scroll through the thread: I’m back! Went offline for most of the last week, pics and stories to follow 🐊 pic.twitter.com/hRUcKMwgGU — Troy Hunt (@troyhunt) September 2, 2021 Which the Twitter client on my iPad somehow decided to break into 2 threads: At times this felt like navigating through a scene from Jurassic Park, just with wallabies rather than velociraptors 🦖 pic.twitter.com/VHa4kJw6k

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Schneier on Security
SEPTEMBER 1, 2021
Citizen Lab is reporting on two zero-click iMessage exploits, in spyware sold by the cyberweapons arms manufacturer NSO Group to the Bahraini government. These are particularly scary exploits, since they don’t require to victim to do anything, like click on a link or open a file. The victim receives a text message, and then they are hacked. More on this here.

Krebs on Security
SEPTEMBER 1, 2021
Over the past 15 years, a cybercrime anonymity service known as VIP72 has enabled countless fraudsters to mask their true location online by routing their traffic through millions of malware-infected systems. But roughly two weeks ago, VIP72’s online storefront — which ironically enough has remained at the same U.S.-based Internet address for more than a decade — simply vanished.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Last Watchdog
AUGUST 30, 2021
One of the most commonly repeated phrases in the security industry is, “Security teams hate their SIEM!”. Related: The unfolding SIEM renaissance. Security Information and Event Management (SIEM) is not what it was 20 years ago. Don’t get me wrong, SIEMs do take work through deployment, maintenance, and tuning. They also require strategic planning. Yet, much to the chagrin of everyone who believed the vendor hype, they fail to provide the “single pane of glass” for all tasks in security operatio

Schneier on Security
SEPTEMBER 3, 2021
Black Hat is a hacker-themed board game.

Tech Republic Security
SEPTEMBER 3, 2021
Cybersecurity training is not the same across all companies; SMB training programs must be tailored according to size and security awareness. Here are an expert's cybersecurity training tips.

Anton on Security
SEPTEMBER 3, 2021
As you recall from “Anton and The Great XDR Debate, Part 1” , there are several conflicting definitions of XDR today. As you also recall, I never really voted for any of the choices in the post. While some of you dismiss XDR as the work of excessively excitable marketing people (hey … some vendor launched “XDR prevention ”, no way, right?), perhaps there is a way to think about it from a different perspective.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

SecureList
SEPTEMBER 2, 2021
Main description. QakBot, also known as QBot, QuackBot and Pinkslipbot, is a banking Trojan that has existed for over a decade. It was found in the wild in 2007 and since then it has been continually maintained and developed. In recent years, QakBot has become one of the leading banking Trojans around the globe. Its main purpose is to steal banking credentials (e.g., logins, passwords, etc.), though it has also acquired functionality allowing it to spy on financial operations, spread itself, and

Schneier on Security
SEPTEMBER 3, 2021
Jon D. Paul has written the fascinating story of the HX-63, a super-complicated electromechanical rotor cipher machine made by Crypto AG.

Tech Republic Security
AUGUST 31, 2021
Authentication sans password is already possible and solutions are on the market from companies like Ping Identity. With passwords passé, it's time to make the leap to better security.

Bleeping Computer
SEPTEMBER 1, 2021
Juliana Barile, the former employee of a New York credit union, pleaded guilty to accessing the financial institution's computer systems without authorization and destroying over 21 gigabytes of data in revenge. [.].

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Trend Micro
SEPTEMBER 2, 2021
We take a closer look at the SSL/TLS certificates used by malware.

Schneier on Security
AUGUST 31, 2021
Late last year, the NSA declassified and released a redacted version of Lambros D. Callimahos’s Military Cryptanalytics, Part III. We just got most of the index. It’s hard to believe that there are any real secrets left in this 44-year-old volume.

Tech Republic Security
SEPTEMBER 3, 2021
Fail2ban should be on every one of your Linux servers. If you've yet to install it on either Rocky Linux or AlmaLinux, Jack Wallen is here to help you out with that.

