Pwned Passwords Adds NTLM Support to the Firehose
Troy Hunt
FEBRUARY 9, 2023
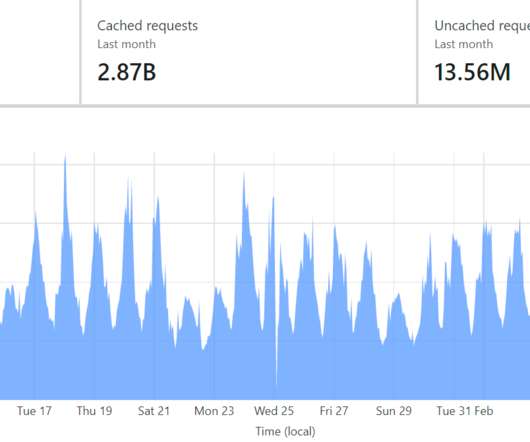
I think I've pretty much captured it all in the title of this post but as of about a day ago, Pwned Passwords now has full parity between the SHA-1 hashes that have been there since day 1 and NTLM hashes. We always had both as a downloadable corpus but as of just over a year ago with the introduction of the FBI data feed , we stopped maintaining downloadable behemoths of data.























Let's personalize your content