Cameras that Automatically Detect Mobile Phone Use
Schneier on Security
DECEMBER 2, 2019
New South Wales is implementing a camera system that automatically detects when a driver is using a mobile phone.

Schneier on Security
DECEMBER 2, 2019
New South Wales is implementing a camera system that automatically detects when a driver is using a mobile phone.

Troy Hunt
DECEMBER 1, 2019
It's summer! Yes, I know it's back to front for many of you but Dec 1 means it's sunnier than ever here. Regardless, this week I've been at DDD in Brisbane, written my 10 year old son Ari and I running kids coding clubs in Oslo (cold) and London (rainy) next month and the Swiss gov being on-boarded onto HIBP. Plus there's this week's sponsor IVPN and how tracking ain't tracking (that may be a bit of an old Aussieism ).
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
DECEMBER 4, 2019
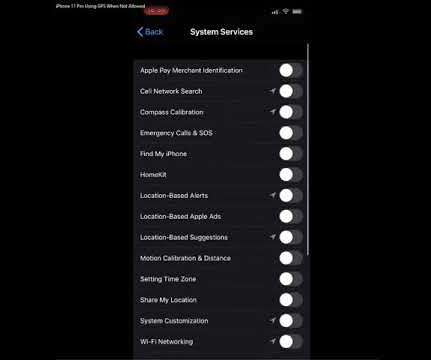
One of the more curious behaviors of Apple’s new iPhone 11 Pro is that it intermittently seeks the user’s location information even when all applications and system services on the phone are individually set to never request this data. Apple says this is by design, but that response seems at odds with the company’s own privacy policy.

The Last Watchdog
DECEMBER 5, 2019
I’m privileged to share news that two Last Watchdog articles were recognized in the 2019 Information Management Today MVP Awards. My primer on the going forward privacy and security implications of IoT — What Everyone Should Know About the Promise and Pitfalls of the Internet of Things — won second place in the contest’s IoT Security category.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Schneier on Security
DECEMBER 3, 2019
This just in : We are pleased to announce the factorization of RSA-240, from RSA's challenge list, and the computation of a discrete logarithm of the same size (795 bits): RSA-240 = 12462036678171878406583504460810659043482037465167880575481878888328 966680118821085503603957027250874750986476843845862105486553797025393057189121 768431828636284694840530161441643046806687569941524699318570418303051254959437 1372159029236099 = 509435952285839914555051023580843714132648382024111473186660296521821206

Tech Republic Security
DECEMBER 4, 2019
After a number of devastating breaches and hacks, the sheer size of data lost is no longer the only indicator of severity.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Affairs
DECEMBER 1, 2019
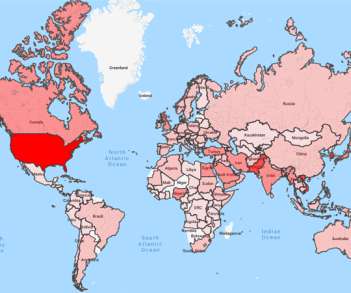
Google revealed that over 12,000 of its users were targeted by state-sponsored hackers in the third quarter of this year. Google’s Threat Analysis Group (TAG) revealed that it has detected and blocked attacks carried out by nation-state actors on 12,000 of its users in the third quarter of this year. Over 90 percent of the users identified by Google were targeted via “credential phishing emails” that attempt to trick victims into providing their password or other account credentials to hij

Schneier on Security
DECEMBER 6, 2019
Andy Ellis, the CSO of Akamai, gave a great talk about the psychology of risk at the Business of Software conference this year. I've written about this before. One quote: "The problem is our brains are intuitively suited to the sorts of risk management decisions endemic to living in small family groups in the East African highlands in 100,000 BC, and not to living in the New York City of 2008.".

Tech Republic Security
DECEMBER 3, 2019
Labeled "StrandHogg," the vulnerability discovered by the mobile security vendor Promon could give hackers access to users' photos, contacts, phone logs, and more.

The Last Watchdog
DECEMBER 6, 2019
In 2019, we’ve seen a surge in domain name service (DNS) hijacking attempts and have relayed warnings from the U.S. Cybersecurity and Infrastructure Agency, U.K.’s Cybersecurity Centre, ICANN, and other notable security experts. Although, the topic has gained popularity amongst CIOs and CISOs, most companies are still overlooking important security blind spots when it comes to securing their digital assets outside the enterprise firewalls—domains, DNS, digital certificates.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
Security Affairs
DECEMBER 2, 2019
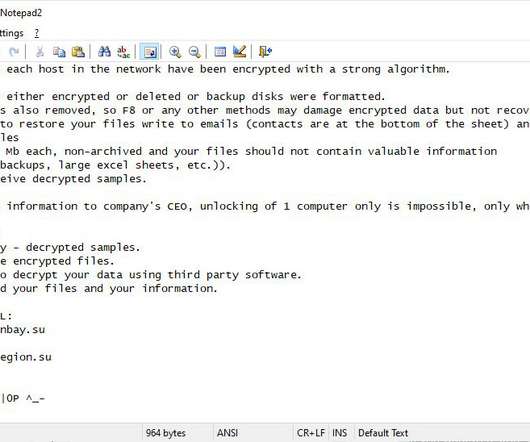
Experts discovered a new malware dubbed Clop ransomware that attempts to remove Malwarebytes and other security products. Security researcher Vitali Kremez discovered a new malware dubbed Clop ransomware that targets Windows systems and attempts to disable security products running on the infected systems. The malicious code executes a small program, just before starting the encryption process, to disable security tools running on the infected systems that could detect its operations.