We Live Security
AUGUST 31, 2021
ESET's cybersecurity expert Marc-Étienne Léveillé analyses in-depth the Quebec's vaccine proof apps VaxiCode and VaxiCode Verif. The post Flaw in the Quebec vaccine passport: analysis appeared first on WeLiveSecurity.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Boulevard
AUGUST 31, 2021
Microsoft Windows 11 won’t auto-update on slightly old PCs. It appears this includes security updates. The post Windows 11 Security Scare—MS Nixes Fixes on Older PCs appeared first on Security Boulevard.

Zero Day
SEPTEMBER 3, 2021
The watchdog alleges the app "helped stalkers steal private information.

Tech Republic Security
AUGUST 31, 2021
Identity and access management is pushing application security past single-factor authentication (a password) and even multi-factor authentication to a risk management model says Ping Identity CEO.

CSO Magazine
AUGUST 30, 2021
Enterprise-class password managers have become one of the easiest and most cost-effective ways to help employees lock down their online accounts. Most of the options were originally designed for individual users. Your organizational needs will differ wildly from security-conscious personal users, but the good news is that the key password management players all have made their solutions suitable for the business world. [ Learn 12 tips for effectively presenting cybersecurity to the board and 6 s

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Cisco Security
AUGUST 31, 2021
In my first nearly 90 days since joining Cisco , I’ve spoken with customers from around the world. And one thing that I continue to hear? The shift to a more distributed workforce is driving the need for anywhere, anytime access to resources, wherever they exist. Prior to 2020, many treated “digital transformation” as merely a buzzword — a low priority, at best.

We Live Security
SEPTEMBER 3, 2021
Smartphones are kids’ trusty companions both in- and outside the classroom, and as they return to their desks, we’ve prepared some handy tips on how to keep their devices secure. The post A parent’s guide to smartphone security appeared first on WeLiveSecurity.

Tech Republic Security
AUGUST 31, 2021
Soft skills are just as important, if not more so, than technical skills in cybersecurity professionals. People with soft skills can be trained in tech skills, expert says.

The Hacker News
SEPTEMBER 2, 2021
Microsoft's Active Directory is said to be used by 95% of Fortune 500. As a result, it is a prime target for attackers as they look to gain access to credentials in the organization, as compromised credentials provide one of the easiest ways for hackers to access your data. A key authentication technology that underpins Microsoft Active Directory is Kerberos.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
CSO Magazine
SEPTEMBER 2, 2021
Cybersecurity has steadily crept up the agenda of governments across the globe. This has led to initiatives designed to address cybersecurity issues that threaten individuals and organizations. “Government-led cybersecurity initiatives are critical to addressing cybersecurity issues such as destructive attacks, massive data breaches, poor security posture, and attacks on critical infrastructure,” Steve Turner, security and risk analyst at Forrester, tells CSO.

Malwarebytes
SEPTEMBER 3, 2021
It’s a good idea to try and keep certain things private. For example, people have been using anonymous email services for years. These either hide your real email address, or replace it entirely for specific tasks. Folks will go one step further, setting aliases for each service they sign up to. If the mail ends up in the wild? They know there’s a good chance which service has suddenly experienced a breach.

Tech Republic Security
SEPTEMBER 2, 2021
The Labor Day holiday could be prime time for more than just barbecues and closing the pool for the year as the open season on ransomware continues.
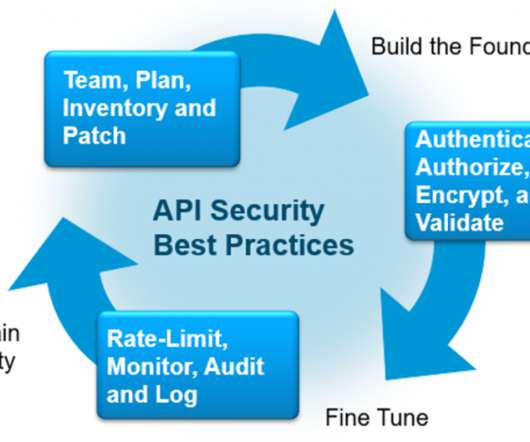
Cisco Security
AUGUST 30, 2021
Recently one of the big-three consumer credit bureaus fixed an issue that allowed an ordinary user to obtain the credit score of tens of millions of Americans just by providing their name and mailing address. The connective tissue making this data exposure possible was an Application Programming Interface or API. An API enables two pieces of software to communicate with each other.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
Let's personalize your content