Inside the Cit0Day Breach Collection
Troy Hunt
NOVEMBER 19, 2020
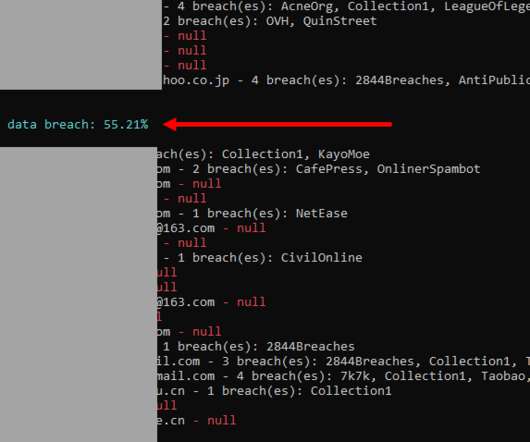
It's increasingly hard to know what to do with data like that from Cit0Day. If that's an unfamiliar name to you, start with Catalin Cimpanu's story on the demise of the service followed by the subsequent leaking of the data. The hard bit for me is figuring out whether it's pwn-worthy enough to justify loading it into Have I Been Pwned (HIBP) or if it's just more noise that ultimately doesn't really help people make informed decisions about their security posture.







































Let's personalize your content