Massive Brazilian Data Breach
Schneier on Security
JANUARY 26, 2021
I think this is the largest data breach of all time: 220 million people. ( Lots more stories are in Portuguese.).

Schneier on Security
JANUARY 26, 2021
I think this is the largest data breach of all time: 220 million people. ( Lots more stories are in Portuguese.).
Daniel Miessler
JANUARY 25, 2021
There are recon tools, and there are recon tools. @tomnomnom —also called Tom Hudson—creates the latter. I have great respect for large, multi-use suites like Burp , Amass , and Spiderfoot , but I love tools with the Unix philosophy of doing one specific thing really well. I think this granular approach is especially useful in recon. Related Talk: Mechanizing the Methodology.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Joseph Steinberg
JANUARY 25, 2021
Long-time cybersecurity-industry veteran, Joseph Steinberg , has been appointed by CompTIA, the information technology (IT) industry’s nonprofit trade association that has issued more than 2-million vendor-neutral IT certifications to date, to its newly-formed Cybersecurity Advisory Council. The council, comprised of 16 experts with a diverse set of experience and backgrounds, will provide guidance on how technology companies can both address pressing cybersecurity issues and threats, as well as

Krebs on Security
JANUARY 29, 2021
The unprecedented volume of unemployment insurance fraud witnessed in 2020 hasn’t abated, although news coverage of the issue has largely been pushed off the front pages by other events. But the ID theft problem is coming to the fore once again: Countless Americans will soon be receiving notices from state regulators saying they owe thousands of dollars in taxes on benefits they never received last year.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Schneier on Security
JANUARY 27, 2021
Insider data theft : Dutch police have arrested two individuals on Friday for allegedly selling data from the Dutch health ministry’s COVID-19 systems on the criminal underground. […]. According to Verlaan, the two suspects worked in DDG call centers, where they had access to official Dutch government COVID-19 systems and databases. They were working from home: “Because people are working from home, they can easily take photos of their screens.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Joseph Steinberg
JANUARY 28, 2021
Hands-free car-entry systems that allow people to unlock their car doors without the need to push any buttons on the fob or car provide great convenience; at least during the winter, many people even store key fobs in their coats and do not even physically handle the fobs on a regular basis. Cars that allow such access typically utilize proximity to determine when to let people open their doors; when a corresponding fob (and, ostensibly the car’s owner) is close to a locked vehicle that ve

Schneier on Security
JANUARY 29, 2021
Apple has added added security features to mitigate the risk of zero-click iMessage attacks. Apple did not document the changes but Groß said he fiddled around with the newest iOS 14 and found that Apple shipped a “significant refactoring of iMessage processing” that severely cripples the usual ways exploits are chained together for zero-click attacks.

Troy Hunt
JANUARY 25, 2021
I had this idea out of nowhere the other day that I should have a visual display somewhere in my office showing how many active Have I Been Pwned (HIBP) subscribers I presently have. Why? I'm not sure exactly, it just seemed like a good idea at the time. Perhaps in this era of remoteness I just wanted something a little more. present. More tangible than occasionally running a SQL query.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Last Watchdog
JANUARY 25, 2021
SolarWinds and Mimecast are long-established, well-respected B2B suppliers of essential business software embedded far-and-wide in company networks. Related: Digital certificates destined to play key role in securing DX. Thanks to a couple of milestone hacks disclosed at the close of 2020 and start of 2021, they will forever be associated with putting supply-chain vulnerabilities on the map.

Schneier on Security
JANUARY 29, 2021
This essay makes the point that actual computer hackers would be a useful addition to NATO wargames: The international information security community is filled with smart people who are not in a military structure, many of whom would be excited to pose as independent actors in any upcoming wargames. Including them would increase the reality of the game and the skills of the soldiers building and training on these networks.

Adam Shostack
JANUARY 28, 2021
For Data Breach Today, I spoke with Anna Delaney about threat modeling for issues that are in the news right now: “Does your organization have a plan in place if one of your employees is accused via Twitter of being an insurrectionist? If your software was being used to spread plans for a riot, could you detect that? Threat modeling expert Adam Shostack discusses how companies should be prepared to respond to issues in the news.” Threat Modeling for Social Issues.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Tech Republic Security
JANUARY 29, 2021
By knowing the different types of data, it can help your company protect itself from breaches and better recover from a cyberattack.

Schneier on Security
JANUARY 28, 2021
A coordinated effort has captured the command-and-control servers of the Emotet botnet: Emotet establishes a backdoor onto Windows computer systems via automated phishing emails that distribute Word documents compromised with malware. Subjects of emails and documents in Emotet campaigns are regularly altered to provide the best chance of luring victims into opening emails and installing malware regular themes include invoices, shipping notices and information about COVID-19.

Zero Day
JANUARY 29, 2021
FonixCrypter gang claimed it shut down and deleted their ransomware's source code.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Tech Republic Security
JANUARY 25, 2021
A Gartner report predicts that the second-order consequences of widespread AI will have massive societal impacts, to the point of making us unsure if and when we can trust our own eyes.

Graham Cluley
JANUARY 28, 2021
Law enforcement agencies across the globe say that they have dealt a blow against Emotet, described by Interpol as "the world's most dangerous malware", by taking control of its infrastructure. Read more in my article on the Tripwire State of Security blog.

Zero Day
JANUARY 29, 2021
After the discovery of NAT Slipstreaming 2.0 attack this week, Google says it will block Chrome traffic on ports 69, 137, 161, 1719, 1720, 1723, 6566, and 10080.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
JANUARY 27, 2021
Active accounts for people who have left your organization are ripe for exploitation, according to Sophos.
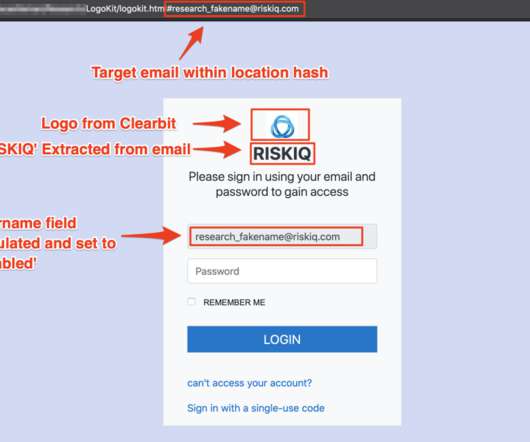
Security Affairs
JANUARY 28, 2021
Researchers from RiskIQ have discovered a new phishing kit dubbed LogoKit that dynamically compose phishing content. Researchers from RiskIQ discovered a new phishing kit that outstands for its ability to dynamically create phishing messages to target specific users. LogoKit has a modular structure that makes it easy to implement a phishing-as-as-Service model.

Zero Day
JANUARY 28, 2021
Security firm Clearsky said they identified at least 250 servers hacked by Lebanese Cedar, a hacking group linked to the Hezbollah militant group.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Tech Republic Security
JANUARY 29, 2021
This comprehensive guide covers different types of denial of service attacks, DDoS protection strategies, as well as why it matters for business.

Graham Cluley
JANUARY 27, 2021
Apple is encouraging owners of iPhones and iPads to update their devices to the latest version of iOS and iPadOS in order to protect against serious vulnerabilities that could have already been actively exploited by malicious hackers.

Zero Day
JANUARY 28, 2021
Pretending to be someone you’re not online could, one day, land you in hot water.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
Let's personalize your content