Schneier on Security
DECEMBER 4, 2019
Carolyn McCarthy gave an excellent TEDx talk about becoming a tech policy activist. It's a powerful call for public-interest technologists.

Tech Republic Security
DECEMBER 5, 2019
Learn how iCloud Keychain can help you keep track of your app and website passwords.

Adam Shostack
NOVEMBER 30, 2019
For 51 years, the gallant people of Gavle, Sweden, have been putting up a straw goat, and arsonists have been burning it. Apparently, they didn’t have Twitter back then, and needed alternate ways to get into flame wars. Previously: Gavle Goat at Shostack & Friends.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Affairs
DECEMBER 1, 2019
Millions of SMS messages have been leaked by a database run by TrueDialog, a business SMS provider for businesses and higher education providers. Security experts at vpnMentor discovered a database belonging to the US communications company, TrueDialog that was leaking millions of SMS messages. Most of the SMS included in the database were sent by businesses to potential customers.

Schneier on Security
DECEMBER 3, 2019
The New Yorker has published the long and interesting story of the cybersecurity firm Tiversa. Watching "60 Minutes," Boback saw a remarkable new business angle. Here was a multibillion-dollar industry with a near-existential problem and no clear solution. He did not know it then, but, as he turned the opportunity over in his mind, he was setting in motion a sequence of events that would earn him millions of dollars, friendships with business élites, prime-time media attention, and respect in Co

Tech Republic Security
DECEMBER 5, 2019
More than a third of systems that handle biometric data were hit by at least one malware infection in the third quarter of 2019, according to a new Kaspersky report.

WIRED Threat Level
DECEMBER 1, 2019
Once you realize most things you search for online are boring and obvious, you realize you don't really need Google in your life. .

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Affairs
NOVEMBER 30, 2019
Security experts discovered an Android banking Trojan, dubbed Ginp, that steals both login credentials and credit card data. Security experts at ThreatFabric discovered an Android banking Trojan, dubbed Ginp, that steals both login credentials and credit card data. Ginp was first spotted in October by Kaspersky while targeting Spain and UK, but researchers believe it has been active around since June.
Thales Cloud Protection & Licensing
DECEMBER 3, 2019
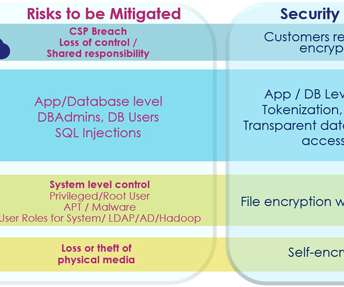
With more and more organizations embracing digital transformation and accelerating their pace to digitize every piece of information, they become increasingly vulnerable to sophisticated cyber-attacks and data breaches. As highlighted in the 2019 Thales Data Threat Report , an increasing number of organizations across the globe are now using sensitive data on digitally transformative technologies like cloud, virtualization, big data, IoT, blockchain, etc. that further increases their exposure to

Tech Republic Security
DECEMBER 6, 2019
Security experts say most voting machines are safe and secure, but disinformation campaigns on platforms like Facebook and Twitter need to be addressed.

Adam Shostack
DECEMBER 2, 2019
Over the years, a number of people set up Feedburner accounts to proxy RSS from our blogs into their system. I generally have no issue with people reading how they choose, but I cannot provide support or management. Google is end of lifing the old Feedburner, and for those of you reading via Feedburner RSS, I humbly ask that you update to [link] or [link] (with comments).

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Affairs
DECEMBER 1, 2019
The online music streaming service Mixcloud was recently breached by a hacker that is attempting to sell stolen user data a dark web marketplace. On Friday, the hacker that goes online with the handle “A_W_S” contacted multiple media outlets to disclose the hack, it also provided data samples as proof of the data breach. The hack took place in early November and exposed data for more than 20 million user accounts.

Daniel Miessler
DECEMBER 1, 2019
[advanced_iframe src=”[link] width=”100%”] No related posts.

Tech Republic Security
DECEMBER 4, 2019
Common sense and a careful backup plan are just a couple of the ways to be prepared for online and traditional dangers during the season.

Adam Shostack
DECEMBER 1, 2019
Cyber. The Huawei and Snowden Questions , by Olav Lysne is a deep dive into what happens when an untrusted vendor builds your trusted computing base, and more importantly, why a great many of the “obvious” ways to address those risks are subject to easy work-arounds. This is unhappy news for Huawei, but more importantly, as cyber is now treated as a “fifth domain” and there are no norms of conflict, bad news for technology in general.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Security Affairs
DECEMBER 1, 2019
The official Twitter account of Huawei Mobile Brazil has been hacked and attackers have sent offensive messages to the rival Apple. The official Twitter account of Huawei Mobile Brazil has been hacked, attackers have sent offensive messages to provoke the rival Apple. The hack took place on Black Friday in Brazil, but at the time of writing the tweets have been already removed.

WIRED Threat Level
DECEMBER 4, 2019
Hate them or love them, the Ewoks have more strategic chops than any military in the Star Wars galaxy.

Tech Republic Security
DECEMBER 4, 2019
With an average of 11 connected devices in US households, consumers are ready for faster and more reliable 5G networks.

Thales Cloud Protection & Licensing
DECEMBER 4, 2019
It’s speculated that $10 million is still unaccounted for from one of the most lucrative robberies in U.S. history. The 1997 Dunbar Armored truck depot heist netted $18.9 million when six aspiring conspirators executed a well-laid plan that included deep insider knowledge and hoax alibis. While this event is still considered one of the most grandiose thefts, financial institutions today collectively face digital attacks that easily rival it.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
Let's personalize your content